Top 15 Okta Alternatives and Competitors in 2025
Looking for Okta alternatives in 2025? Explore the top 10+ Okta competitors for identity and access management (IAM). Compare features, pricing, and integrations to find the best fit for your organization.


Okta has long been a leader in identity and access management (IAM), offering secure authentication and lifecycle management across modern IT environments. However, as organizations scale, many seek alternatives that offer greater flexibility, pricing transparency, and deeper integration with existing tech stacks.
In this guide, we’ll explore the top Okta alternatives and competitors in 2025, analyze what makes each platform unique, and help you identify the right fit for your business needs. Whether you’re prioritizing compliance, reducing costs, or modernizing access management, these solutions offer diverse options for secure, scalable identity control.
Why Companies Look for Okta Alternatives
As identity and access management (IAM) becomes central to enterprise security, organizations are reassessing their reliance on legacy providers like Okta. While Okta remains a well-established platform, many IT and security leaders are exploring alternatives that offer greater flexibility, cost efficiency, and support for evolving hybrid and multi-cloud environments. Below are three common drivers behind the shift:
- High Total Cost of Ownership
- Complexity and Setup Challenges
- Integration and Ecosystem Limitations
High Total Cost of Ownership
For many organizations, Okta’s pricing model presents a major barrier to scalability. The platform’s tiered pricing and minimum user commitments can lead to steep costs, especially for small and mid-sized businesses (SMBs) or organizations with fluctuating workforce sizes. Beyond licensing, costs often extend to professional services, premium support, and integration overhead; expenses that accumulate quickly as teams expand their application ecosystems.
This high total cost of ownership makes it difficult for companies to balance IAM performance with budget constraints. Mid-market enterprises, in particular, struggle to justify ongoing spend when newer competitors offer modular pricing models or pay-as-you-grow flexibility. As a result, many are transitioning to alternative IAM solutions that align better with variable staffing levels, seasonal fluctuations, and tighter IT budgets.
Complexity and Setup Challenges
Okta’s depth of functionality can also translate into complexity – both in setup and daily administration. Deployment timelines often stretch due to intricate configuration requirements, particularly in environments with multiple identity sources or custom applications. Integrating new systems may require specialized expertise, slowing time-to-value and increasing dependence on third-party consultants.
From an operational standpoint, administrators frequently cite usability challenges with policy management, role definitions, and reporting. The user interface, while robust, can be overwhelming for non-specialist IT staff, and end users sometimes experience friction when navigating multi-factor authentication (MFA) prompts or single sign-on (SSO) workflows. These factors contribute to higher support volumes and administrative overhead, prompting organizations to look for IAM platforms that deliver simpler, more intuitive user experiences.
Integration and Ecosystem Limitations
While Okta supports a wide range of applications, its architecture isn’t always optimized for modern, composable IAM frameworks. Many organizations today need solutions that seamlessly connect across multi-cloud environments, containerized infrastructures, and microservice-based applications. Okta’s integration model, though extensive, can require additional customization to support advanced automation, infrastructure-as-code workflows, or modern developer toolchains.
In contrast, emerging alternatives emphasize API-first designs and open standards like SCIM, OAuth 2.0, and OIDC to enable faster integrations and greater flexibility. This makes it easier for IT teams to embed access controls directly into application logic or CI/CD pipelines.
As identity management becomes more distributed, organizations increasingly prioritize solutions that allow lightweight interoperability, automation, and real-time governance.
Top 15 Okta Alternatives and Competitors in 2025
As the IAM landscape evolves, organizations are seeking platforms that offer greater flexibility, transparent pricing, and seamless integration across multi-cloud and hybrid environments. While Okta remains one of the most established players in the IAM market, several emerging and established vendors now provide comparable capabilities tailored to different business needs.
In 2025, the best Okta alternatives range from enterprise-grade identity platforms with deep governance capabilities to lightweight, developer-friendly solutions that simplify authentication and provisioning. The following list highlights the top 15 Okta competitors:
- Lumos
- Microsoft Entra ID
- Ping Identity
- CyberArk Workforce Identity
- OneLogin
- JumpCloud
- Keycloak
- FusionAuth
- ZITADEL
- Rippling
- ForgeRock
- SailPoint
- IBM Security Verify
- Saviynt
- SecureAuth
Let’s take a closer look at each one!
1. Lumos
- G2 Rating: 4.8/5
Pricing: Starts at ~$1/user/month (varies by feature set)
Lumos is built as the first autonomous identity platform. Instead of treating access management as a set of point solutions, Lumos weaves discovery, governance, and automation into one unified system. Rather than manually wrestling with app sprawl, your teams gain auto‑pilot control over who has what, when, and why.
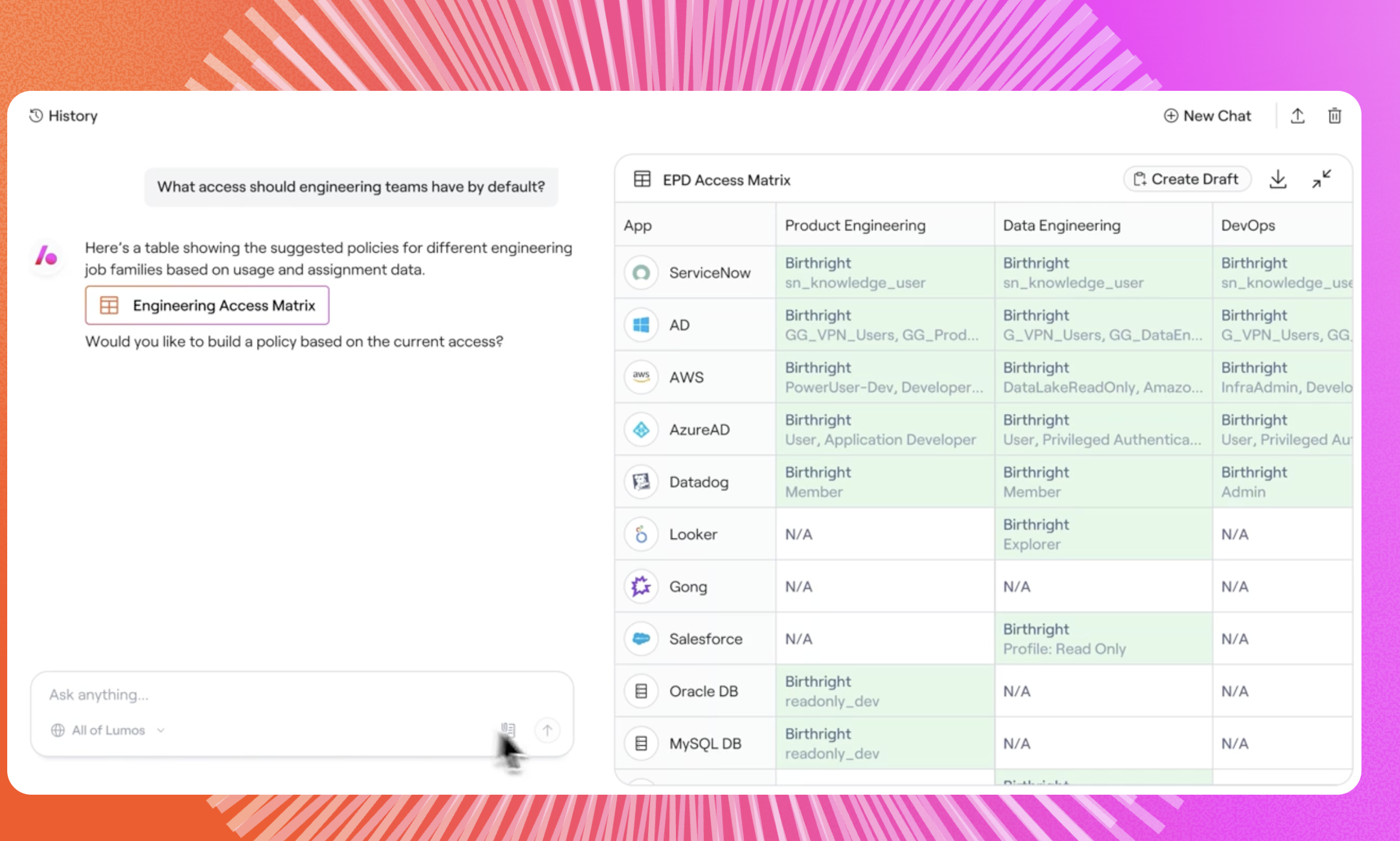
Features:
- Centralized Access Visibility: Lumos surfaces entitlement-level access across all connected systems – HRIS, IdP, SaaS, cloud, on-prem – to answer “who has access to what?” in real time, not weeks later.
- Accelerated & Intelligent Access Reviews: No more spreadsheets. Lumos automates the ingestion of access data, flags SoD violations, drives review workflows, and produces audit‑ready reports with minimal manual effort.
- End-to-End Identity Lifecycle Management: From onboarding to offboarding (and everything in between), Lumos automates access changes with RBAC/ABAC logic. It ensures people get the right access at the right time; and removes it cleanly when roles change.
- Seamless User Experience: Lumos supports multiple request channels – Web AppStore, Slack, Teams, CLI, and ITSM integration – while enforcing least privilege and just-in-time access.
- Agile, Less Complex Implementation: Compared to legacy IGA or identity platforms, Lumos is designed for agility. Integrations, role discovery, and governance features can be up and running faster, without the heavy maintenance burden.
Lumos is a great option for organizations wanting to streamline identity management, shrink audit burden, reduce license waste, and offload repetitive access operations. Lumos makes a strong alternative to conventional identity governance suites – especially when you want automation, transparency, and speed without a massive rollout project.
Looking to see how Lumos compares side-by-side with Okta or other vendors? Book a demo and we can walk you through real-world use cases.
2. Microsoft Entra ID
- G2 Rating: 4.5 / 5
- Pricing: Various tiers (premium features like identity governance often require higher plans)
Microsoft Entra ID is Microsoft’s enterprise-grade identity and access management platform. It offers a unified solution for managing identities across hybrid and cloud environments, making it a viable alternative to Okta; especially for organizations already using Microsoft 365, Azure, or other parts of the Microsoft ecosystem.

Features:
- Single Sign-On and Adaptive Authentication: Entra ID provides single sign-on across Microsoft and third-party applications. It also supports adaptive multifactor authentication (MFA) and conditional access policies, allowing organizations to tailor login requirements based on user context, device, and risk level.
- Lifecycle Workflows and Automation: With Lifecycle Workflows, Entra ID automates user onboarding, offboarding, and role changes. Identity attributes sync automatically, and provisioning is triggered by HR or directory changes.
- Access Governance and Reviews: Entra ID Governance includes tools for managing access packages, conducting periodic access reviews, and enforcing separation of duties. These capabilities ensure that the right users have the right access—and only when they need it.
- Dynamic Role and Group Management: Role assignments and group memberships can be defined using user attributes like department or job title. This allows for dynamic, policy-driven access control that evolves as your organization changes.
- Broad Integration Support: Entra ID integrates with a wide range of SaaS, on-prem, and custom applications using protocols like SCIM, SAML, and LDAP, giving it broad coverage across your environment.
Microsoft Entra ID excels in environments already aligned with Microsoft infrastructure. It offers tight integration and built-in capabilities that may reduce overall complexity and licensing costs for Microsoft-first organizations.
3. Ping Identity
- G2 Rating: 4.3/5
- Pricing: Custom pricing based on organization size, deployment type, and selected modules
Ping Identity is an enterprise-grade identity management platform focused on secure, scalable authentication and access for hybrid and multi-cloud environments. Known for its flexibility and support for open standards, Ping provides tools for identity federation, single sign-on (SSO), and adaptive multi-factor authentication (MFA). It’s often chosen by large organizations seeking a more customizable and security-driven alternative to Okta.

Features:
- Enterprise-Grade SSO and Federation: Ping supports industry-standard protocols like SAML, OAuth 2.0, and OpenID Connect, enabling seamless SSO across on-premises, cloud, and SaaS applications.
- Adaptive MFA: Combines device intelligence, user context, and behavioral analytics to dynamically enforce MFA policies without compromising usability.
- Granular Access Control: Leverages policy-based and attribute-based access models to manage complex authorization scenarios at scale.
- Comprehensive Integration Ecosystem: Offers pre-built connectors for thousands of enterprise applications and directories, along with APIs for custom integrations and developer extensibility.
- Hybrid and Multi-Cloud Support: Designed for flexible deployments, Ping can run on-premises, in private or public clouds, or as a fully managed SaaS solution.
Ping Identity excels in environments where security, compliance, and architectural flexibility are top priorities. Compared to Okta, Ping offers deeper policy customization and better support for complex enterprise ecosystems, though it may require more administrative expertise during deployment.
4. CyberArk Workforce Identity
- G2 Rating: 4.4/5
- Pricing: Custom pricing based on deployment scale, workforce size, and selected identity modules
CyberArk Workforce Identity, part of CyberArk’s broader identity security platform, delivers access management and adaptive authentication designed for enterprise-scale environments. Known for its security posture and alignment with Zero Trust principles, it helps organizations protect workforce identities, secure privileged access, and minimize the risk of credential-based attacks.

Features:
- Adaptive Multi-Factor Authentication (MFA): Dynamically adjusts authentication requirements based on contextual risk factors such as user behavior, device posture, and location, ensuring security without adding unnecessary friction.
- Single Sign-On (SSO): Provides secure access across SaaS, on-premises, and cloud applications using SAML, OAuth, and OpenID Connect.
- Privileged Access Integration: Leverages CyberArk’s privileged access management (PAM) foundation to extend protection to high-risk accounts, unifying workforce and administrative access under one security framework.
- Policy-Based Access Controls: Uses granular access rules and risk-based policies to enforce least privilege while maintaining flexibility for evolving business needs.
- Comprehensive Reporting and Compliance Tools: Generates detailed audit trails, access analytics, and compliance reports to meet SOX, HIPAA, and ISO 27001 standards.
Compared to Okta, CyberArk Workforce Identity emphasizes security depth over simplicity, offering a more unified approach to managing both regular and privileged users. For enterprises seeking to strengthen Zero Trust implementation and reduce credential exposure, CyberArk provides a security-first alternative.
5. OneLogin
- G2 Rating: 4.3/5
- Pricing: Custom pricing; plans typically start around $2 per user/month with enterprise options available
OneLogin is a cloud-based identity and access management solution designed to simplify and secure user authentication across enterprise applications. Now part of One Identity, it provides centralized identity governance, adaptive authentication, and integrations for both cloud and on-premises systems. OneLogin is a reasonable Okta alternative for organizations seeking a user-friendly, standards-based platform that balances security and simplicity.

Features:
- Single Sign-On (SSO): Provides secure, one-click access to thousands of pre-integrated applications using SAML, OpenID Connect, and OAuth protocols.
- SmartFactor Authentication: Uses machine learning to assess risk in real time and apply adaptive MFA policies based on user context, device, and network conditions.
- Unified Directory and User Provisioning: Syncs identities from multiple directories (e.g., Active Directory, LDAP, Google Workspace) to simplify onboarding, offboarding, and access lifecycle management.
- Advanced Security Policies: Enables conditional access controls, session monitoring, and device trust enforcement to strengthen Zero Trust implementations.
- Comprehensive Integration Ecosystem: Offers over 6,000 app integrations through its catalog and robust APIs for custom connectivity in hybrid environments.
OneLogin excels in organizations looking for ease of deployment and unified identity management across cloud and legacy systems. Compared to Okta, it offers similar SSO and MFA capabilities with a cleaner administrative experience and competitive pricing.
6. JumpCloud
- G2 Rating: 4.6/5
- Pricing: Free for up to 10 users and 10 devices; paid plans start at $11 per user/month
JumpCloud is an open directory platform that unifies identity, device, and access management for modern hybrid IT environments. Designed with flexibility in mind, JumpCloud helps organizations consolidate authentication and authorization across systems, networks, and applications. It’s a solid Okta alternative for organizations embracing cloud-native IT and Zero Trust access models.
Features:
- Unified Directory Platform: Serves as a central source of truth for user identities across Windows, macOS, and Linux systems, cloud applications, and on-prem resources.
- Single Sign-On (SSO): Supports SAML 2.0 and OIDC-based authentication to simplify access to thousands of pre-integrated apps and services.
- Comprehensive Device Management: Integrates identity and device security by enforcing policies, patching, and compliance checks at the endpoint level.
- Passwordless and MFA Options: Offers adaptive MFA and hardware-based authentication to reduce credential-related risks.
- Cross-Platform Access Control: Seamlessly manages permissions across diverse environments, including servers, VPNs, and file shares – all managed through one console.
- APIs and Integrations: Provides REST APIs and integrations with identity providers, HR systems, and SIEM tools for streamlined automation and visibility.
JumpCloud excels for IT teams looking to replace or extend Active Directory while maintaining centralized control over identity and device management. Compared to Okta, it provides deeper endpoint integration, broader OS support, and a more unified IT operations experience.
7. Keycloak
- G2 Rating: 4.4/5
- Pricing: Open-source and free to use; optional enterprise support available via Red Hat Single Sign-On
Keycloak is an open-source IAM solution maintained by Red Hat, offering enterprise-grade authentication and authorization features without licensing costs. It provides single sign-on (SSO), identity brokering, and fine-grained access control; which makes it a popular Okta alternative for organizations that prefer open-source flexibility and on-premises deployment options.
Features:
- Single Sign-On (SSO): Supports seamless authentication across applications using standard protocols like SAML 2.0, OAuth 2.0, and OpenID Connect.
- Identity Brokering and Federation: Enables integration with external identity providers (such as Google, Azure AD, or LDAP directories) to centralize identity management.
- User Federation: Connects to existing directories to synchronize users and credentials, simplifying hybrid identity environments.
- Role-Based and Attribute-Based Access Control: Allows administrators to define roles, policies, and permissions at both the realm and application level for granular control.
- Customizable Login and Themes: Offers full control over branding and user experience, allowing teams to design consistent authentication pages and flows.
- Extensible Architecture: Built for developers, with REST APIs, SPIs, and extension points for custom authentication logic, workflows, or integrations.
Keycloak offers developer-friendly flexibility and open-source transparency, making it ideal for organizations that want to self-manage their IAM stack or avoid vendor lock-in. Compared to Okta, Keycloak offers more control and customization at the infrastructure level but may require greater operational expertise to deploy and maintain.
8. FusionAuth
- G2 Rating: 4.7/5
- Pricing: Free community edition; paid cloud plans start at approximately $125/month
FusionAuth is a developer-focused identity and access management solution that provides complete control over authentication, authorization, and user management. Designed to be self-hosted or deployed in the cloud, FusionAuth offers a flexible alternative to Okta for organizations that want customization, transparency, and cost efficiency without sacrificing enterprise-grade security.
Features:
- Comprehensive Authentication Support: Delivers OAuth 2.0, OpenID Connect, and SAML integrations with built-in MFA, passwordless login, and federated identity support.
- Full User Lifecycle Management: Handles registration, password recovery, email verification, and account deactivation through customizable workflows.
- Flexible Deployment Options: Can be deployed on-premises, in private clouds, or fully managed through FusionAuth Cloud for scalability and compliance needs.
- Advanced Developer Customization: Provides APIs, webhooks, and customizable themes for login pages, consent screens, and registration flows.
- Multi-Tenant and Multi-App Architecture: Supports distinct tenants and apps within a single deployment – ideal for SaaS companies or complex organizations managing multiple identity contexts.
- Data Control and Compliance: Gives organizations full ownership of user data to meet privacy, regulatory, and localization requirements.
FusionAuth appeals to teams that prioritize developer autonomy, transparency, and API-driven integration. Compared to Okta, it offers greater flexibility and ownership of infrastructure, with lower long-term costs; particularly for engineering-driven organizations or product teams embedding authentication directly into their applications.
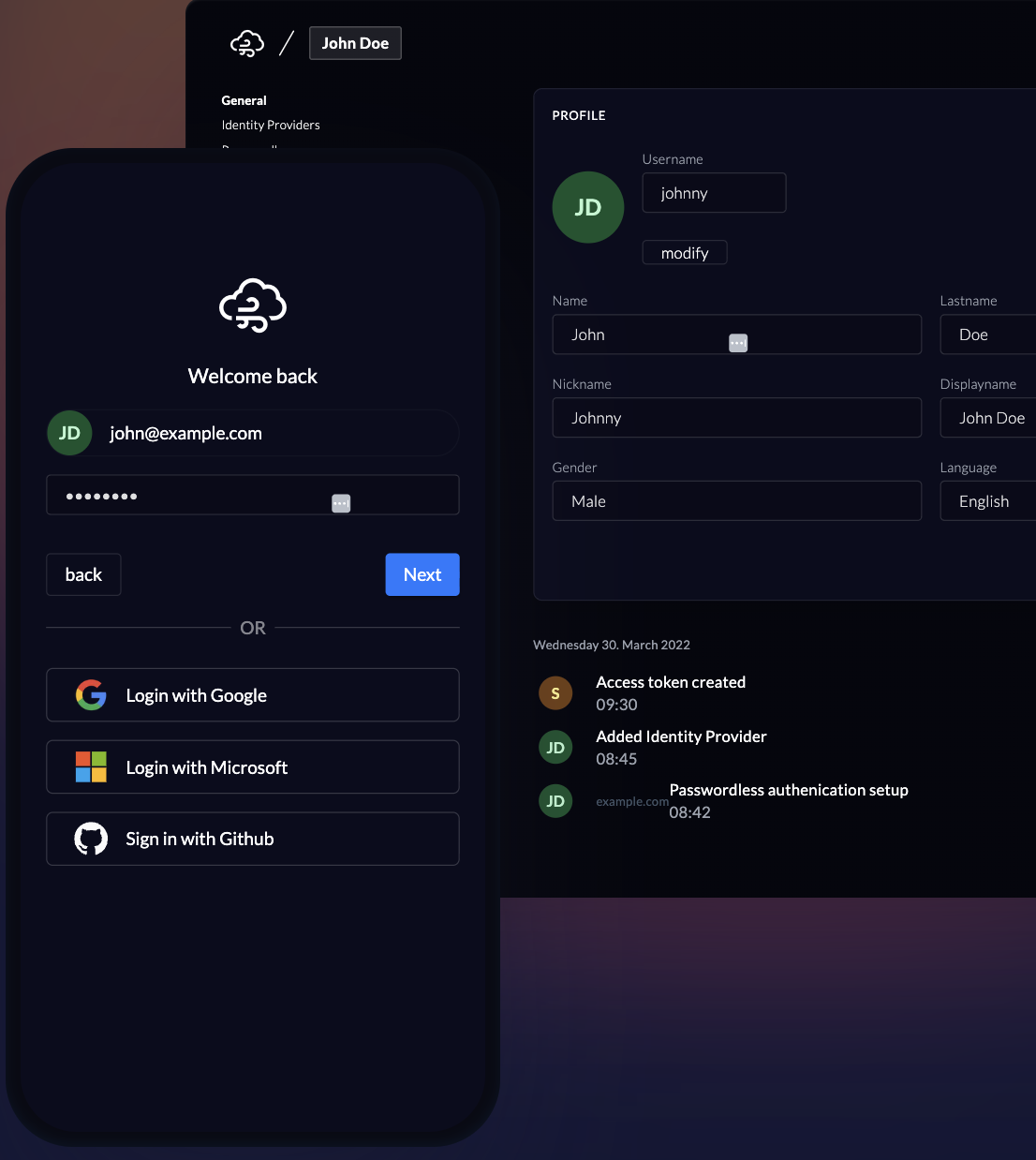
9. ZITADEL
- G2 Rating: 4.6/5
- Pricing: Free community tier available; paid plans start at approximately $25/month for advanced enterprise features
ZITADEL is an open-source, cloud-native identity and access management (IAM) platform built for modern DevOps and security teams. It provides a unified framework for authentication, authorization, and user management with a strong focus on automation and scalability. As an alternative to Okta, ZITADEL delivers fine-grained control, transparent architecture, and flexible deployment models, making it ideal for organizations embracing Zero Trust and composable IAM ecosystems.
Features:
- Open-Source and Cloud-Native: Built on Go and CockroachDB, ZITADEL offers horizontal scalability, fault tolerance, and transparency for both on-prem and cloud deployments.
- OIDC, OAuth 2.0, and SAML Support: Seamlessly integrates with a wide range of applications and APIs using modern identity standards.
- Granular Role and Project Management: Enables hierarchical permission structures and delegated administration across tenants, applications, and projects.
- Passwordless and MFA Support: Provides built-in WebAuthn and FIDO2 authentication methods, reducing credential risk and enhancing user experience.
- Developer-Friendly APIs and SDKs: Designed for automation and integration within CI/CD pipelines and infrastructure-as-code environments.
- Audit Logging and Compliance: Tracks authentication events and administrative changes for audit readiness and governance.
ZITADEL stands out for its developer-first approach, open architecture, and cloud-native scalability, making it a compelling choice for organizations seeking flexibility and transparency. Compared to Okta, it offers greater customization and data sovereignty, allowing security teams to adapt identity management to their operational and compliance needs. For enterprises building secure, scalable systems that align with DevSecOps principles, ZITADEL provides a future-ready alternative.
10. Rippling
- G2 Rating: 4.8/5
- Pricing: Starts at $8 per user/month; pricing varies based on modules and integrations
Rippling is an all-in-one workforce management platform that unifies HR, IT, and finance operations: including onboarding, payroll, device management, and access provisioning. Unlike traditional IAM vendors, Rippling integrates identity and access management directly into employee lifecycle management, making it a viable Okta alternative for organizations seeking integrated access control and automation across HR and IT workflows.
Features:
- Unified Employee Lifecycle Management: Automatically provisions and deprovisions user accounts and access permissions when employees join, move, or leave the company.
- Built-In Identity Management: Offers SSO, MFA, and directory sync capabilities natively integrated with HR and payroll data, reducing administrative overhead.
- App and Device Provisioning: Manages access to SaaS applications and hardware from a single console, ensuring alignment between IT and HR processes.
- Workflow Automation: Triggers automated actions based on employee status changes, such as revoking credentials upon termination or adjusting access when roles change.
- Compliance and Audit Support: Maintains detailed logs and access histories for audit readiness across HR, IT, and security operations.
- Integrations with Core Business Systems: Connects with tools like Google Workspace, Slack, Salesforce, and Microsoft 365, supporting hybrid and remote environments.
Rippling offers tight integration between identity, access, and employee data, enabling organizations to achieve security and operational efficiency without managing multiple disconnected platforms. Compared to Okta, Rippling offers broader business automation and cost consolidation, though it may be less customizable for enterprises with complex IAM policies.
11. miniOrgange
- G2 Rating: 4.6/5
- Pricing: Starts around $1 per user/month; enterprise plans available with volume-based pricing
miniOrange is a versatile IAM provider that offers a wide range of security and authentication solutions for businesses of all sizes. Positioned as a cost-effective and flexible alternative to Okta, miniOrange supports modern access control, SSO, and MFA across cloud and on-premises environments.
Features:
- Comprehensive SSO Support: Provides single sign-on across thousands of pre-integrated applications using SAML, OAuth, OpenID Connect, and WS-Federation protocols.
- Adaptive Multi-Factor Authentication (MFA): Offers contextual authentication based on IP, device, time, or user behavior, balancing strong security with user convenience.
- User Provisioning and Lifecycle Management: Automates onboarding and deprovisioning workflows with integrations for Active Directory, Azure AD, Google Workspace, and HR systems.
- Custom Branding and Whitelabel Options: Allows organizations to fully brand their login portals and end-user experiences – a useful feature for MSPs and resellers.
- Granular Access Policies: Enables attribute- and role-based access enforcement through centralized dashboards for IT and compliance teams.
- Cloud, On-Premises, and Hybrid Deployment: Offers flexible hosting options depending on organizational security and regulatory requirements.
miniOrange stands out for its broad protocol support, ease of customization, and affordability. Compared to Okta, it provides more flexibility in deployment models and more transparent pricing for mid-market and global organizations. While Okta targets large enterprise ecosystems, miniOrange appeals to IT teams looking for a lightweight, scalable, and fully manageable IAM platform that still offers strong integration and compliance capabilities.
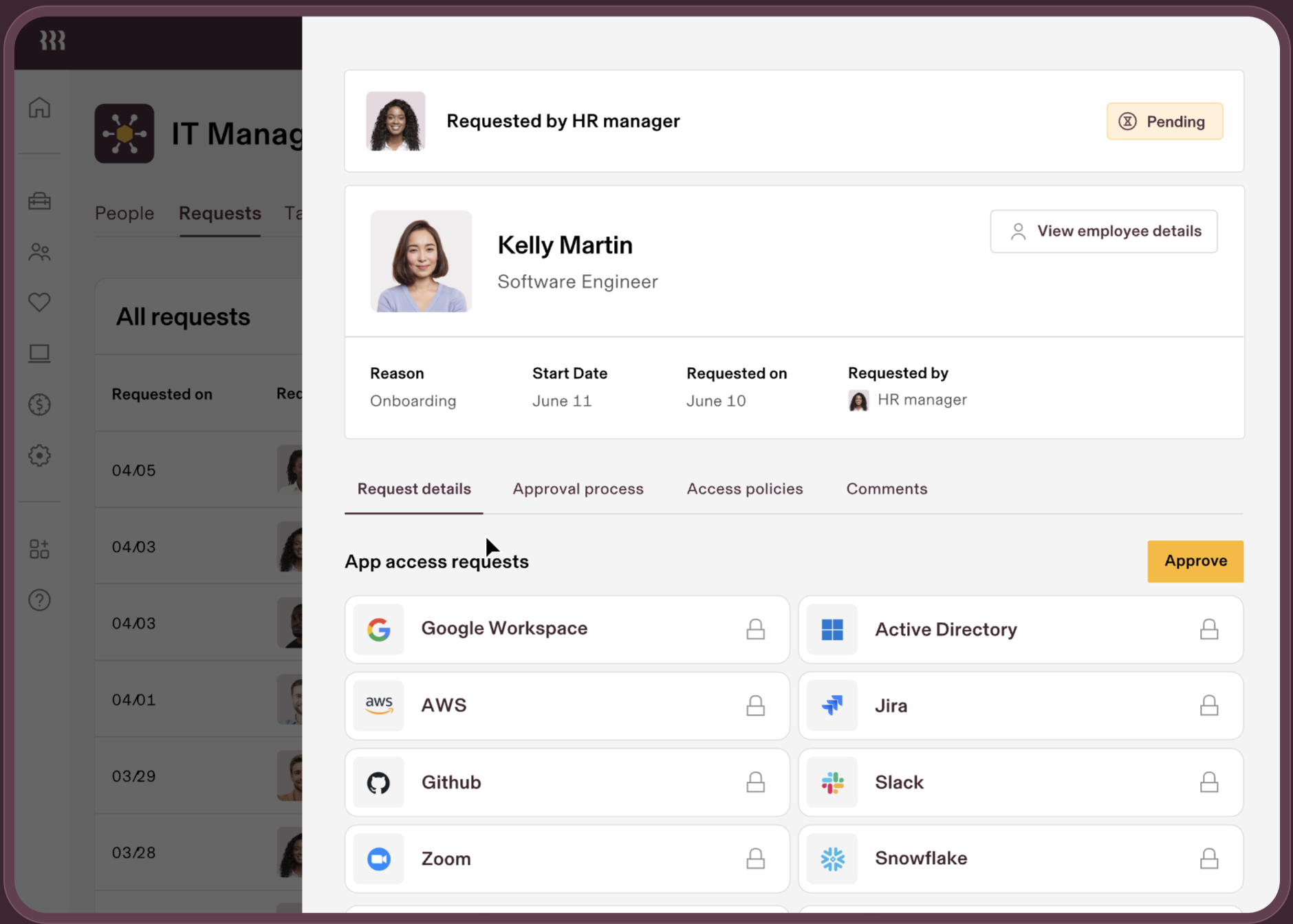
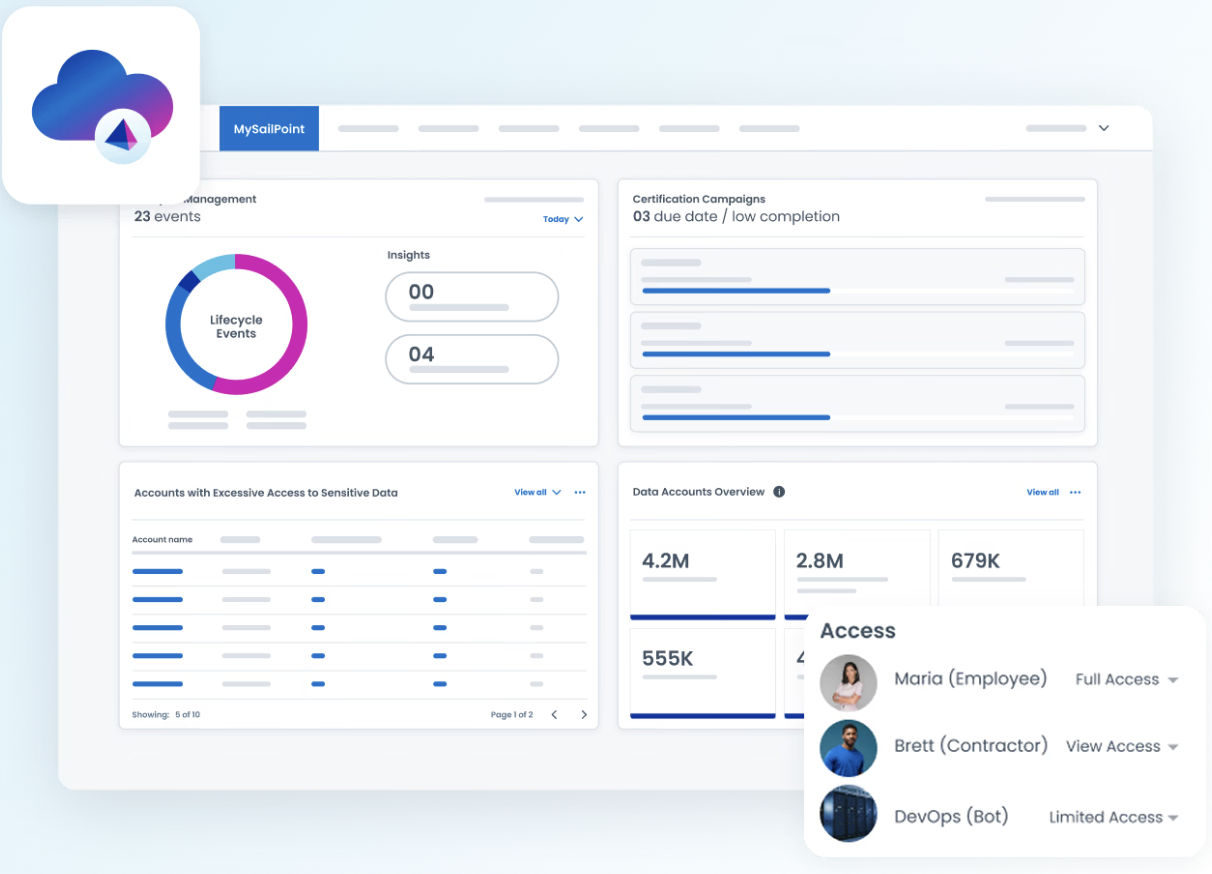
12. SailPoint
- G2 Rating: 4.4/5
- Pricing: Custom pricing based on organization size, deployment model, and selected modules
SailPoint is an identity security and governance platform designed to provide enterprises with deep visibility into access permissions, risk management, and compliance across complex environments. While Okta emphasizes identity access and SSO workflows, SailPoint focuses on identity governance and lifecycle automation, making it an option for organizations prioritizing compliance, auditability, and access risk reduction.
Features:
- Comprehensive Identity Governance: Automates access reviews, certification processes, and policy enforcement to maintain continuous compliance with SOX, GDPR, HIPAA, and ISO standards.
- AI-Driven Role Mining and Access Insights: Uses artificial intelligence and machine learning to detect risky entitlements, recommend least-privilege roles, and simplify policy management.
- Automated Provisioning and Deprovisioning: Streamlines user lifecycle management by connecting to HR systems and cloud applications for real-time access adjustments.
- Separation of Duties (SoD) Controls: Prevents toxic access combinations through automated policy enforcement and violation monitoring.
- Integration with Hybrid and Multi-Cloud Environments: Offers out-of-the-box connectors for SaaS platforms, data centers, and on-premise systems like Active Directory and SAP.
- Advanced Analytics and Reporting: Provides detailed audit logs, access dashboards, and compliance metrics to strengthen governance programs.
SailPoint operates in governance-heavy environments that require granular access visibility and strong compliance oversight. Compared to Okta, which focuses on access management and SSO simplicity, SailPoint delivers deeper identity analytics, automation, and control frameworks.
13. IBM Security Verify
- G2 Rating: 4.2/5
- Pricing: Custom pricing based on user count, deployment model, and enterprise requirements
IBM Security Verify is a comprehensive IAM platform that provides both workforce and consumer identity solutions with a strong emphasis on security, compliance, and scalability. Designed for large enterprises with complex hybrid or multi-cloud environments, IBM Security Verify serves as an Okta alternative for organizations prioritizing advanced risk detection, identity governance, and zero-trust alignment.
Features:
- Adaptive Access and Risk-Based Authentication: Uses AI-driven risk scoring to evaluate user behavior and contextual signals – such as device, location, and time – to dynamically adjust authentication requirements.
- Single Sign-On (SSO): Provides a seamless login experience across cloud and on-premises applications with support for SAML, OAuth, and OpenID Connect.
- Identity Governance and Administration (IGA): Centralizes identity lifecycle management, role assignments, and access certifications to maintain compliance with SOX, HIPAA, and GDPR.
- Passwordless and MFA Capabilities: Supports biometric, FIDO2, and push-based authentication methods to eliminate credential-based risks.
- AI-Powered Threat Analytics: Continuously monitors login attempts and user activities to detect anomalies and reduce false positives in access decisions.
- Deployment Flexibility: Available in both cloud and on-premises models, making it adaptable for organizations transitioning from legacy infrastructure to hybrid ecosystems.
IBM Security Verify differentiates itself through enterprise-grade analytics, zero-trust alignment, and AI-enhanced risk detection, offering deeper governance capabilities than Okta’s access-first approach. IBM provides a broader security and compliance framework suited for highly regulated industries such as finance, healthcare, and government.
14. Saviynt
- G2 Rating: 4.4/5
- Pricing: Custom pricing based on user volume, modules, and enterprise requirements
Saviynt is an Identity Governance and Administration (IGA) platform built to provide unified visibility, access control, and compliance management across hybrid and cloud ecosystems. As an alternative to Okta, Saviynt differentiates itself with deep governance capabilities, granular access analytics, and cloud-native architecture.

Features:
- Comprehensive Identity Governance: Centralizes identity lifecycle management, access certifications, and SoD (Separation of Duties) enforcement to strengthen compliance and internal controls.
- Cloud-Native Platform: Designed natively for multi-cloud environments such as AWS, Azure, and GCP, offering flexibility and scalability without heavy infrastructure dependencies.
- Risk-Based Access Controls: Uses AI-driven analytics to identify access outliers, recommend role adjustments, and reduce unnecessary entitlements.
- Privileged Access Management (PAM) Integration: Combines IGA with just-in-time access provisioning for sensitive accounts, minimizing standing privileges.
- Automated Provisioning and Deprovisioning: Streamlines onboarding and offboarding workflows through pre-built connectors for enterprise and SaaS applications.
- Compliance and Audit Readiness: Provides real-time dashboards, automated evidence collection, and reporting to align with SOX, HIPAA, GDPR, and ISO standards.
Saviynt fits where identity governance, access intelligence, and regulatory compliance are top priorities. Compared to Okta, which focuses heavily on access management and authentication, Saviynt offers deeper risk insight, compliance automation, and governance integration for enterprise-scale operations.
15. SecureAuth
- G2 Rating: 4.3/5
- Pricing: Custom pricing based on user volume, deployment type, and selected authentication modules
SecureAuth is an identity and access management solution specializing in adaptive authentication and passwordless security. Designed for enterprises seeking to strengthen user verification, SecureAuth serves as an alternative to Okta for organizations focused on contextual authentication, advanced threat detection, and zero-trust alignment.

Features:
- Adaptive Authentication: Leverages over 30 contextual risk signals – including device fingerprinting, IP reputation, and behavioral biometrics – to dynamically adjust authentication requirements.
- Passwordless Login Options: Supports a wide range of modern authentication methods such as FIDO2, biometrics, and push-to-approve, reducing dependency on passwords and minimizing credential-related risks.
- Comprehensive MFA Support: Offers versatile MFA capabilities across cloud, on-prem, and hybrid systems, with flexible enrollment and enforcement policies.
- Risk Engine and Threat Intelligence: Uses machine learning to detect suspicious login attempts and anomalous access patterns in real time, improving response times and reducing false positives.
- Customizable Access Policies: Enables administrators to design and deploy fine-grained, policy-based access controls aligned with zero-trust principles.
- Integration Ecosystem: Compatible with SAML, OAuth, and OpenID Connect, SecureAuth integrates easily with enterprise directories, VPNs, and critical SaaS applications.
SecureAuth stands out for its depth in adaptive authentication and strong threat analytics, giving organizations more flexibility and control than traditional SSO platforms. While Okta focuses on ease of use and broad integrations, SecureAuth provides greater depth in identity risk scoring and contextual decision-making.
How to Choose the Right Okta Alternative
Selecting an Okta alternative isn’t just about switching IAM platforms: it’s about aligning identity strategy with your organization’s evolving security, compliance, and scalability needs. The right choice depends on understanding both technical requirements and operational goals, from authentication and governance to cost efficiency and ecosystem compatibility.
Key Evaluation Criteria
When evaluating alternatives to Okta, IT and security leaders should consider these foundational factors:
- Security and Compliance Certifications: Ensure that any IAM or IGA platform meets key compliance frameworks such as SOC 2 Type II, ISO 27001, HIPAA, and GDPR. These certifications demonstrate that the vendor maintains rigorous security controls and adheres to international privacy standards.
- Integration Support for SaaS, Cloud, and On-Prem Systems: A strong Okta alternative should seamlessly integrate with your existing environment; supporting SAML, SCIM, LDAP, OAuth, and OpenID Connect. Look for solutions that provide pre-built connectors for core enterprise tools like Microsoft 365, Google Workspace, AWS, and Salesforce.
- Scalability and Performance Under Enterprise Workloads: As identity volumes grow, scalability becomes critical. Evaluate how each platform performs under high authentication loads, complex directory structures, and hybrid cloud environments. Cloud-native IAM solutions often provide better elasticity and uptime guarantees.
- Customization and Extensibility: Identity requirements vary by organization. The best Okta alternatives offer custom workflows, APIs, and policy engines that allow fine-tuned governance, adaptive authentication, and integration with DevOps or CI/CD pipelines.
These criteria ensure that your chosen platform not only replicates Okta’s capabilities but enhances them, and provides a future-ready identity foundation that can evolve with your business.
Use-Case Alignment
The next step is identifying how the solution fits your operational context. Not every organization requires a full-featured IAM platform; some need governance depth, while others prioritize authentication flexibility.
- Lifecycle Management vs. Authentication Focus: If your organization needs automated provisioning, access reviews, and compliance workflows, prioritize vendors offering strong IGA (Identity Governance and Administration) capabilities, such as SailPoint or Saviynt. For teams focused on SSO, MFA, and adaptive authentication, platforms like Ping Identity, CyberArk Workforce Identity, or SecureAuth may be a better fit.
- IAM vs. IGA (Identity Governance and Administration): IAM platforms manage authentication, access, and SSO, while IGA tools focus on compliance, least privilege, and access certifications. Some platforms—like Lumos—combine both, offering unified visibility, lifecycle automation, and risk reduction in one system.
By aligning your vendor choice with both security maturity and operational goals, you can achieve the balance between control, agility, and compliance that modern identity ecosystems demand.
Why Lumos Is a Powerful Okta Alternative
Lumos isn’t just “Okta, but better.” We’re built around a different paradigm – autonomous identity governance – that merges Next‑Gen IGA, AI-powered automation, and seamless lifecycle orchestration into a single platform. Whereas Okta focuses heavily on authentication, SSO, and identity infrastructure, Lumos extends further: delivering governance, policy automation, and deep access control across human and machine identities.
Agentic AI for Governance
Lumos introduces Albus, our AI identity agent, to elevate governance from static to autonomous:
- Smart Policy Recommendations: Albus reviews usage patterns and entitlement data to flag overprivileged accounts, dormant access, and conflict risks before they become threats.
- Contextual Learning: The system learns from reviewer decisions – approvals, rejections, compliance feedback – and refines future suggestions so you see fewer false positives and reviewer fatigue diminishes.
- Conversational Access Insight: Need to know “Which devs have admin rights?” or “Which apps show sudden usage spikes?” You can query Lumos in plain language and get evidence-backed answers; speeding audits, reviews, and investigations.
This agentic layer moves governance from reactive cleanup to proactive control, where the system not only suggests but evolves your access model.
Deep Access Visibility and Governance
Lumos gives you clarity into every corner of your identity ecosystem:
- Unified Access Graph: Every user, entitlement, group, and resource relationship is mapped in one graph; across SaaS, infrastructure, cloud, and on-prem systems.
- Least-Privilege Enforcement: Ongoing analysis surfaces users with excess permissions and recommends just-in-time rights reduction.
- Dynamic Access Reviews: Certification campaigns run automatically with risk scoring, review prioritization, and tiered decision logic. This cuts review cycles from weeks to hours.
- Usage-Based Controls: By including real usage data (not just assignments), Lumos prioritizes which permissions and users merit attention, to help you focus security effort where it matters most.
Together, these visibility and governance capabilities allow security and compliance teams to catch risky access before it becomes an incident.
Built-In Policy Mining and Role Engineering
Role design is traditionally tedious. Lumos makes it intelligent:
- AI-Driven Role Discovery: Albus analyzes real access clusters and suggests role structures: grouping users by common entitlements, not guesswork.
- Policy Simulation & What-Ifs: Test proposed roles (or changes) safely before enforcing them to see how they’d impact your environment.
- Adaptive Role Updates: When people move or responsibilities shift, Lumos updates role definitions dynamically, keeping your access model in sync with reality.
This shifts role engineering from a heavy lift to something continuously maintainable – without rebuilds every time orgs evolve.
Unified Experience for Requests, Lifecycle and Reviews
Lumos integrates everything under one roof – no fragmentation:
- Self-Service Requests: Users request access via a web portal, Slack, Teams, CLI, or integrated ITSM: complete with approval workflows, just-in-time enforcement, and audit trails.
- Lifecycle Automation: Onboarding, mover transitions, and offboarding run automatically via HRIS/IdP triggers, enforcing entitlement-level logic and policy rules.
- Compliance-Ready Reviews: Certification cycles, decision audits, and evidence exports are built-in; no spreadsheets, no stitching between systems.
By bringing request, lifecycle, and governance into one system, Lumos reduces operational overhead while strengthening security, compliance, and access hygiene across the board.
Ready to Go Beyond SSO?
Okta may be where access begins; but Lumos is where governance, control, and intelligent automation take over. If you’re looking to simplify identity management, reduce access risk, and make governance actually work at scale, Lumos is the upgrade your stack needs.
Book a demo with Lumos today and see how we bring identity governance, lifecycle automation, and agentic AI together in one unified platform.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.
%20Process.avif)



