Shine a Light on Shadow IT
See every app, managed and shadow, in one unified platform. Unify usage, risk, and spend to govern your stack and cut costs fast.








See Every App. Spend Less. Stay Safe.
Too many apps across direct sign-ups and SSOs — paired with too-broad permissions — creates blind spots, redundant tools, and mounting risk and cost. Turn every app into an efficient financial decision and future-proof your investments.
Maintain a single source-of-truth
Continuously discover every app across IT approved and shadow IT using multiple channels. Centralize app inventory with usage, owners, contracts, and entitlements in one single source-of-truth.
Automatically remediate to drive down spend by 15%
Track and remove unused licenses, orphaned accounts and unauthorized software with AI-powered insights — before costs snowball.
Get ahead of risk and spend
Uncover risky access and redundant tools, surface unused licenses, and track adoption. Align real-time dashboards with security posture and spend.
SaaS Discovery Delivered by Agentic AI
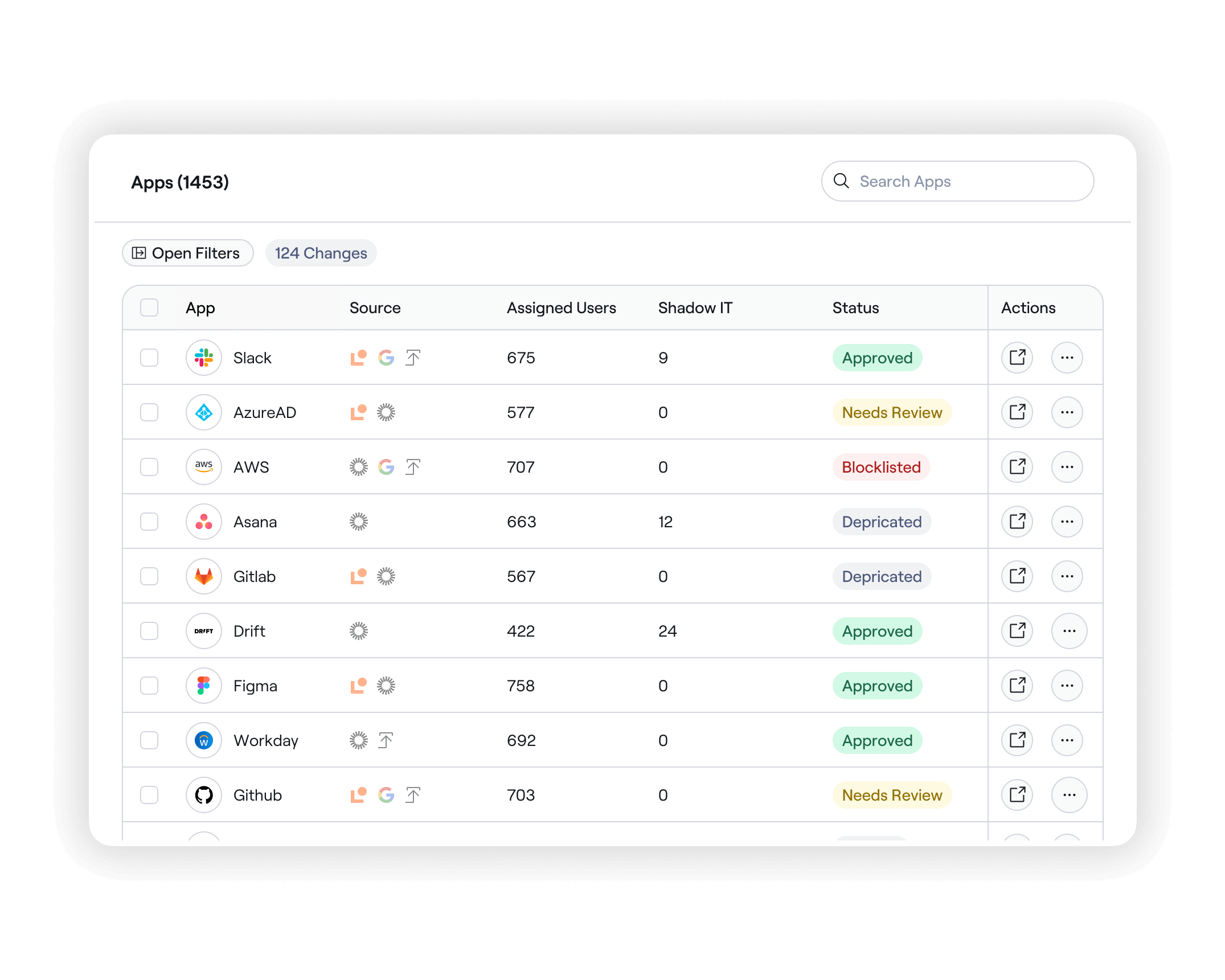
Maintain one centralized catalog
With Lumos, create a single source-of-truth for all apps, managed and shadow IT. Proactively identify unauthorized software, track license usage, and mitigate security risks with continuous enrichment via emails, logins, and contract ingestion.
Close security blind spots faster
With AI, expose unsafe and unsanctioned usage in minutes, surface access anomalies, track unused license patterns, and prevent stale access when employees depart. Standardize on approved tools with policy guardrails and least-privilege controls.

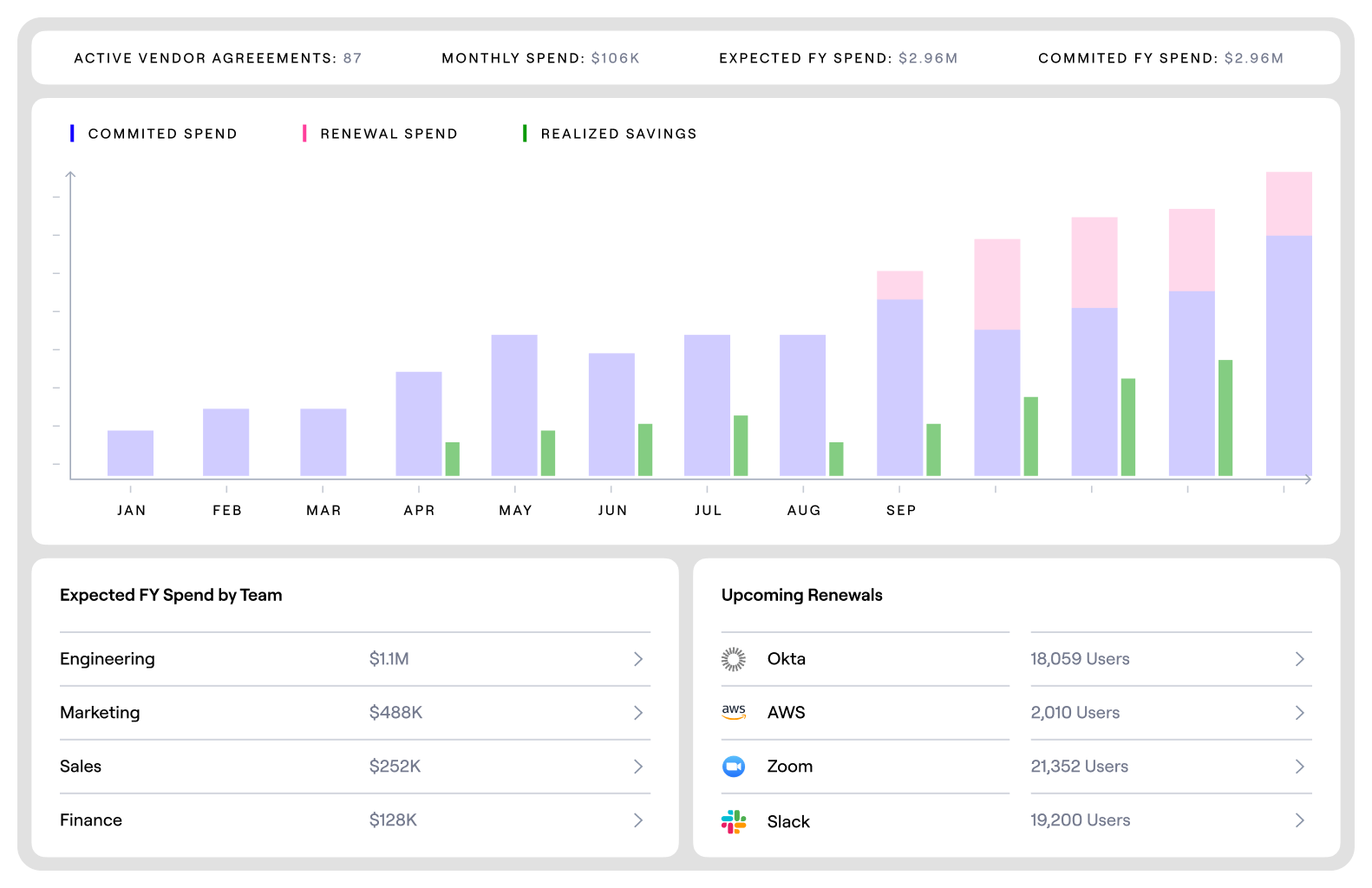
Unlock profitability gains with easy-to-use workflows
Automatically detect and remediate idle licenses, orphaned apps, and redundant tools with no-code automation. Drive financial efficiency and app rationalization with confidence.
Outcomes You Can Measure














Additional Resources
Frequently Asked Questions
Shadow IT refers to software, applications, or tools used within an organization without explicit approval from the IT or security team. These tools are often adopted by employees or teams to meet immediate needs but can bypass corporate security policies, leading to compliance risks, data exposure, and license waste.
You can discover shadow IT by monitoring authentication logs, browser extensions, expense reports, and SSO access logs to identify apps being used without IT oversight. However, this process is often manual and incomplete.
Lumos automates shadow IT discovery by integrating with your identity provider (IdP), and browser sessions to detect apps users are logging into and whether or not those apps are approved or under contract. This creates a centralized inventory of managed and unmanaged tools, helping IT regain control and reduce risk.
Reducing shadow IT starts with visibility, knowing which unapproved apps are in use, and continues with structured governance. Strategies include consolidating redundant tools, routing access through approved platforms, providing sanctioned alternatives, and tightening access controls.
With Lumos, teams can identify shadow apps, notify stakeholders, and work with functional leaders to either formalize, replace, or retire them. Lumos also enables self-service access to approved apps, reducing the need for teams to go rogue in the first place.
The risks of shadow IT include:
- Security vulnerabilities from unvetted tools and poor configurations
- Data leakage due to lack of DLP and compliance oversight
- Compliance violations (e.g., GDPR, HIPAA) if sensitive data is stored or processed improperly
- License waste and overspend from redundant or unauthorized tools
- Operational inefficiencies due to app sprawl and lack of visibility
Lumos helps mitigate these risks by surfacing unauthorized usage, enforcing least-privilege access, and consolidating your app ecosystem into a secure, manageable stack.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.



