Find and Fix What Matters, Fast
Continuously monitor identities — humans, machines, and agents — to bring access sprawl under control without slowing teams down.
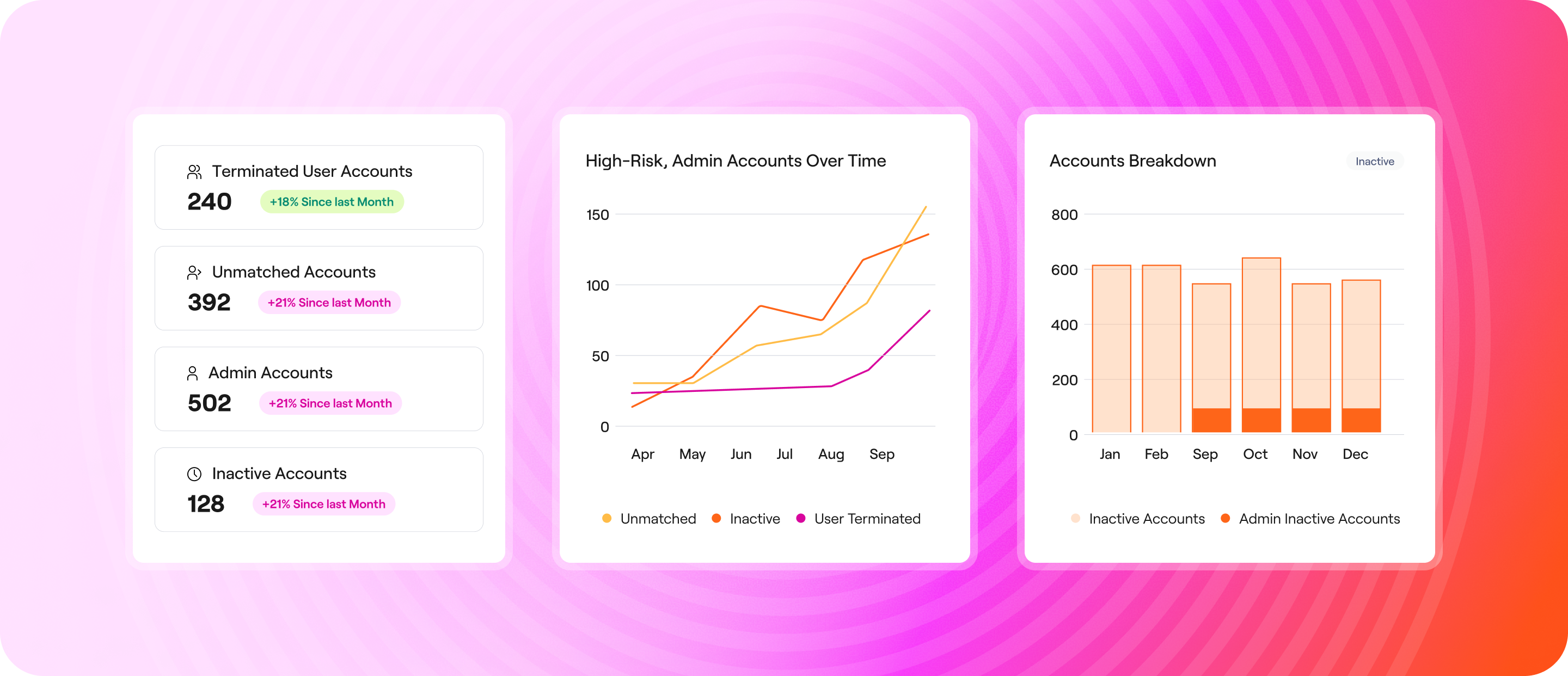







From Reactive to Proactive, Bring Your Sprawl Under Control
Privilege creep, non-human identities, shadow IT, and shadow AI make building scalable policies tough. Continuous monitoring and AI-powered analysis turns noise to prioritized signals so you can act before risks become breaches.
Spot risks faster with AI
Albus surfaces misconfigurations, SoD conflicts, access anomalies, toxic combinations, orphaned and dormant accounts, and privilege spikes. Get clear, explanation-backed ranking to prioritize remediation.
Enforce least-privilege by design
Apply JIT and time-bound access, revoke licenses based on inactivity, use peer baselines for policy creation, and build offboarding guardrails. Close security gaps before they become issues.
Analyze and prevent, on repeat
Continuously monitor access changes and trigger automated workflows to grant or remove access, launch delta-focused access reviews, and auto-remediate any violations with admin oversight. Visualize posture with live dashboards and audit-ready reports.
Outcomes Delivered With Agentic AI
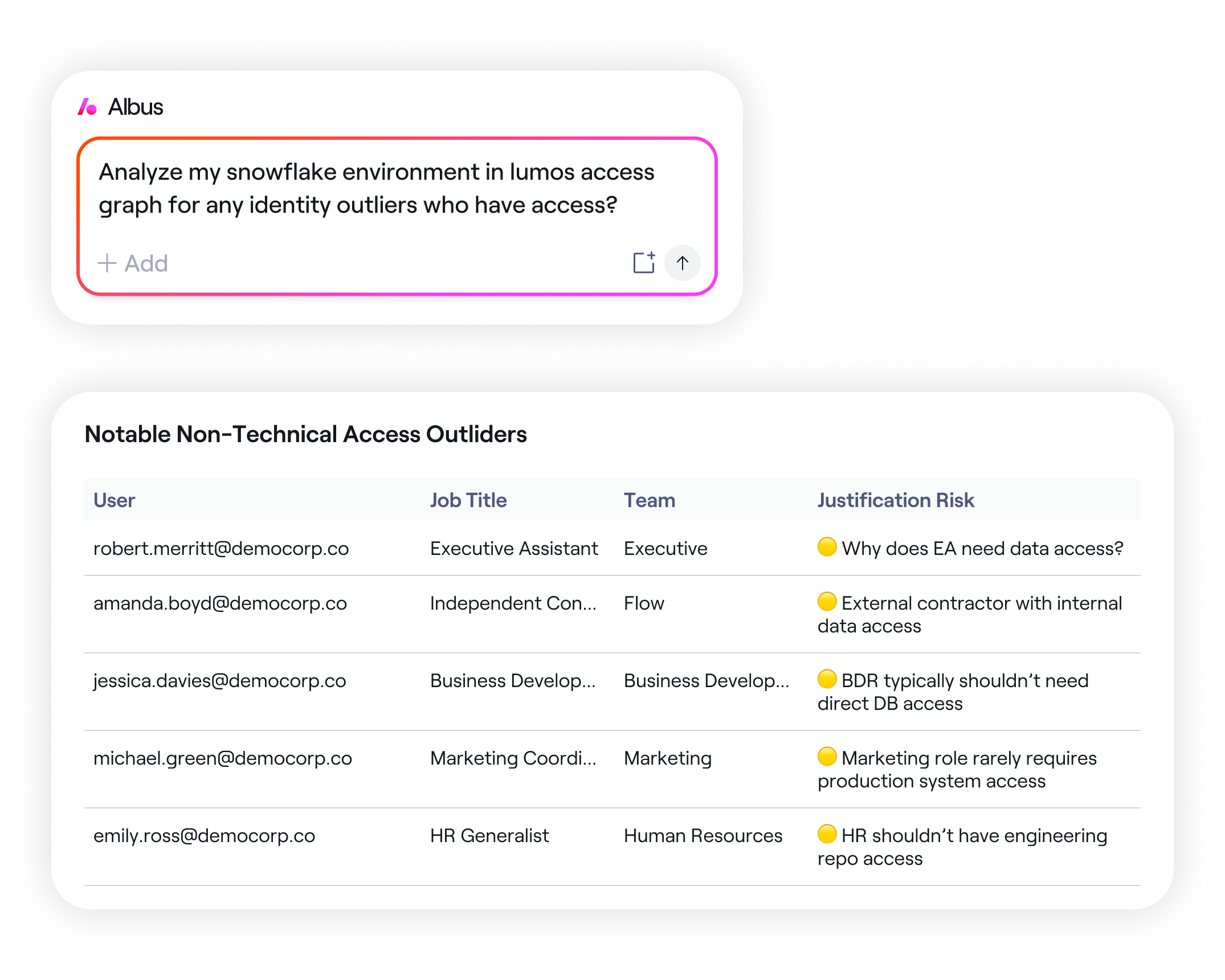
Identify who has access and whether they should
Unify identity hygiene with a single source-of-truth for all identities — human and non-human — and all SaaS, cloud, and on-premises apps. Go beyond groups and roles to understand granular entitlement with usage visibility. Eliminate data siloes and blind spots.
Prioritize what to remediate
Albus makes identity investigations as simple as asking a question. Go beyond surface-level alerts: analyzing real usage data, building contextual baselines, and automatically flagging outliers, misconfigurations, and unauthorized access. Each anomaly is scored and explained in plain language so security teams know what’s risky, why it matters, and where to act first.
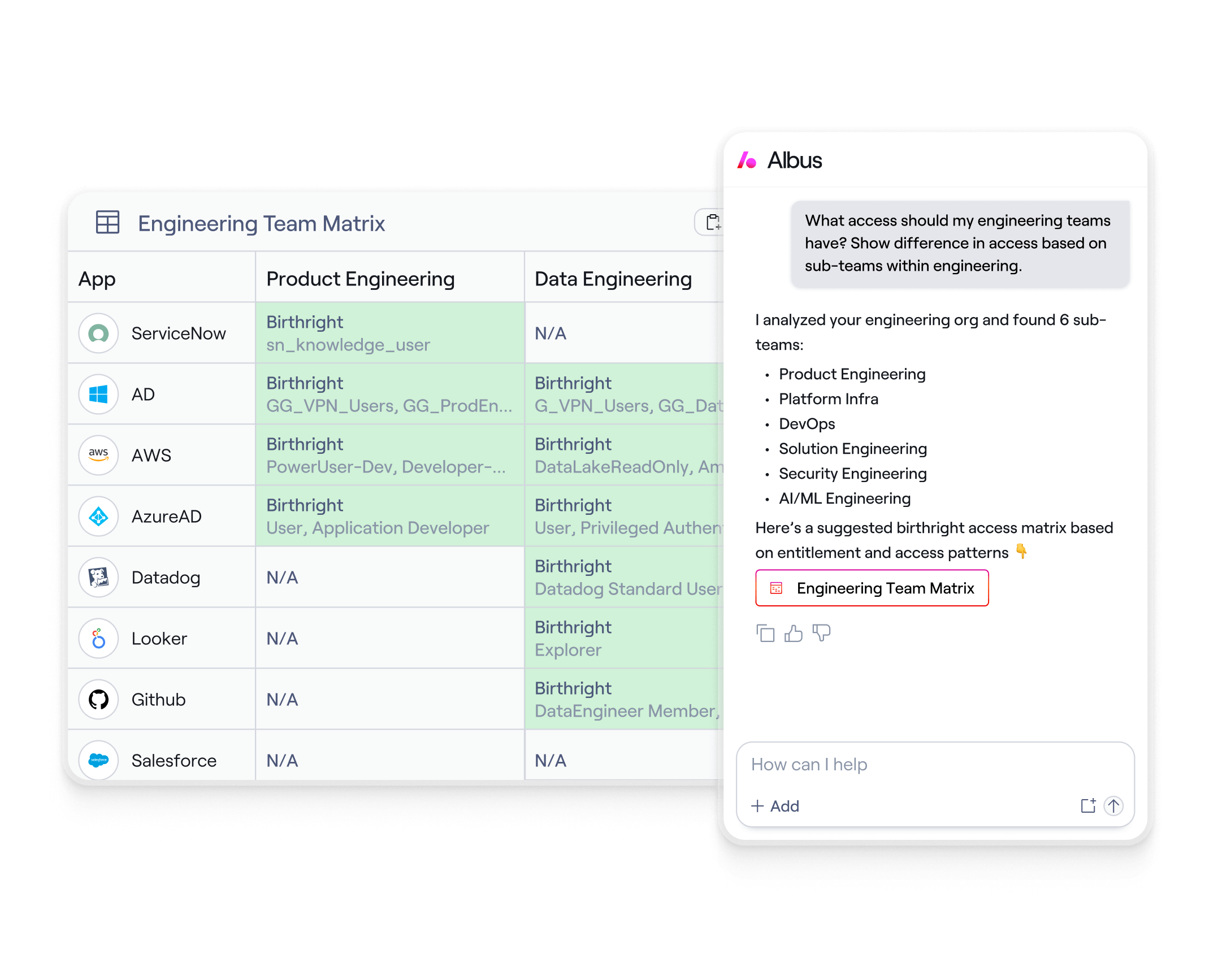
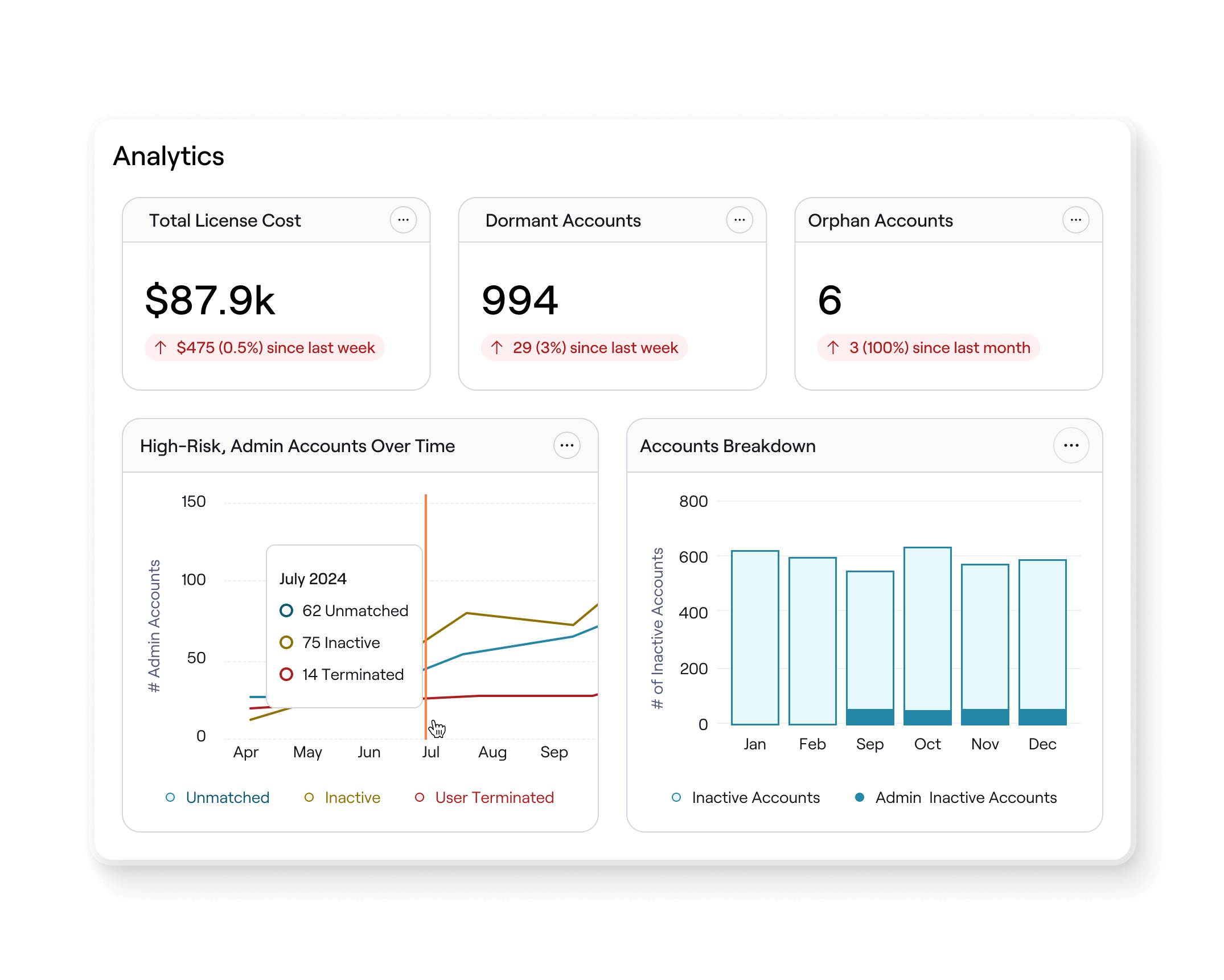
Accelerate risk assessment and reporting
Automate posture reporting with AI-built dashboards and one-click reporting to stakeholders, executives and auditors. Detect and report risky users, orphaned accounts, and terminated users using advanced analytics.
Outcomes You Can Measure














Additional Resources
Frequently Asked Questions
Identity Security Posture prioritizes who has what and how it’s used—finding misconfigurations, SoD conflicts, and excess privilege—then triggers governed fixes. It complements IGA (enforcement/workflows) and SIEM (event detection).
Albus correlates HRIS, IdP, app, and usage signals; builds peer baselines; and flags outliers (toxic combos, dormant/orphaned access, privilege spikes). Every finding includes rationale so teams know why it’s risky and what to fix first.
That's up to you! Use preventive guardrails (JIT, time-bound, inactivity revocation) and/or require owner approval. Closed-loop workflows enforce removals, capture evidence, and sync back to ITSM and Lumos platform.
Yes. Service accounts, keys, workload/agent identities, and shadow IT/AI are discovered and monitored with entitlement-level context, so you can reduce blast radius across humans and machines.
Yes. Service accounts, keys, workload/agent identities, and shadow IT/AI are discovered and monitored with entitlement-level context, so you can reduce blast radius across humans and machines.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.



