Go From Identity Data to Decisions
Elevate your identity hygiene and posture analysis with interactive, customizable dashboards.

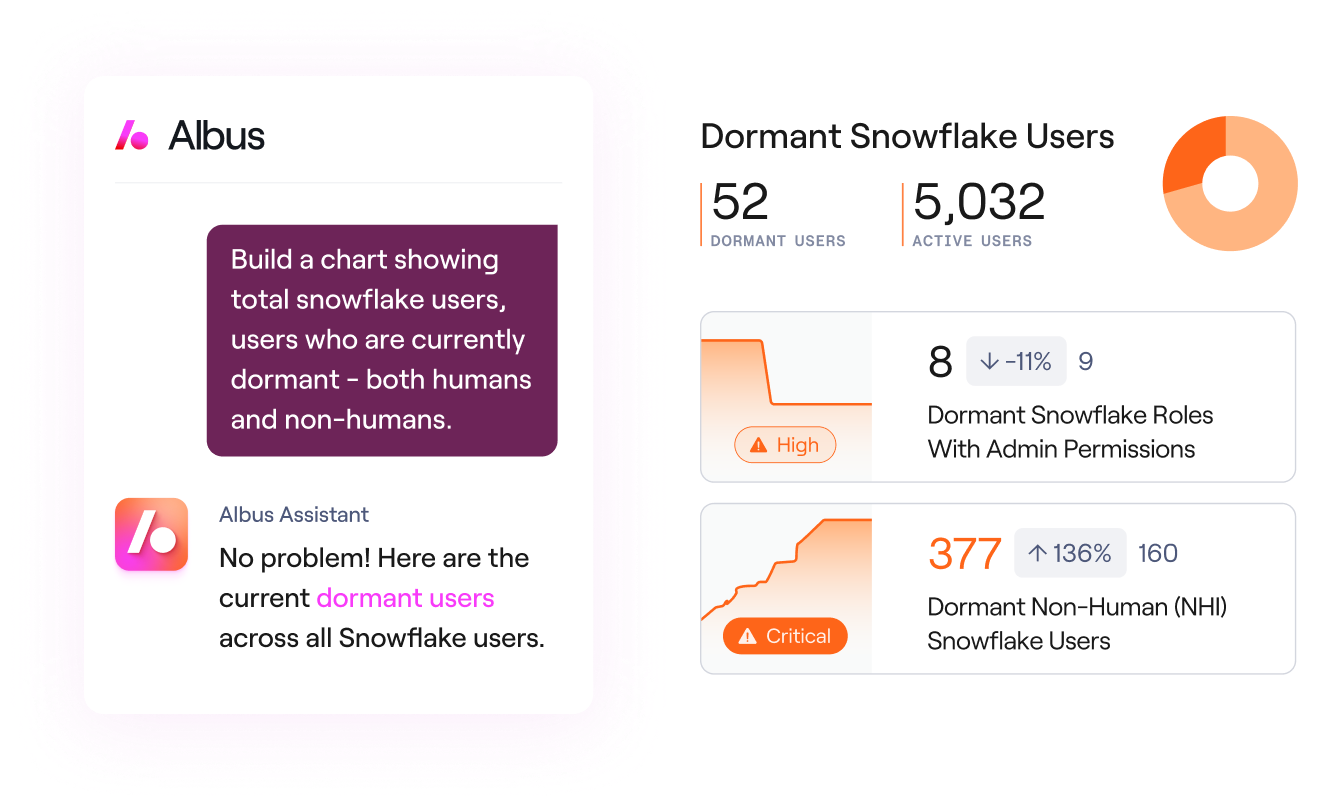







See Everything, Act With Confidence
Real-time visibility with AI-powered insights help you ask the right question and make the right decision instantly. Meet your business needs, empower users, and close risks fast.
Stay always up-to-date with real-time views
Empower app owners and department leaders with role-based, real-time views of the data they care about. No more request backlogs.
Automate reporting with interactive dashboards
No more long approval bottlenecks. Instantly grant right fine-grained access for the right amount of time to the right users.
Identify risks fast with AI-powered insights
Spot shadow IT, dormant accounts, over-privileged accounts fast, and then act with unified workflows - reducing risk and driving down costs.
Bring Agentic AI to Identity Analytics
Turn identity data into actions. Get answers to questions in plain English, build the right charts to tell the story, prioritize areas to focus and fix. No more spreadsheets or stale data.

Outcomes You Can Measure
Key Features
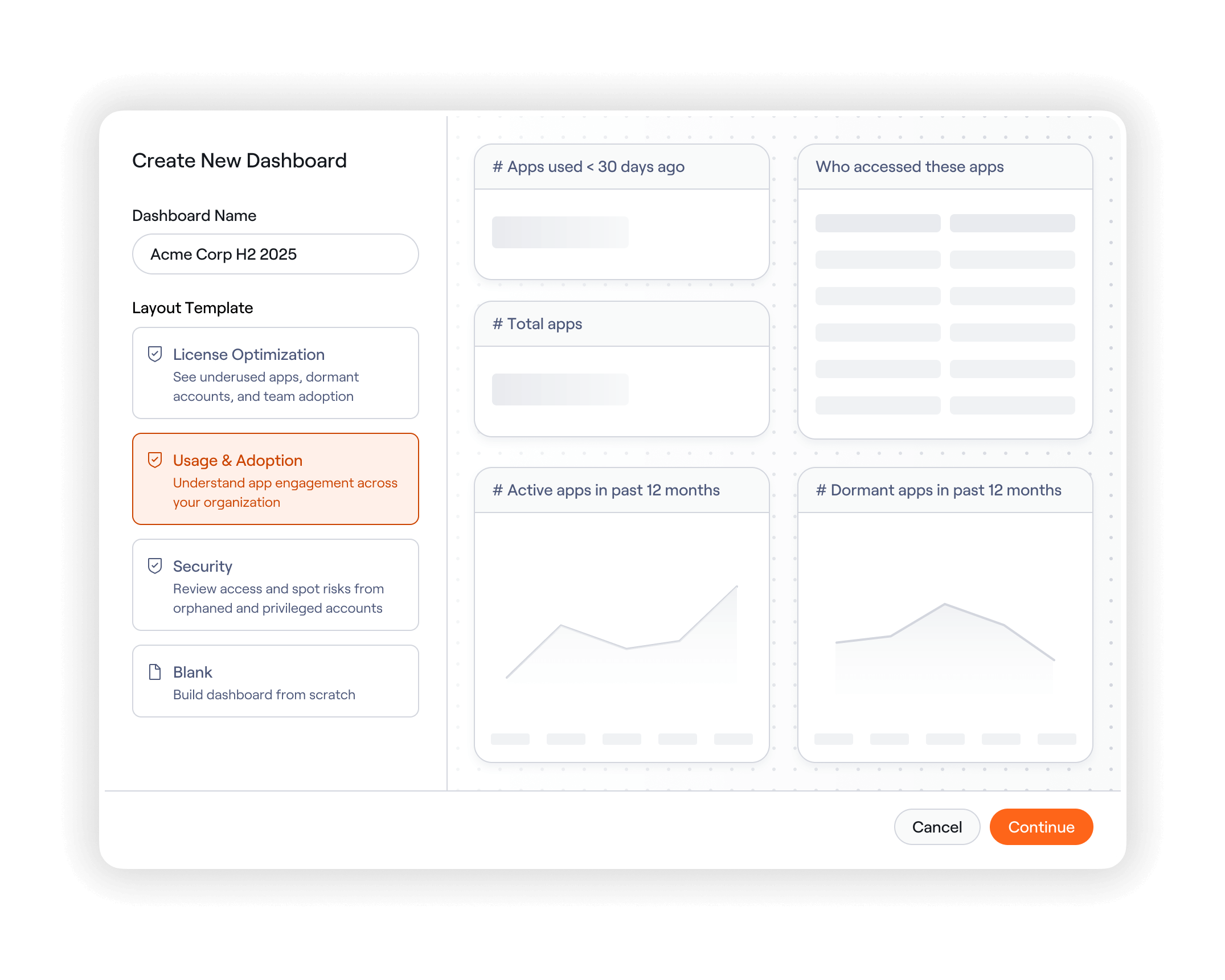
Customize dashboards to meet your needs
Start with out-of-the-box templates or build your own. Highlight license optimization, security posture, usage and adoption, shadow IT, and more. Filter by custom attributes, drill down from org to user and entitlement, and customize with a drag-and-drop layout.
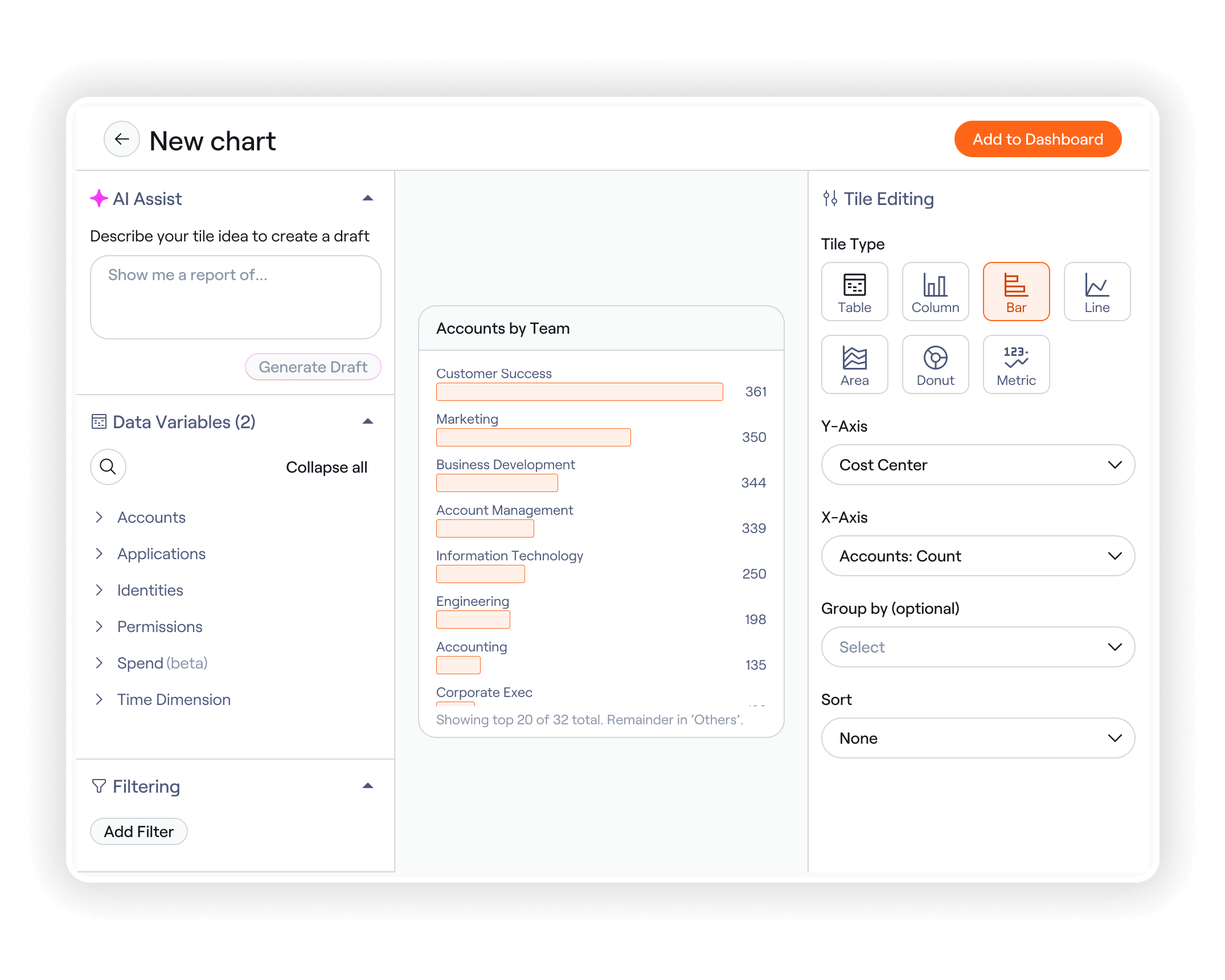
Build ready-to-use charts with AI in minutes
Ask natural language questions like, “Show inactive users by department,” and Albus automatically selects the right fields, filters, and visualization. Build charts in minutes with clear rationale and smart recommendations.
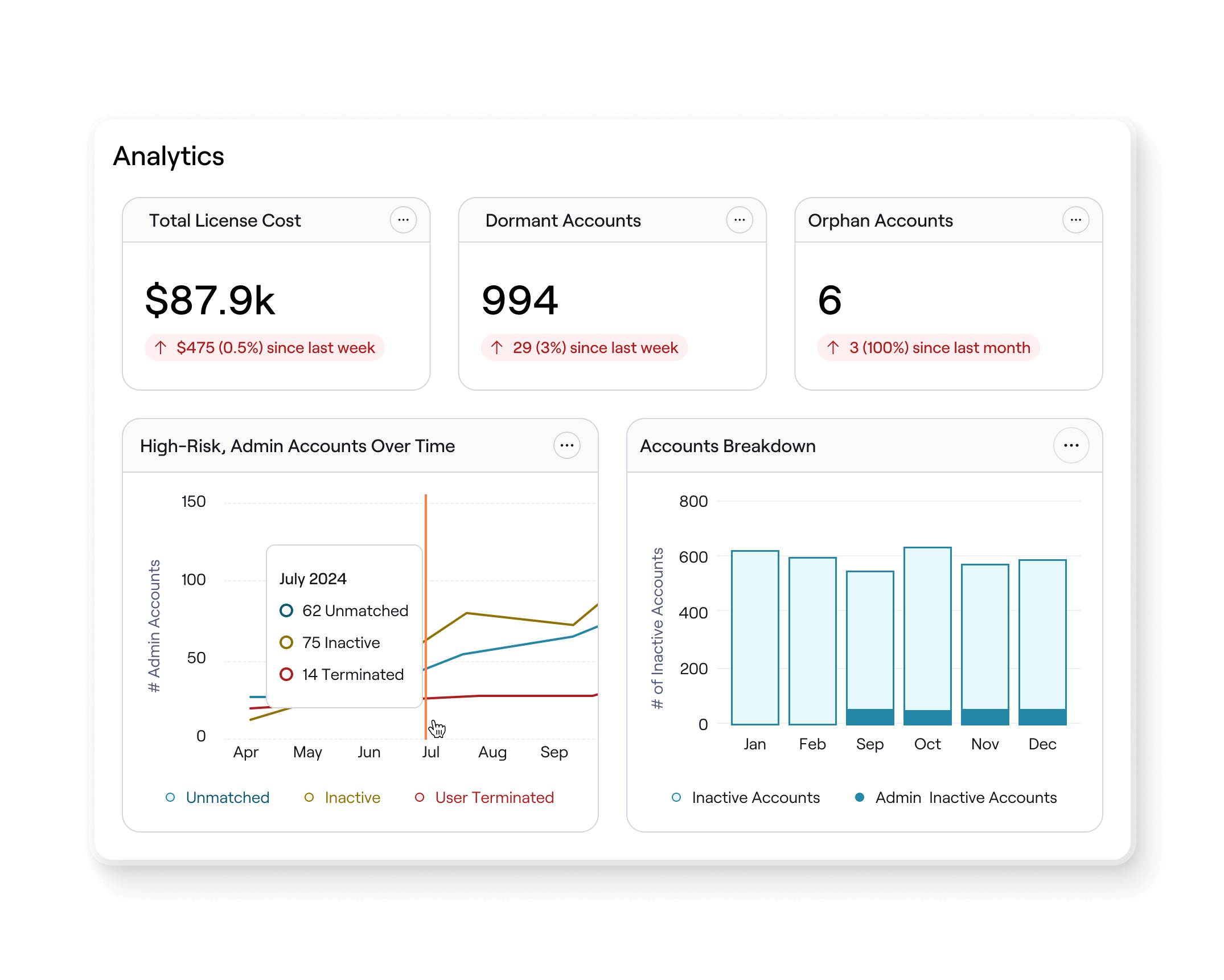
Share executive-grade reports that stay up-to-date
Save and share live links with leadership and stakeholders with real-time data updates. Control who sees what with role-based access and data scoping. Get answers fast without the manual burden.














Additional Resources
Frequently Asked Questions
Identity data refers to all the information associated with a user’s digital identity; such as their role, department, group memberships, application entitlements, login history, and access activity. This data is critical for making informed decisions about access controls, risk management, and compliance.
Lumos aggregates identity data across your HRIS, IdP, and 300+ apps, giving IT and security teams full visibility into who has access to what, why, and how that access is being used.
Identity analytics is the practice of analyzing identity and access data to uncover risks, enforce least-privilege access, and optimize governance decisions. It helps IT and security teams understand who has access to what, why they have it, and how that access is used; across all users, apps, and systems. With Lumos, identity analytics is powered by Albus, our AI identity agent, which delivers real-time insights into overprovisioned accounts, access anomalies, and policy gaps. This enables organizations to continuously improve access decisions, reduce security risk, and streamline compliance through data-driven governance.
Identity analytics tools help organizations analyze user access data to detect anomalies, enforce least-privilege access, and improve governance decisions. These tools surface risky entitlements, shadow IT usage, SoD violations, and overprovisioned accounts.
Lumos is a modern identity analytics platform powered by Albus AI, delivering real-time insights across all human and non-human identities. It helps IT and security teams take action with confidence by mapping access behavior to business context.
Key use cases for identity analytics include:
- Detecting over provisioned or orphaned accounts
- Enforcing least privilege and role clean-up
- Identifying shadow IT and redundant apps
- Supporting audit readiness with access trails
- Flagging risky access combinations and SoD violations
With Lumos, you can operationalize these use cases through automation: accelerating decision-making, streamlining access reviews, and reducing SaaS spend and security risk at scale.
Role-Based Access Control (RBAC) is a framework for managing user permissions based on job roles rather than assigning access individually. It simplifies access governance by mapping common permissions to standard roles like “Engineer” or “HR Manager.”
Lumos enhances RBAC by using AI to recommend and optimize roles based on real usage patterns. With Albus AI, teams can identify permission bloat, streamline roles, and implement cleaner, more scalable access policies that are aligned with least-privilege principles.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.



