Access Control Matrix: Definition, Components, Models, and Implementation Guide
An effective access control matrix ensures secure data management. Check out these essential examples and templates to streamline your access control processes.


An Access Control Matrix provides a centralized framework for defining which subjects (users, processes, roles) can perform specific operations on objects (files, databases, resources), ensuring robust authorization in any system. By mapping every subject–object pair to a set of permissions, the matrix delivers granular control, auditability, and policy clarity.
And access control is more critical than ever, as CrowdStrike’s Global Threat Report states that 52% of vulnerabilities in attacks came from initial access.
This guide explores the matrix’s origin, core components, comparisons with other models, and future trends.
What is an Access Control Matrix?
An Access Control Matrix (ACM) is a foundational security model used to define and enforce permissions within information systems. At its core, the matrix is a table where subjects (such as users, groups, or processes) are represented as rows, and objects (such as files, databases, applications, or resources) are represented as columns. The intersecting cells between rows and columns specify the operations or rights that each subject can perform on a given object: for example, read, write, execute, or delete.
This structured model provides a clear and formalized way to represent who has access to what within a system, reducing ambiguity and strengthening governance. Unlike informal or ad hoc permission management, the ACM serves as a single source of truth for authorization policies.
How the Access Control Matrix Differs from Other Models
The Access Control Matrix differs from traditional role-based or attribute-based approaches by offering direct visibility into the relationship between every subject and object.
While Role-Based Access Control (RBAC) abstracts permissions into roles and Attribute-Based Access Control (ABAC) bases decisions on attributes and policies, the ACM shows explicit mappings of access rights. This makes it particularly valuable for auditing, troubleshooting, and demonstrating compliance, even though large-scale systems often transform the matrix into more practical implementations (such as access control lists or capability tables).
Why Access Control Matrices Matter
For IT and security leaders, an Access Control Matrix helps ensure least-privilege enforcement, compliance with frameworks like SOX, HIPAA, or ISO 27001, and provides a foundation for identity governance automation.
By mapping entitlements at a granular level, organizations can minimize risks of excessive permissions, insider threats, and data breaches; all while ensuring that the right people (or processes) have the right access at the right time.
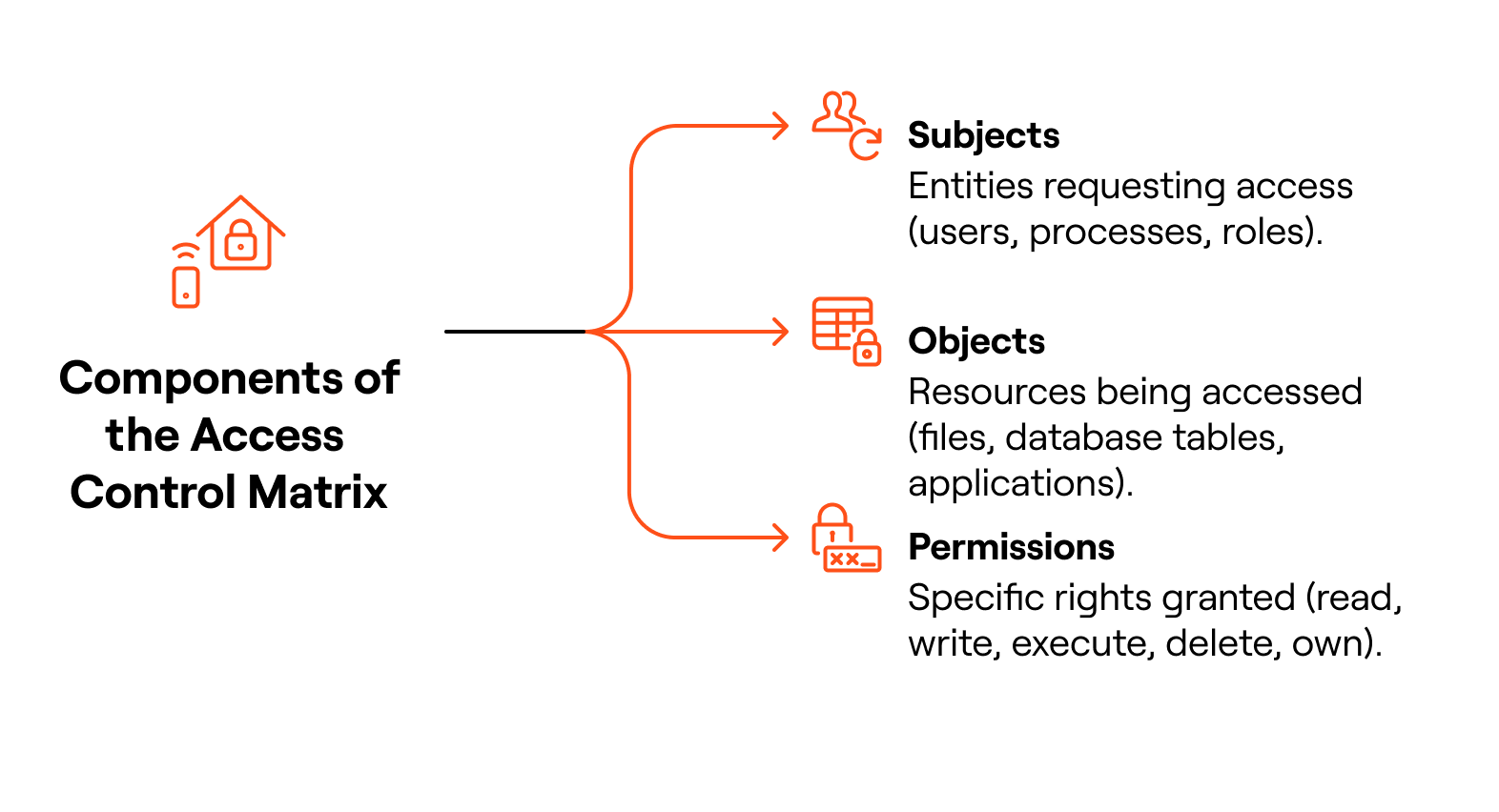
What are the primary components of an Access Control Matrix?
The Access Control Matrix (ACM) is built around three fundamental components: subjects, objects, and permissions. Together, these elements create a structured framework that defines who can do what within an information system.
- Subjects: Entities requesting access (users, processes, roles).
- Objects: Resources being accessed (files, database tables, applications).
- Permissions: Specific rights granted (read, write, execute, delete, own).
Subjects
Subjects are the active entities requesting access to resources. In most systems, this means users, such as employees, contractors, or customers. However, subjects can also include processes, applications, or roles that act on behalf of a user.
For example, a background service running database queries is also a subject, even though it’s not a human user. Subjects are critical because they anchor the matrix: each subject corresponds to a row that explicitly defines its relationship with every object in scope.
Objects
Objects represent the resources or assets being secured. These can be digital files, database tables, applications, network devices, or even APIs. Essentially, any item within an IT environment that requires controlled access can be modeled as an object. Objects are organized as columns in the ACM, and the intersection with subjects defines which actions are permitted.
By classifying objects carefully, organizations can align access controls with business priorities, for instance: protecting sensitive customer data more strictly than general corporate resources.
Permissions
Permissions are the actions a subject is authorized to perform on an object. Common permissions include read, write, execute, delete, or own. These rights are represented in the intersecting cells of the matrix, forming the operational rules that govern access.
For example, a subject might have “read” permission on a financial report but no “write” or “delete” rights. By explicitly mapping permissions, organizations can implement least-privilege access, reducing the attack surface and ensuring compliance with security and privacy regulations.
Why These Components Matter Together
The interaction between subjects, objects, and permissions provides a fine-grained, auditable map of access relationships. This structure helps IT and security teams answer key questions such as:
- Who has access to which systems or data?
- What specific actions can they perform?
- Where do excessive permissions pose risks?
By managing these components cohesively, organizations can strengthen security, streamline audits, and ensure compliance across complex, hybrid IT environments.
How Does an Access Control Matrix Compare to Other Access Control Models? ACL, RBAC, DAC, MAC, and ABAC
By contrasting the matrix with prevalent models, organizations can choose the approach best suited to their complexity, scalability, and compliance requirements.
What is the difference between an Access Control Matrix and an Access Control List (ACL)?
An Access Control Matrix offers a global, centralized view of all subject–object permissions, whereas an ACL attaches to each object individually, listing which subjects can access that object. The matrix excels at auditing all rights across a system, while ACLs simplify object-centric permission checks.
How does Role-Based Access Control (RBAC) differ from an Access Control Matrix?
RBAC introduces roles as an abstraction layer between subjects and permissions, grouping rights into roles that users assume. In contrast, a pure Access Control Matrix assigns permissions directly to each subject–object pair, offering maximum granularity but requiring careful management when scaling to many users.
How do Discretionary Access Control (DAC) and Mandatory Access Control (MAC) relate to the Access Control Matrix?
DAC lets resource owners grant or revoke rights at their discretion, mapping naturally to matrix cells updated by owners. MAC enforces system-wide policies based on sensitivity labels and clearance levels, which can be encoded into matrix entries to automate enforcement without owner intervention.
What is Attribute-Based Access Control (ABAC) and its relation to the Access Control Matrix?
ABAC evaluates attributes (environmental, user, resource) in real time to grant access, providing dynamic decisions beyond static matrix entries. Organizations often pre-compute common attribute combinations into matrix cells for performance, blending ABAC’s flexibility with matrix clarity.
How is an Access Control Matrix Implemented in Real-World Systems?
The Access Control Matrix (ACM) is more than just a theoretical security model; it underpins many practical authorization mechanisms used in today’s IT environments. While few systems display the ACM explicitly in a table format, its principles are embedded across operating systems, databases, and cloud platforms.
Operating Systems
In operating systems, ACM concepts are implemented through Access Control Lists (ACLs) and capability lists. Each file, folder, or system object can be thought of as a column in the matrix, while users and processes represent rows.
- ACLs: These list all the subjects that have permissions over an object, such as “user A can read, user B can write.”
- Capabilities: These represent rights associated with a subject, detailing which objects they can access and what actions they can perform.
By managing these lists, operating systems enforce fine-grained control over file access, process execution, and device interaction.
Databases
Databases apply ACM principles to regulate who can query, update, or manage records. Here, subjects are users or roles, objects are tables, views, or stored procedures, and permissions specify allowed operations like SELECT, INSERT, or DELETE.
- Role-based models: Many relational databases extend ACM with Role-Based Access Control (RBAC), where permissions are assigned to roles rather than individual users.
- Granular permissions: Some databases also allow column-level or row-level permissions, aligning closely with ACM’s fine-grained approach.
This ensures sensitive data, such as personally identifiable information (PII), is accessible only to authorized users.
Cloud Environments
Cloud platforms scale ACM principles across distributed and dynamic ecosystems. In services like AWS, Azure, or Google Cloud, subjects may include not just users, but also applications, APIs, and service accounts. Objects include cloud resources such as storage buckets, virtual machines, or databases.
- IAM Policies: Identity and Access Management (IAM) policies reflect ACM rules, mapping who can perform what action on which resource.
- Context-aware enforcement: Modern cloud environments extend ACM with conditional access, factoring in device health, geolocation, or risk scores before granting permissions.
- Scalability: Unlike static environments, cloud platforms rely on ACM logic embedded in APIs to automatically apply consistent policies across thousands of resources.
What Are the Key Benefits of an Access Control Matrix?
The Access Control Matrix (ACM) provides organizations with a structured, formalized approach to authorization management. While it may not always be visualized as a table in production environments, its conceptual framework delivers multiple advantages in security, compliance, and operational efficiency.
Granular, Centralized Permission Management
One of the most significant benefits of an ACM is its ability to centralize and standardize permissions across systems. Instead of scattering access rules across applications or relying on inconsistent manual processes, an ACM maps permissions in a single framework.
- Fine-grained control: Administrators can specify exactly which actions each subject can perform on each object, whether that’s read, write, execute, or delete.
- Consistency across environments: Whether managing operating systems, databases, or cloud platforms, ACM principles apply uniformly, reducing the likelihood of misconfigurations.
- Scalability: As organizations grow, centralized permission mapping reduces complexity by providing a clear model for extending access without compromising security.
Comprehensive Audit Trails
The ACM also enhances compliance and accountability by making it easier to track who has access to what and why.
- Visibility for auditors: Since the matrix structure outlines every relationship between subjects and objects, it serves as a transparent record of authorization logic.
- Change tracking: Administrators can log updates to the matrix—such as role assignments or permission revocations—creating a historical record of access decisions.
- Regulatory alignment: This traceability supports mandates from frameworks like SOX, HIPAA, or GDPR, where proving effective access governance is essential.
Policy Clarity
Another key advantage of the ACM is its ability to reduce ambiguity in access management.
- Clear representation of rules: By explicitly mapping permissions in cells, the ACM removes guesswork about who can access what resources.
- Improved communication: Security and IT teams can use the matrix as a common reference point when discussing access rights, avoiding misunderstandings caused by technical silos or inconsistent documentation.
- Support for principle of least privilege: The structured nature of the ACM makes it easier to identify excessive permissions and enforce tighter controls.
What Are the Common Challenges Surrounding the Access Control Matrix?
While the Access Control Matrix is a foundational framework for authorization management, its practical implementation is not without obstacles. Organizations that rely on ACM concepts often encounter operational and technical challenges, particularly as systems and users scale.
Scalability and Complexity of Large Data Sets
One of the primary challenges of the ACM is handling large-scale environments where the number of subjects and objects grows exponentially.
- Matrix size explosion: In enterprises with thousands of users and tens of thousands of resources, the resulting matrix can be massive, creating administrative overhead and potential performance issues.
- Difficult maintenance: As data volumes increase, mapping each permission at a fine-grained level becomes increasingly difficult. Without automation or supporting tools, IT teams may struggle to keep the matrix up to date.
- Operational inefficiency: In large environments, the complexity of manually maintaining an ACM often leads to shortcuts, such as granting broader permissions than necessary, undermining the principle of least privilege.
Frequent Changes to Subjects or Objects
Another challenge arises from the dynamic nature of modern organizations, where users, roles, and resources frequently change.
- High turnover and mobility: Employees joining, leaving, or shifting departments require constant updates to their access rights. An ACM that isn’t updated in near real time risks leaving accounts over-provisioned or under-provisioned.
- Application sprawl: As organizations adopt more SaaS applications and cloud services, new objects (resources) are continuously added, increasing the burden of keeping the matrix accurate.
- Error-prone updates: Frequent changes raise the likelihood of misconfigurations, especially if updates are handled manually. A missed deprovisioning step, for instance, can leave behind orphaned accounts that attackers may exploit.
How Does the Access Control Matrix Support Modern Security Frameworks?
The Access Control Matrix (ACM) remains a powerful conceptual tool, even as organizations adopt advanced security frameworks. Its ability to represent who can access what, and under which conditions, aligns naturally with modern identity, trust, and compliance practices. By mapping permissions clearly, the ACM provides both a foundation and a lens through which IT and security teams can enforce evolving policies.
Identity and Access Management (IAM)
In IAM, the ACM serves as a blueprint for assigning and managing permissions across systems. It supports:
- Centralized governance: By consolidating subject-object-permission relationships, the ACM simplifies entitlement reviews and access recertifications.
- Role design and refinement: Mapping permissions against roles helps identify redundancies and supports least-privilege enforcement.
- User lifecycle alignment: As joiners, movers, and leavers cycle through the organization, the ACM provides clarity into required access adjustments.
This alignment makes it easier for IAM platforms to automate provisioning and ensure consistency across complex environments.
Zero Trust
The Zero Trust security model requires continuous verification and least-privilege enforcement, principles that align directly with the ACM.
- Context-aware enforcement: By adding conditions such as device type or location to the traditional subject-object matrix, organizations can translate ACM concepts into dynamic access policies.
- Microsegmentation: The ACM helps define which users and workloads may interact, supporting tighter network and application boundaries.
- Adaptive response: In a Zero Trust architecture, ACM principles evolve beyond static rules into policies enforced in real time based on contextual risk.
In short, the ACM provides the granular visibility needed to implement Zero Trust at scale.
Compliance
From SOX and HIPAA to ISO 27001, compliance frameworks consistently demand proof of access governance. The ACM supports this by:
- Audit-ready visibility: Clearly mapping subjects, objects, and permissions makes it easy to demonstrate who had access to what at any point in time.
- Policy traceability: Regulators require evidence of least-privilege enforcement, separation of duties, and timely revocation of access. The ACM structure provides this evidence in an accessible format.
- Reducing audit fatigue: Centralized mapping reduces the manual work of reconciling permissions across disparate systems, streamlining compliance reporting.
Future Trends and Innovations Related to the Access Control Matrix
As security architectures evolve, the Access Control Matrix is being reimagined through modern innovations that extend its principles into dynamic, scalable, and tamper-resistant systems. These advancements ensure that the ACM continues to remain relevant in increasingly complex IT and cloud-native environments.
AI-driven Permission Recommendations
Artificial Intelligence (AI) is transforming how access rights are assigned and reviewed. Instead of relying solely on static policies, AI models analyze behavioral data, usage trends, and organizational role structures to recommend the least-privilege permissions.
- Role mining: AI helps identify overlapping access rights across users and automatically groups them into optimized roles.
- Anomaly detection: By learning typical access patterns, AI highlights excessive privileges or risky entitlements that deviate from the baseline.
- Predictive governance: Future access needs can be forecasted, reducing the manual burden on IT and security teams during onboarding or role changes.
This predictive capability enhances both efficiency and accuracy while lowering the risk of access creep.
Microservice-native Policy Orchestration
With the rise of microservices and containerized environments, policy enforcement is moving closer to workloads and APIs. Instead of centralizing all logic in static tables, ACM concepts are now embedded within service meshes and orchestration frameworks.
- Dynamic enforcement: Policies are applied at runtime, tailored to the microservice, user identity, and request context.
- Granular segmentation: Each microservice defines its own access rules but aligns with enterprise-wide ACM principles for consistency.
- Scalable governance: This approach supports hybrid and multi-cloud ecosystems, where workloads must interoperate across diverse platforms.
Policy orchestration enables ACM models to stay effective in distributed, cloud-native infrastructures where static mappings would otherwise fail.
Blockchain-backed Immutable Audit Trails
Auditability is central to the ACM model, and blockchain technology is emerging as a powerful tool to strengthen it.
- Tamper-resistant logs: Recording access decisions and changes on a distributed ledger ensures immutable, verifiable audit trails.
- Transparency and trust: Regulators and auditors can verify compliance without relying solely on internal system logs.
- Decentralized enforcement: Smart contracts may one day enforce ACM-based policies directly, reducing reliance on central authorities.
By combining ACM principles with blockchain’s immutability, organizations gain enhanced accountability and assurance against insider tampering or post-incident disputes.
Modernizing Access Control with Lumos
The traditional Access Control Matrix model laid the groundwork for structured authorization by mapping users, roles, and resources. But in today’s dynamic IT landscapes – spanning cloud, hybrid, and distributed environments – a static matrix no longer suffices. To stay effective, access control must evolve with automation, intelligence, and real-time alignment.
Lumos bridges this evolution. We take the principles of ACM and embed them into a modern identity governance engine: layered with AI, lifecycle automation, and deep visibility. With Lumos, access policies become living, enforceable rules. Joiner‑mover‑leaver workflows trigger provisioning or deprovisioning automatically; AppStore and just-in-time access ensure users get exactly what they need when they need it; and entitlement-level reporting surfaces risks instantly. This unification of governance, control, and automation transforms access control from a static model into a real-time strategic capability.
As identity-based threats grow in frequency and sophistication, legacy IAM tools buckle under complexity. Lumos helps organizations break free. With granular policy enforcement, continuous audit readiness, and automation that scales, Lumos enables IT and security leaders to modernize access without sacrificing efficiency or security posture.
If you’re ready to move beyond manual access governance and deploy truly adaptive control, schedule a demo with Lumos. Let us show you how we merge automation, least privilege, and full visibility into one streamlined identity platform.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.




