Best ConductorOne Alternatives and Competitors in 2025
Discover the 12 best ConductorOne alternatives and competitors in 2025. Compare features, pricing, automation capabilities, and identity governance strengths to find the right IAM and IGA platform for your organization.


ConductorOne is an identity security and governance platform focused on automating access reviews, managing least-privilege permissions, and improving compliance across hybrid environments. While it delivers capabilities for mid-market and enterprise teams, some organizations are now exploring alternatives that offer greater scalability, broader integration options, or more customizable workflows for complex governance needs.
In this guide, we’ll explore the top ConductorOne alternatives and competitors in 2025, analyzing what makes each solution unique and how they compare across automation, AI-driven governance, and identity lifecycle management. Whether your priorities include improving audit readiness, reducing manual access review workloads, or consolidating identity tools, these platforms provide diverse options to help you enhance security, streamline operations, and maintain full visibility across your digital ecosystem.
Why Companies Consider ConductorOne Competitors
As identity governance and access management (IGA) evolve toward greater automation and intelligence, many IT and security leaders are re-evaluating their current tools. ConductorOne, known for its focus on automating access reviews and simplifying least-privilege governance, has gained strong traction among mid-market and enterprise organizations. However, some teams are beginning to explore alternative platforms that offer broader integration capabilities, more advanced policy automation, or greater scalability for complex environments.
Below are three key factors driving companies to consider competitors to ConductorOne in 2025:
- High Total Cost of Ownership
- Complexity and Setup Challenges
- Integration and Ecosystem Limitations
High Total Cost of Ownership
While ConductorOne delivers access governance features, the total cost of ownership (TCO) can escalate as organizations expand. Pricing often scales with user volume, connected systems, and advanced feature sets, which can make ongoing costs difficult to predict.
Mid-market companies, in particular, report challenges aligning budgets with their growth trajectory; especially when factoring in professional services, implementation time, and support packages. As identity environments grow more distributed across SaaS and multi-cloud platforms, leaders are increasingly drawn to solutions that provide transparent, modular pricing or pay-as-you-scale models. These flexible approaches reduce financial strain and make it easier to adapt IAM investments to changing workforce or compliance needs.
Complexity and Setup Challenges
Although ConductorOne emphasizes usability, its depth of functionality can introduce complex setup requirements, particularly for enterprises integrating dozens of applications or custom systems. Configuration of workflows, policies, and connectors may require specialized technical knowledge or extensive onboarding support.
From an operational standpoint, IT teams also note that maintaining integrations and managing frequent policy updates can add ongoing administrative overhead. Smaller teams may find it difficult to balance the learning curve of a sophisticated governance platform with day-to-day access control responsibilities.
In response, many organizations are turning to competitors that prioritize faster deployment timelines, pre-built integrations, and low-code policy customization, enabling them to achieve governance automation without prolonged implementation cycles.
Integration and Ecosystem Limitations
ConductorOne supports a growing number of applications and identity systems, yet some enterprises seek broader interoperability across legacy environments, cloud infrastructures, and DevOps toolchains. As identity governance extends beyond traditional HR and SaaS boundaries, businesses increasingly require API-first platforms capable of connecting seamlessly to both modern and on-premise systems.
Alternatives to ConductorOne often emphasize open standards (such as SCIM, OAuth 2.0, and OIDC) and deeper integration ecosystems, allowing organizations to embed governance logic directly into CI/CD pipelines, ITSM tools, and collaboration platforms. This flexibility enables more dynamic identity management and real-time policy enforcement across hybrid environments.
12 Best ConductorOne Alternatives in 2025
As the IGA landscape grows, organizations are looking for platforms that provide greater automation, flexibility, and transparency than ever before. While ConductorOne has earned recognition for its focus on automating access reviews and enforcing least-privilege principles, many IT and security leaders are evaluating alternatives that offer broader governance capabilities, deeper integrations, or enhanced scalability across complex enterprise environments.
The following list highlights the top 12 ConductorOne alternatives and competitors in 2025, each offering distinct advantages in governance automation, integration breadth, pricing flexibility, and ease of deployment.
- Lumos
- Okta
- Auth0
- Microsoft Entra ID
- SailPoint Identity Security Cloud
- Saviynt Identity Cloud
- Omada Identity
- One Identity
- Ping Identity Platform
- IBM Security Verify Governance
- Rippling Identity & Access
- Opal Security
1. Lumos
- G2 Rating: 4.8 / 5
- Pricing: Starts at ~$1/user/month (varies by feature set)
Lumos is the first autonomous identity platform, designed to unify discovery, governance, and automation under one intelligent system. Rather than treating access management as a fragmented collection of tools, Lumos provides a single platform where IT and security teams gain full visibility and control over who has access to what, when, and why.
Built for modern enterprises, Lumos helps teams shrink audit fatigue, reduce entitlement sprawl, and enforce least privilege at scale. The platform combines access requests, lifecycle management, reviews, and policy automation into one cohesive workflow, dramatically simplifying governance and compliance for organizations of all sizes.
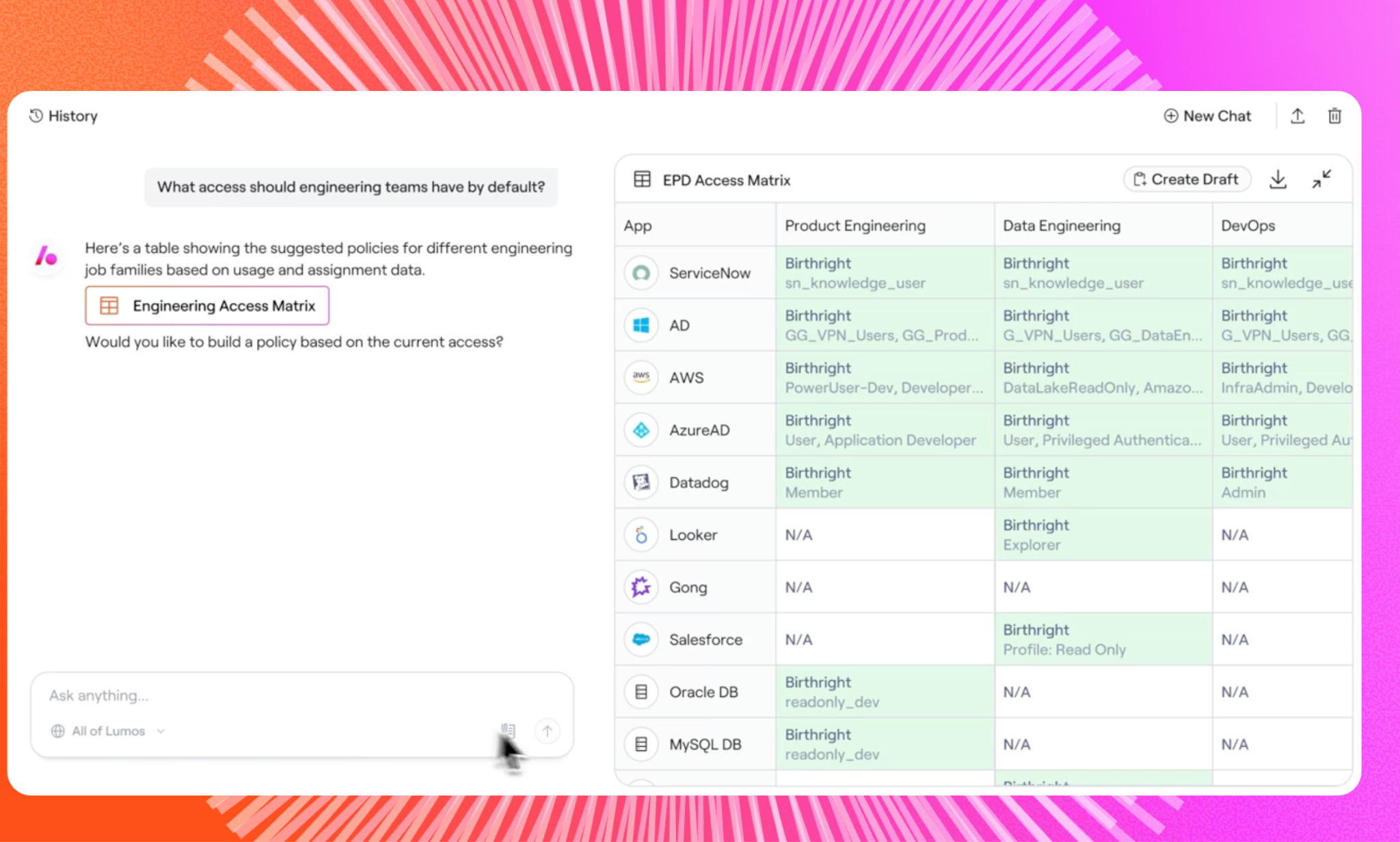
Features:
- Centralized Access Visibility: Lumos provides real-time, entitlement-level visibility across HR systems, IdPs, SaaS apps, and on-prem infrastructure. IT leaders can instantly answer critical audit questions – without waiting on spreadsheets or manual data pulls.
- Accelerated and Intelligent Access Reviews: Lumos automates access review campaigns with built-in policy logic, SoD violation detection, and customizable reviewer workflows. Audit-ready reporting ensures compliance without draining team bandwidth.
- End-to-End Identity Lifecycle Management: From onboarding to offboarding, Lumos automates access provisioning and deprovisioning with fine-grained RBAC and ABAC policies. This ensures users get the right access at the right time; and lose it when they shouldn’t have it.
- Seamless User Experience: Lumos integrates directly with the tools employees already use, including Slack, Microsoft Teams, ITSM systems, and CLI. Self-service access requests are routed automatically through approval workflows, reducing tickets and friction.
- Policy Mining and Role Engineering: Lumos intelligently analyzes access data to recommend optimal roles, eliminate redundancies, and tighten privileges across your environment.
- Agile, Low-Overhead Implementation: Unlike traditional IGA suites, Lumos deploys quickly, scales easily, and minimizes ongoing maintenance requirements: delivering faster time to value.
Lumos takes access governance beyond automation; embedding AI-driven intelligence and autonomous policy execution into every aspect of identity management. Organizations looking for a more complete, flexible, and faster-to-deploy alternative to ConductorOne will find Lumos especially compelling. It’s built for teams that need full governance visibility, lightweight implementation, and proactive risk reduction – all without the heavy lift of legacy IGA solutions.
Ready to see Lumos in action? Book a demo to explore how Lumos simplifies governance, reduces audit fatigue, and scales identity management for the modern enterprise.
2. Okta
- G2 Rating: 4.4 / 5
- Pricing: Starts at approximately $2 per user/month; enterprise pricing available based on deployment and feature set
Okta is an established name in identity and access management (IAM), offering a mature platform for authentication, provisioning, and governance across cloud and on-premises environments. With a broad range of integrations and enterprise-ready security features, Okta helps organizations centralize identity management while enabling seamless user experiences through single sign-on (SSO) and adaptive multi-factor authentication (MFA).
Features:
- Universal Directory and Centralized Identity Management: Okta provides a unified platform to manage user identities and attributes across SaaS, cloud, and on-prem systems with granular control.
- Single Sign-On (SSO): Streamlines user authentication across thousands of applications with pre-built connectors and support for SAML, OAuth 2.0, and OpenID Connect.
- Adaptive Multi-Factor Authentication (MFA): Protects user access with contextual MFA policies based on device, location, and behavior analytics.
- Lifecycle Management: Automates onboarding, provisioning, and deprovisioning processes through integrations with major HR systems and directories.
- Zero Trust Security Framework: Okta enforces least-privilege access and continuous verification, aligning identity management with modern Zero Trust architectures.
- Integration Ecosystem: Supports over 7,000 pre-built integrations, making it highly compatible with existing enterprise tools and workflows.
Okta provides a mature identity infrastructure with deep SSO and MFA capabilities but may require more administrative oversight and configuration for governance use cases.
3. JumpCloud
- G2 Rating: 4.5 / 5
- Pricing: Free tier available; paid plans start around $11/user/month depending on modules and device management needs
JumpCloud is an open directory platform that unifies identity, device, and access management into a single cloud-based system. Unlike traditional IAM providers that focus primarily on authentication and SSO, JumpCloud delivers a broader approach; combining user identity, endpoint management, and conditional access policies under one roof.
Features:
- Cloud Directory Services: JumpCloud replaces or extends Active Directory, enabling centralized management of users, groups, and authentication across on-prem and cloud environments.
- Unified Device Management: Offers built-in MDM for Windows, macOS, and Linux, with policies for patching, configuration, and conditional access tied directly to identity.
- SSO & MFA: Provides single sign-on to SaaS applications, combined with TOTP, push-based MFA, and conditional access rules for device posture, location, and user risk.
- Zero Trust Security Controls: Enforces least privilege through identity-bound device trust, passwordless workflows, and continuous risk-based authentication.
- Cross-Platform Compatibility: Works seamlessly across heterogeneous environments, making it ideal for organizations with mixed OS, cloud, and network configurations.
- API-Driven Integrations: Supports SCIM provisioning, LDAP-as-a-service, RADIUS, and APIs for custom workflows and deeper automation.
JumpCloud is a strong fit for organizations seeking a simplified approach to identity, access, and device governance. JumpCloud stands out for its ease of deployment, integrated device management, and ability to consolidate multiple IT tools into a single platform.
4. Microsoft Entra ID
- G2 Rating: 4.4 / 5
- Pricing: Free tier available; paid tiers (Premium P1/P2) start at ~$6–$9/user/month
Microsoft Entra ID (formerly Azure Active Directory) is one of the most widely adopted cloud identity platforms, offering authentication, access control, and governance capabilities. As part of the larger Microsoft Entra suite, it provides deep integration with Microsoft 365, Azure, and thousands of SaaS applications.

Features:
- Enterprise Single Sign-On (SSO): Supports thousands of pre-integrated applications through the Azure App Gallery, leveraging standards like SAML, OAuth, and OpenID Connect for seamless authentication.
- Adaptive Multi-Factor Authentication: Enforces MFA based on risk, user context, device state, and session signals, powered by Microsoft’s identity protection analytics.
- Conditional Access Policies: Fine-grained, policy-based controls that evaluate user risk, device posture, location, and compliance signals in real time before granting access.
- Identity Governance and Entitlement Management: Provides workflows for lifecycle management, access package provisioning, user access reviews, and automated governance across SaaS and Azure resources.
- Hybrid Identity Support: Bridges on-prem Active Directory with cloud identity through Azure AD Connect, enabling unified management for hybrid environments.
- Deep Microsoft Ecosystem Integration: Native integration with Microsoft 365, Teams, Azure, Power Platform, and Intune, reducing friction for organizations standardized on Microsoft tools.
Microsoft Entra ID works well in enterprise settings that require scalable identity governance, strong cloud integration, and extensive security intelligence. Compared to ConductorOne, Entra ID delivers broader identity protection and seamless interoperability across the Microsoft ecosystem, though it may require more complex configuration for organizations not already invested in Azure or M365.
5. SailPoint
- G2 Rating: 4.2 / 5
- Pricing: Custom pricing based on organization size, deployment model, and governance modules
SailPoint is one of the most established vendors in identity governance and administration (IGA), offering lifecycle automation, and compliance controls for large and highly regulated enterprises. SailPoint is often considered a top ConductorOne alternative for organizations that prioritize governance, risk reduction, and audit readiness above lightweight authentication workflows.

Features:
- Advanced Identity Governance: Centralizes governance controls with automated access certifications, risk scoring, and auditing tools built to meet strict regulatory frameworks like SOX, HIPAA, and GDPR.
- Identity Lifecycle Management: Automates onboarding, offboarding, and access changes using policy-driven workflows, ensuring users maintain appropriate access as roles evolve.
- Role Mining and Access Modeling: Uses analytics to discover patterns across entitlements, enabling organizations to build cleaner role structures and reduce permission sprawl.
- Separation of Duties (SoD) Controls: Enforces SoD rules across applications to prevent toxic access combinations, with automated violation detection and remediation workflows.
- Extensive Integration Ecosystem: Offers connectors for thousands of SaaS apps, HR systems, directories, and cloud providers, supporting large enterprises with diverse tech stacks.
- Deployment Flexibility: Available as a SaaS platform (SailPoint Identity Security Cloud) or as a self-hosted solution for organizations with strict data residency or customization needs.
SailPoint fits in environments where governance, compliance, and risk reduction are the highest priorities. Compared to ConductorOne, SailPoint delivers broader enterprise-grade governance features and deeper compliance automation, though it often requires more complex setup, longer deployment timelines, and dedicated admin resources.
6. Saviynt
- G2 Rating: 4.3 / 5
- Pricing: Custom pricing based on user volume, governance modules, and deployment needs
Saviynt is an enterprise Identity Governance and Administration (IGA) platform known for its compliance, risk analytics, and cloud-focused access governance capabilities. As a modern, cloud-native alternative to ConductorOne, Saviynt provides extensive controls for managing entitlements, securing privileged identities, and enforcing regulatory standards across hybrid and multi-cloud environments.
Features:
- Cloud-Native Identity Governance: Saviynt’s platform is built for modern cloud environments, offering identity lifecycle automation, access certification, and continuous compliance monitoring without heavy on-prem infrastructure.
- Risk-Aware Access Controls: Uses analytics and machine learning to score identity risk, detect anomalous access behavior, and highlight toxic entitlement combinations before they lead to audit or security issues.
- Privileged Access Management (PAM): Provides JIT privileged access, session monitoring, and vault-less credential management – allowing organizations to consolidate PAM and IGA capabilities into one platform.
- Third-Party and Vendor Access Governance: Extends governance to contractors, vendors, and external partners through onboarding workflows, time-bound access, and identity proofing.
- Separation of Duties (SoD) and Compliance Automation: Includes out-of-the-box SoD rulesets and controls for frameworks like SOX, HIPAA, PCI, and GDPR, helping teams streamline audit preparation.
- Extensive Integrations: Supports thousands of applications and cloud providers with granular entitlement-level visibility.
Saviynt is a viable alternative to ConductorOne for enterprises that prioritize governance rigor, deep entitlement insights, and compliance automation. While it offers broader IGA and PAM functionality than most competitors, its platform can be more complex to deploy and may require experienced administrators or implementation partners.
7. Omada Identity
- G2 Rating: 4.2 / 5
- Pricing: Custom pricing based on user count, governance modules, and deployment model
Omada Identity is a governance-focused Identity Governance and Administration (IGA) platform built to help enterprises manage the full identity lifecycle, enforce access policies, and maintain regulatory compliance at scale.
Features:
- Identity Lifecycle Automation: Automates joiner, mover, and leaver processes with policy-driven workflows that ensure users receive the correct access based on roles, departments, or attributes.
- Advanced Access Governance: Offers capabilities for access certification, policy enforcement, and segregation of duties (SoD) to reduce risk and support audit readiness.
- Role and Policy Management: Includes robust role mining, modeling, and maintenance tools designed to help enterprises define and govern access roles at scale.
- Compliance and Audit Support: Provides detailed reporting, risk scoring, and compliance dashboards aligned with SOX, GDPR, ISO, and other regulatory frameworks.
- Extensive Integrations: Supports a broad ecosystem of applications, directories, and cloud services with entitlement-level visibility and connector templates.
- Hybrid Deployment Options: Available as SaaS, on-premises, or hybrid, enabling organizations to choose the architecture that best supports their environment.
Omada Identity is a sound alternative to ConductorOne for organizations that need structured governance, repeatable identity processes, and a mature compliance-oriented IGA platform. While it offers more out-of-the-box governance capabilities than modern lightweight platforms, it may require more administrative oversight and longer implementation timelines.
8. One Identity
- G2 Rating: 4 / 5
- Pricing: Custom pricing based on deployment model, modules (IGA, PAM, AD management), and enterprise size
One Identity is an identity security platform that unifies identity governance, privileged access management (PAM), and Active Directory (AD) administration. With strong modular capabilities, it allows organizations to adopt the components they need while maintaining a cohesive identity security strategy.
Features:
- Unified Identity Security Portfolio: Combines IGA, PAM, AD management, and identity analytics into one ecosystem, reducing tool fragmentation and simplifying operations.
- Identity Governance & Administration (IGA): Provides role-based access control (RBAC), automated provisioning, access certifications, and SoD enforcement for large enterprises with complex governance needs.
- Privileged Access Management: Offers session monitoring, least-privilege enforcement, and credential vaulting to protect high-risk privileged accounts and reduce identity blast radius.
- Active Directory & Azure AD Management: Delivers robust delegation, automation, and governance for directory services, enabling scalable and secure management of users, groups, and entitlements.
- Compliance & Audit Support: Provides extensive reporting, audit trails, and policy enforcement aligned with SOX, HIPAA, GDPR, and other compliance frameworks.
- Flexible Deployment Options: Available on-premises, hybrid, or SaaS, making it adaptable to organizations with legacy infrastructure or complex cloud adoption roadmaps.
One Identity is a solid alternative to ConductorOne for organizations that need a mature, enterprise-grade identity platform with deep governance and privileged access controls. Its comprehensive capabilities make it well-suited for large, highly regulated enterprises that require tight policy enforcement and extensive control over directory services.
9. Ping Identity
- G2 Rating: 4.3 / 5
- Pricing: Custom pricing based on organization size, deployment model, and selected identity modules
Ping Identity is an enterprise-grade identity and access management platform designed for large organizations that require advanced authentication, federation, and access control across hybrid and multi-cloud environments. Known for its flexibility and strong support for open standards, Ping offers deeper customization and architectural control than many modern identity platforms.
Features:
- Enterprise-Grade SSO & Federation: Supports SAML, OAuth 2.0, OpenID Connect, WS-Federation, and SCIM, enabling seamless SSO across SaaS, legacy, and on-premise applications.
- Adaptive Multi-Factor Authentication (MFA): Uses device posture, risk signals, location, and behavior analytics to enforce context-aware MFA without disrupting user productivity.
- Advanced Access Policy Controls: Offers granular, attribute-based authorization (ABAC) and centralized policy enforcement for complex enterprise access scenarios.
- Orchestration & Workflow Automation: PingOne DaVinci provides low-code orchestration to automate identity flows, user journeys, risk checks, and identity verifications.
- Hybrid and Multi-Cloud Support: Suitable for organizations operating across AWS, Google Cloud, Azure, and private cloud environments with flexible deployment models (SaaS, on-prem, hybrid).
- Extensive Enterprise Integrations: Thousands of pre-built connectors plus rich APIs allow Ping to integrate with custom, legacy, or highly regulated systems that require fine-tuned control.
Ping Identity is a solid option for enterprises needing an identity platform with deep authentication, federation, and adaptive access capabilities. While it may require more administrative expertise and heavier initial configuration, Ping offers flexibility for large-scale identity architectures where security, performance, and integration depth are critical.
10. IBM Verify
- G2 Rating: 4.2 / 5
- Pricing: Custom pricing based on deployment model, feature selection, and enterprise scale
IBM Verify is a comprehensive identity and access management platform built for large, complex enterprises that require strong governance, thorough authentication, and advanced threat detection. As organizations compare ConductorOne alternatives, IBM Verify stands out with its deep analytics, AI-enhanced risk scoring, and flexible support for hybrid and multi-cloud architectures.

Features:
- AI-Driven Risk Assessment: IBM leverages behavioral biometrics, device insights, and machine learning–powered risk scoring to continuously evaluate authentication attempts and user actions.
- Strong Access Management (SSO & MFA): Provides adaptive MFA, passwordless authentication options, and secure SSO using SAML, OIDC, OAuth, FIDO2, and other open standards.
- Identity Governance & Access Certification: Includes role management, attestation workflows, separation-of-duties (SoD) checks, and automated remediation tools to help enterprises maintain compliance.
- Privileged Access Behavioral Monitoring: Tracks privileged sessions in real time to detect anomalies, prevent misuse, and support forensic reviews.
- Flexible Deployment Options: Available as SaaS, self-managed software, or hybrid deployments for organizations with on-prem requirements or strict regulatory controls.
- Integration with Security Operations and SIEM: Connects natively with IBM QRadar and other leading SIEM/SOAR platforms, enabling end-to-end identity threat detection and automated incident response.
IBM Verify is a good option for large enterprises, highly regulated industries, or security-first organizations that need deep analytics, hybrid support, and fully integrated governance capabilities.
11. Rippling
- G2 Rating: 4.8 / 5
- Pricing: Starts at ~$8/user/month for core workforce management; identity and security modules priced separately
Rippling is a unified workforce, IT, and identity management platform designed to centralize employee operations within a single system. Unlike ConductorOne, which focuses primarily on identity governance and access workflows, Rippling approaches identity from the employee lifecycle perspective, automating provisioning, IT operations, and access governance as part of a broader workforce automation platform.
Features:
- Unified Workforce Graph: Rippling uses a centralized data model that ties every role, system, and identity attribute to the employee record, enabling instant updates across the IT and HR stack.
- Automatic Provisioning & Deprovisioning: Employees are automatically assigned (or removed from) apps, groups, and permissions based on department, role, location, seniority, and custom logic.
- App & Device Management in One Platform: Unlike traditional IAM vendors, Rippling combines identity with mobile device management (MDM), endpoint security, and HRIS—giving IT teams full control over devices and access from a single dashboard.
- Role-Based and Attribute-Based Access Rules: Supports dynamic provisioning policies that adjust user access based on real-time employment data. Great for fast-scaling teams with frequent role changes.
- Audit-Ready Reporting: Rippling automatically logs app assignments, access changes, and lifecycle events, simplifying compliance for SOC 2, SOX, HIPAA, and other frameworks.
- Pre-Built Integrations: Offers 500+ direct integrations for SaaS apps, SSO providers, and system directories, reducing setup friction and enabling broad ecosystem coverage.
Rippling is an option for organizations that want to consolidate HR, IT, and IAM under one modern platform. While ConductorOne provides deeper governance, review workflows, and access intelligence, Rippling excels at lifecycle automation, rapid provisioning, and eliminating tool sprawl.
12. Opal Security
- G2 Rating: 4.7 / 5
- Pricing: Custom pricing based on enterprise size, integrations, and governance modules
Opal Security is an identity governance and access management platform focused on bringing least privilege, access visibility, and automated access workflows to modern, fast-moving engineering and cloud environments. Designed with a strong emphasis on developer experience and infrastructure access governance, Opal helps organizations reduce standing privileges, streamline access requests, and improve compliance readiness across SaaS, IaaS, and internal systems.
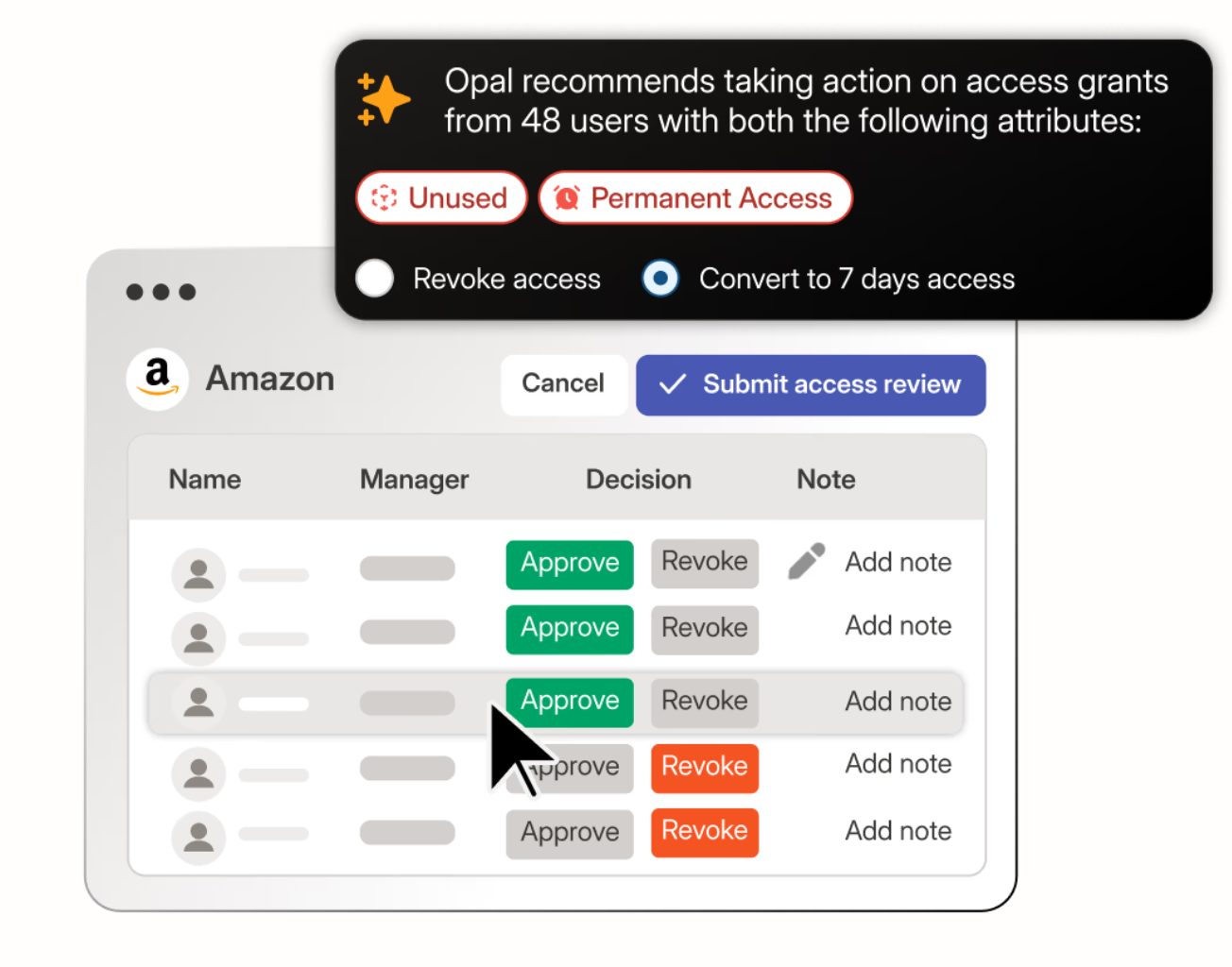
Features:
- Engineering-Focused Access Governance: Opal centralizes and visualizes access to repositories, production systems, Kubernetes clusters, databases, and internal developer tools—making it easier to understand and govern engineering entitlements.
- Just-in-Time (JIT) Access & Temporary Privileges: Reduces the risk of long-lived permissions by enforcing time-bound access for sensitive systems. Users request the access they need, when they need it; backed by approvals and policy rules.
- Automated Access Reviews: Opal streamlines identity audits by ingesting access data, surfacing anomalies, and generating review workflows tailored to engineering managers, compliance teams, and security leaders.
- Granular Access Policies & Role Controls: Enables policy-driven access tied to teams, projects, identity attributes, and security requirements. Helps organizations run cleaner development environments with less privilege sprawl.
- Infrastructure & Cloud Integrations: Native integrations with AWS, GCP, GitHub, GitLab, Okta, and internal tools make it easier to manage high-sensitivity access across distributed systems.
- Centralized Visibility for Security Teams: Security teams gain unified visibility into who has access to production and why which helps enforce least privilege, mitigate insider threats, and simplify SOC 2/SOX/HIPAA compliance.
Opal Security is a viable choice for organizations prioritizing infrastructure governance, developer access, and automated controls across cloud-native ecosystems.
How to Choose the Right ConductorOne Alternative
Selecting the right ConductorOne alternative requires evaluating not only the feature set of competing platforms but also the long-term operational, financial, and efficiency gains they deliver. As identity ecosystems grow more complex, organizations must compare vendors based on the speed at which value is realized, the total cost of ownership over the lifecycle of the system, and the automation depth that reduces manual overhead.
Time-to-Value
A major factor in selecting a ConductorOne alternative is how quickly the platform can be deployed and configured to the point where it delivers measurable outcomes. Modern identity teams need tools that integrate rapidly with HRIS, IdPs, SaaS applications, and cloud infrastructure – without months of professional services or custom engineering.
Platforms that prioritize out-of-the-box connectors, pre-built workflows, and intuitive admin experiences help shorten deployment cycles and reduce staff burden. In contrast, tools requiring extensive customization or manual rule-building can delay value realization, slow down governance improvements, and create early friction for stakeholders.
When assessing alternatives, IT and security leaders should prioritize vendors that offer:
- Fast, non-disruptive integrations
- Clear onboarding playbooks and templates
- Auto-discovery of users, roles, and entitlements
- Rapid setup for access reviews and JML workflows
A shorter time-to-value not only accelerates security improvements but also ensures stakeholder buy-in and early operational wins.
Total Cost of Ownership
Identity platforms vary significantly in both upfront pricing and long-term operational cost. While ConductorOne’s usage-based model may fit some organizations, others experience cost challenges as identity sources, connected apps, and entitlement volumes grow.
When comparing alternatives, leaders should evaluate the true long-term cost, including:
- Licensing and per-user fees
- Required add-ons (IGA, provisioning, reviews, etc.)
- Professional services or ongoing consulting
- Internal admin overhead and maintenance
- Infrastructure or hosting requirements for hybrid deployments
Solutions with modular pricing, all-in-one functionality, or lower administration overhead often deliver a more predictable, and often lower, total cost of ownership. The ideal alternative should reduce identity risk without straining budgets or requiring specialized expertise to maintain.
Automation Capabilities
Automation is one of the most important differentiators among ConductorOne alternatives. While ConductorOne offers strong orchestration for infrastructure access workflows, many organizations need broader automation across identity lifecycle management, request fulfillment, role creation, and access cleanup.
When evaluating rivals, prioritize platforms with automation capabilities that:
- Eliminate manual provisioning and deprovisioning
- Auto-generate roles or least-privilege recommendations
- Trigger access changes from HR or directory events
- Automatically enforce JIT access or time-bound entitlements
- Support AI-driven anomaly detection and SoD analysis
- Produce audit-ready logs and review evidence without human intervention
The right alternative should meaningfully reduce the labor involved in managing identities and entitlements. Strong automation also minimizes human error, accelerates response times, and strengthens least-privilege posture across the environment.
Why Lumos Is a Strong ConductorOne Alternative
While ConductorOne focuses on modernizing access reviews and request workflows, Lumos goes several steps further to deliver agentic, autonomous identity governance that combines Next-Gen IGA, lifecycle orchestration, and intelligent policy management into a unified platform. If ConductorOne is an access governance tool, Lumos is an identity command center – powered by Albus, our multi-agent AI identity system.
Agentic AI for Continuous Governance
Lumos doesn’t just streamline reviews; it makes identity governance smarter, faster, and self-improving:
- Albus, the AI Identity Agent: Analyzes access patterns, usage signals, and org structures to propose and refine roles and policies in real time.
- Smart, Contextual Suggestions: Flags stale access, SoD violations, and overprovisioned accounts based on real activity; not just assignment data.
- Conversational Access Insights: Ask, “Who in finance has production database access?” and Albus delivers evidence-backed answers in seconds – no SQL or spreadsheets needed.
This agentic layer transforms access governance from checklist tasks into intelligent workflows that reduce risk and scale securely.
Beyond Reviews: Complete Access Lifecycle
ConductorOne emphasizes access reviews and requests. Lumos unifies the full access lifecycle:
- Request to Revoke Automation: Access requests via Slack, Teams, CLI, or AppStore feed directly into automated approval chains and just-in-time provisioning.
- Joiner/Mover/Leaver Automation: Lifecycle events from HRIS or IdP systems trigger entitlement-level provisioning or deprovisioning.
- Audit-Ready Governance: Access reviews, certification campaigns, and policy enforcement run continuously and all evidence is captured natively in-platform.
The result: less overhead for IT, stronger audit readiness for GRC, and faster onboarding and access for employees.
Intelligent Role Mining and Policy Creation
Lumos excels where ConductorOne leaves off: automating the messy work of role design.
- AI Role Discovery: Albus detects user clusters based on usage and attributes to propose clean, contextual roles that save months of spreadsheet work.
- Policy Simulation: See what would happen before enforcing a new role or entitlement restriction.
- Adaptive Roles: When someone moves departments or their app usage changes, Lumos suggests updates to keep least privilege intact.
This turns a traditionally brittle RBAC/ABAC implementation into a living, breathing access model.
Fine-Grained Visibility and Control
ConductorOne provides insight into access requests and assignments. Lumos offers deep access intelligence:
- Access Graph: Visualize every identity, permission, and dependency across your stack: from Okta and Google Workspace to AWS and custom apps.
- Usage-Aware Governance: Make decisions based on whether access is actually used, not just assigned.
- Cross-System Control: From SaaS to infra, Lumos centralizes governance with policy enforcement across every identity type.
If you're looking for a next-gen IGA platform that goes beyond tickets and reviews, Lumos is your autonomous upgrade. For teams who want more than visibility, Lumos outpaces ConductorOne as the system of record (and action) for identity.
Want to learn more? Book a demo today and see Lumos and Albus in action!
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.




