What is Dynamic Access Control (DAC)?
Discover how Dynamic Access Control (DAC) enhances security, compliance, and flexibility in modern IT environments. Learn benefits, use cases, and best practices.


In an era where identity-based threats are among the top causes of data breaches, effective access control has never been more crucial. According to a CrowdStrike report, about 80% of cyberattacks involve identity-based methods such as compromised credentials or access misuse. Traditional access control models like Role-Based Access Control (RBAC) often struggle to keep pace with dynamic environments where users, devices, and resources continuously change.
Dynamic Access Control (DAC) is an approach designed to provide context-aware, policy-driven access permissions that adapt in real time. Rather than granting fixed permissions based only on roles, DAC considers attributes and environmental factors to enforce conditional security rules. For IT and security leaders, DAC offers stronger security, better compliance, and more agility.
In this guide, you’ll learn what DAC is, how it works, where it delivers value, implementation best practices, and how to navigate its technical and operational challenges.
What Is Dynamic Access Control (DAC)?
Dynamic Access Control (DAC) is an advanced access management model that applies policies dynamically, based on multiple attributes and real-time context, rather than static user-role assignments. At its core, DAC allows IT and security teams to define conditional rules that evaluate who the user is, what resource is being requested, and under what circumstances the access attempt occurs.
For example, a user may gain access to sensitive financial data only if they are part of the finance department, using a company-issued device, and connected through a secure network.
How DAC Differs from Traditional Models
Traditional access control systems, such as Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), provide foundational frameworks but come with limitations in today’s fast-changing environments:
- Role-Based Access Control (RBAC): Access is tied to predefined roles (e.g., HR, Finance, IT). While straightforward, RBAC can become rigid and overly broad, leading to “role explosion” and excessive privilege accumulation when users wear multiple hats.
- Attribute-Based Access Control (ABAC): Access is determined by evaluating attributes like user role, department, or time of access. While more granular than RBAC, ABAC rules can still be static and require frequent manual updates as organizational contexts change.
Dynamic Access Control advances these models by combining role- and attribute-based conditions with contextual intelligence. It considers factors such as device health, geolocation, sensitivity of the resource, and compliance requirements; all evaluated in real time. Instead of granting access based only on static roles or attributes, DAC continuously adapts permissions to align with security policies and business needs.
This adaptability makes DAC particularly valuable for organizations managing hybrid workforces, cloud adoption, and increasingly complex compliance obligations. By providing context-aware, least-privilege access, DAC ensures that permissions are not only accurate but also responsive to evolving risks and user behaviors.
How Dynamic Access Control Works
Dynamic Access Control operates by layering identity, resource, and contextual intelligence to create fine-grained, real-time authorization decisions. Instead of relying solely on static permissions, DAC continuously evaluates attributes and policies to determine whether access should be granted, denied, or elevated.
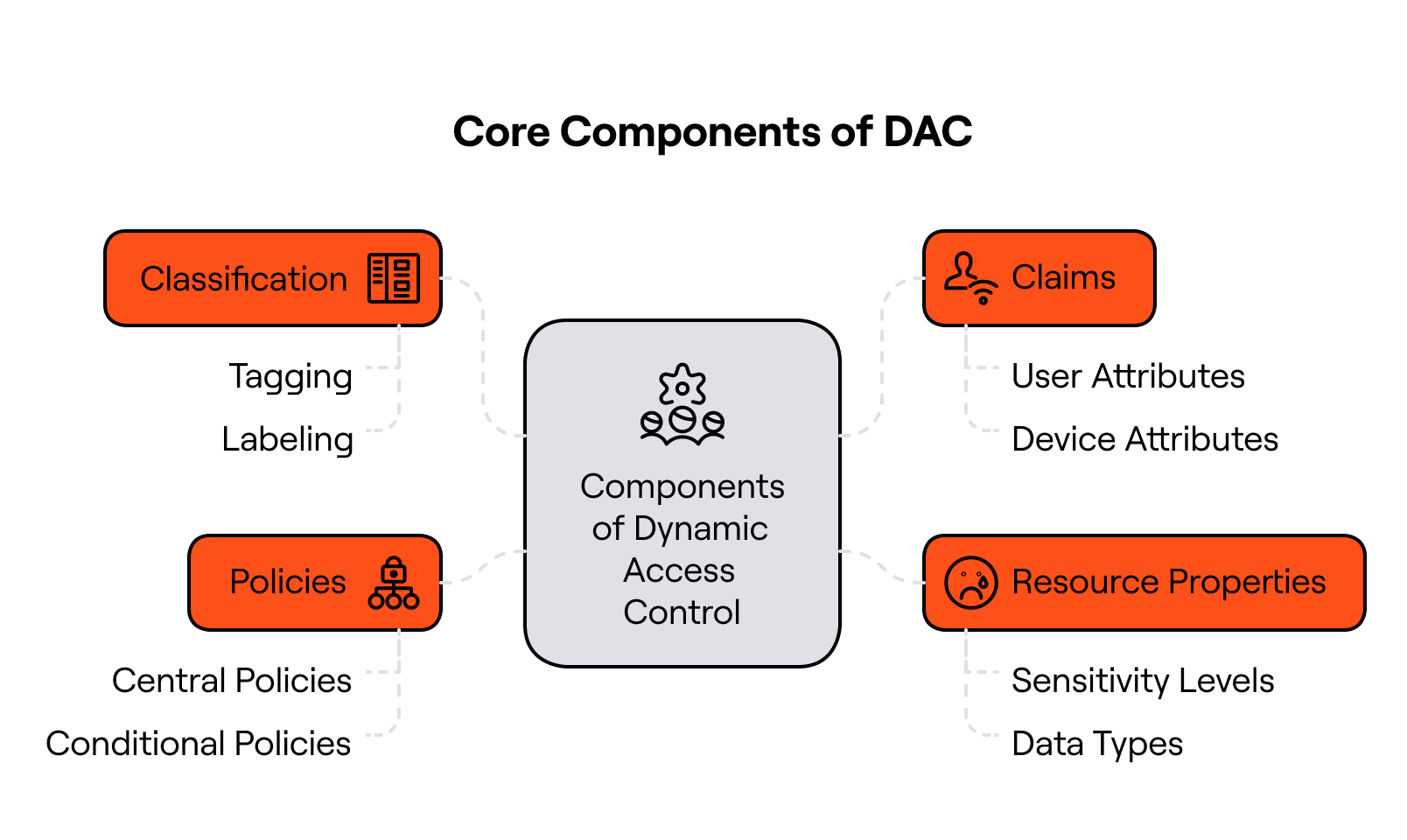
Core Components of DAC
The primary components of dynamic access control are:
- Classification (Tagging and Labeling Resources): Resources such as files and folders are tagged with metadata labels that describe their sensitivity (e.g., “Confidential,” “Finance,” “PII”). This classification makes it easier to enforce consistent policies across the environment.
- Claims (User, Device, and Resource Attributes): DAC leverages claims-based identity. Attributes like a user’s department, security clearance, or the compliance state of their device are included in the access decision process. These claims enable contextual enforcement far beyond traditional username-role matching.
- Resource Properties (Defining Resource Sensitivity): Resource properties extend classification by embedding attributes directly into objects. For example, a document might carry a property that flags it as subject to GDPR or HIPAA compliance.
- Policies (Central/Conditional Access Policies): Policies define the rules that connect users, claims, and resources. For example: “Only members of the Finance group on domain-joined devices can access financial reports.” These central policies reduce administrative overhead and ensure conditional enforcement across the enterprise.
Provisioning in Active Directory and Windows Environments
Dynamic Access Control is natively supported in Windows Server environments and integrates with Active Directory (AD) for identity management. In practice, administrators can:
- Define central access policies in AD that evaluate user claims, device attributes, and resource classifications before granting access.
- Use conditional access enforcement so access is dynamic: for instance, a sales executive might open a proposal only when logged in from a corporate laptop and within the company’s network.
- Apply auditing rules that generate logs when sensitive files are accessed, ensuring traceability for compliance.
In hybrid or cloud-connected environments, DAC principles extend into modern Identity Providers (IdPs) and conditional access solutions, ensuring unified enforcement across both on-premises and cloud resources.
By combining classification, claims, properties, and policies with deep integration into AD, DAC enables organizations to move beyond static, role-based controls to a dynamic, context-aware security model that aligns with Zero Trust principles.
Benefits of Dynamic Access Control
Dynamic Access Control brings IT and security teams beyond static, one-size-fits-all permission models by enabling context-aware, adaptive enforcement of policies. Its benefits span security, compliance, and operational agility that make it a key building block in modern identity and access management strategies.
Granular Access Management
Traditional access control models like RBAC or ABAC rely on static rules that don’t adapt well to changing circumstances. DAC, on the other hand, allows organizations to grant permissions based not only on a user’s role, but also on contextual attributes such as device security posture, location, or data sensitivity.
For example, a finance employee may have access to payroll files while on a corporate-managed laptop but may be denied the same access when logging in from a personal device. This level of granularity ensures the principle of least privilege is consistently applied, reducing unnecessary access pathways.
Improved Security and Compliance
Dynamic, policy-driven access decisions reduce risk by eliminating blanket permissions that attackers or insiders might exploit. Instead of granting long-lived access, DAC enforces real-time conditions, so permissions only exist when they’re truly needed and under secure conditions.
From a compliance perspective, DAC simplifies alignment with mandates like GDPR, HIPAA, and SOX, which emphasize data minimization and access accountability. Centralized policies and automatic enforcement reduce human error in provisioning, while fine-grained logging and auditing provide the evidence regulators demand. This helps IT and security leaders demonstrate compliance with confidence while reducing audit preparation burdens.
Flexibility for Modern IT Environments
Workforces are increasingly hybrid, applications are distributed across cloud and on-premises environments, and non-human identities like service accounts and bots play larger roles in daily operations. Static access models struggle to keep up with this dynamic reality.
DAC addresses these challenges by supporting conditional access across hybrid and multi-cloud infrastructures. Whether managing access to on-prem file servers, SaaS applications, or sensitive cloud workloads, DAC policies adapt to evolving conditions without requiring constant manual reconfiguration. This flexibility ensures security keeps pace with business growth and workforce mobility.
Challenges and Limitations of DAC
While DAC provides powerful, context-aware access policies, it also comes with a range of challenges that IT and security leaders must carefully evaluate before rolling it out at scale. These challenges can be grouped into protocol compatibility issues and operational hurdles, both of which can impact adoption and effectiveness.
Protocol Compatibility Issues
One of the biggest obstacles with DAC is the lack of uniformity in how vendors implement the standard protocols and frameworks that underpin dynamic policies. Different identity and access management solutions may interpret or extend protocols in ways that create interoperability gaps, forcing IT teams to develop custom integrations or workarounds.
Nested group memberships and certain identity objects also remain difficult to manage. For example, DAC can struggle when trying to enforce policies across deeply nested Active Directory groups or when handling non-standard identity objects, such as service accounts. This inconsistency can result in mismatched permissions or ineffective enforcement, reducing the benefits of context-aware access. Organizations often find themselves balancing between the ideal of fine-grained control and the practical limitations of vendor ecosystems.
Operational Challenges
Deploying DAC at scale presents its own operational difficulties. Large organizations with thousands of users and devices can run into synchronization delays between identity providers, directories, and access enforcement points. This may cause temporary mismatches where a user’s attributes or group memberships are updated in one system but not yet reflected in another, leading to inappropriate access denials or unrevoked permissions.
Another issue is partial provisioning or failed synchronization events, which can leave identities or resources in inconsistent states. If a provisioning job fails halfway, some users may receive only partial access or retain outdated privileges, creating both productivity and security risks. Troubleshooting these scenarios often requires specialized expertise, as logs may not always provide clear visibility into where the process failed.
Furthermore, DAC adds complexity to administrative overhead. Policies must be continuously updated to reflect organizational changes, evolving compliance requirements, and new applications or infrastructure. Without strong governance processes and monitoring tools, the risk of policy drift or misconfigurations increases, undermining the intended security posture.
Implementation Guide for Dynamic Access Control
Deploying Dynamic Access Control (DAC) successfully requires a structured approach that balances technical planning with operational readiness. IT and security leaders should consider both the deployment process and the long-term management of DAC policies to ensure sustainable adoption.
Steps to Deploy DAC
Implementing Dynamic Access Control requires more than just flipping a switch; it’s a methodical process that ensures access policies are both effective and sustainable. To achieve success, IT leaders should approach deployment in phases, starting with a clear understanding of resources, followed by the creation of context-aware policies, and finally validating outcomes before scaling across the organization.
The steps below outline a practical roadmap to establish DAC in a structured, low-risk manner.
- Resource Classification Strategy: The first step is defining a resource classification model. This involves tagging and labeling files, folders, and applications with metadata that reflects their sensitivity or business importance. Examples include labels like Confidential, Internal Use Only, or Financial Records. Proper classification ensures that policies can be applied consistently and in alignment with organizational priorities.
Designing and Applying Claims-Based Policies: With classification in place, administrators can design claims-based policies that leverage attributes of users, devices, and resources. For instance, a claims-based rule might grant access only to employees in the Finance department using corporate-managed devices when connecting from approved locations. These policies add context-aware flexibility beyond static role- or attribute-based controls. - Testing and Validation: Before rolling out DAC policies organization-wide, thorough testing is critical. IT teams should validate policies in a controlled environment, checking for unintended denials or over-permissive access. Pilot groups can provide feedback to refine conditions and claims logic. Continuous validation reduces the risk of operational disruption once DAC is enforced at scale.
Operational Considerations
Even with a successful deployment, the long-term effectiveness of DAC depends on how well it’s managed day to day. Beyond the technical setup, organizations need to think about the people and processes that keep policies aligned with evolving business needs.
This means equipping IT, security, and compliance teams with the right training to manage DAC effectively, as well as building governance processes that ensure policies remain accurate and relevant. The following considerations highlight what it takes to maintain DAC as a living, adaptable framework rather than a one-time project.
- Training Teams to Manage DAC: Even the most well-designed DAC policies can fail without proper operational support. Administrators, help desk staff, and compliance teams need training to understand how claims work, how policies are applied, and how to troubleshoot access issues. Role-specific training modules, combined with documentation, can accelerate adoption and reduce misconfigurations.
- Ongoing Policy Adjustments: Organizations are not static—departments change, new applications are introduced, and compliance requirements evolve. DAC policies must be regularly reviewed and adjusted to reflect these changes. Establishing a governance process, such as quarterly policy reviews or automated monitoring of access events, ensures that DAC continues to align with security goals while minimizing administrative burden.
Future of Dynamic Access Control
Dynamic Access Control is not a static technology; it is evolving to meet the demands of modern IT environments. As organizations transition to hybrid models, adopt Zero Trust security, and embrace AI-driven governance, DAC is becoming more adaptive, scalable, and intelligent.
Integration with Zero Trust Frameworks
Zero Trust security models assume that no user, device, or network segment is trusted by default. DAC naturally complements this philosophy by enforcing context-aware access policies. Instead of relying on static role definitions, DAC evaluates claims such as user identity, device health, and resource sensitivity in real time.
For example, a user connecting from an unmanaged device might be granted only partial access, while the same user on a trusted corporate laptop gains full privileges. As more organizations adopt Zero Trust architectures, DAC will serve as a policy engine that bridges identity, network, and endpoint security controls.
Expanding Use Across Hybrid/Multi-Cloud Ecosystems
Modern IT environments are rarely confined to a single data center or cloud provider. Enterprises now run applications across on-premises infrastructure, SaaS platforms, and multiple cloud providers. DAC’s ability to apply dynamic policies based on resource classification and contextual claims makes it well-suited for this complexity.
Future implementations will extend DAC capabilities beyond Windows and Active Directory ecosystems into cloud-native directories, containerized applications, and API-driven services. This expansion will allow organizations to maintain consistent access governance across diverse platforms without creating siloed policies.
AI and ML in Dynamic Policy Enforcement
The next wave of DAC innovation will be powered by artificial intelligence (AI) and machine learning (ML). By analyzing access logs, user behavior, and threat intelligence feeds, AI-driven DAC systems will proactively adjust policies in real time.
For instance, if anomalous behavior suggests a compromised account, DAC can automatically tighten access controls or trigger step-up authentication. Over time, ML models will refine policies by learning from access patterns, reducing manual tuning and minimizing false positives. This shift toward intelligent automation will enable DAC to anticipate risks, enforce least privilege at scale, and align security policies with ever-changing organizational dynamics.
Unlocking the Value of Dynamic Access Control
Dynamic Access Control elevates identity and access management from rigid role-based models into living, context‑aware systems. Instead of static permissions, DAC adapts to changes in user roles, device posture, sensitivity of resources, and real‑time risk signals. For IT and security leaders, this means stronger protection from insider threats, faster alignment with regulatory expectations, and smoother operations across hybrid and cloud environments. Enforcing least privilege becomes not just policy, but practice.
Lumos powers this shift. As the Autonomous Identity Platform, Lumos embeds automation, intelligence, and visibility directly into access governance. We unify identity lifecycle workflows, app access requests, and policy enforcement across 300+ integrations. This makes it easier to define DAC policies, apply them in real time, and maintain them as your organization changes. Whether you’re dealing with joiner/mover/leaver events, temporary access, or entitlement cleanup, Lumos turns DAC from a theoretical ideal into operational reality.
In a landscape of rising access risks and tighter compliance demands, legacy IAM tools and manual provisioning simply don’t scale. Lumos solves this by delivering end‑to‑end lifecycle automation, continuous monitoring (with Albus insights), and full audit trails – all built to elevate security without slowing productivity. The result is reduced risk, fewer tickets, and trust: in access, in governance, and in your identity posture.
Ready to embrace Dynamic Access Control with confidence? Book a demo with Lumos today to see how you can simplify compliance, secure every identity, and accelerate productivity.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.




