UAR Software: Top 15 User Access Review Tools in 2025
Discover the top 15 User Access Review (UAR) tools in 2025. Learn how UAR software improves compliance, reduces risk, and helps you choose the best solution for your organization.


User access reviews (UARs) – sometimes called access recertification, entitlement review, or account attestation – are the periodic audits organizations perform to verify that users only have the permissions they need. A thorough UAR process helps reduce security gaps, prevent insider threats, and ensure compliance with regulations like GDPR, HIPAA, and SOX. Despite that, many organizations struggle: according to a Verizon report, 82% of data breaches can be traced back, at least in part, to misuse of credentials, phishing, or overly permissive user access.
UAR tools are evolving rapidly. Rather than relying solely on manual spreadsheets or infrequent audits, modern solutions automate data collection, stakeholder notifications, role-based assessments, and reporting.
Whether your organization is just starting UARs or looking to upgrade, this guide will highlight what matters most and what to look for when choosing the right tool to protect your access environment.
What Is UAR Software?
User Access Review (UAR) is the process of periodically verifying that employees, contractors, and partners have the right level of access to systems, data, and applications. It ensures users only retain permissions necessary for their role, and that outdated or unnecessary privileges are removed. UARs are often mandated by compliance frameworks such as SOX, HIPAA, GDPR, and ISO 27001, making them a cornerstone of modern security programs.
UAR software automates this process by consolidating entitlement data from identity providers, HR systems, and applications, then presenting it in an organized format for managers and auditors to review. Instead of manually gathering data across systems and relying on spreadsheets, UAR tools streamline data collection, review campaigns, remediation, and reporting.
Why UAR Matters for IT, Security, and Compliance Teams
For IT and security teams, UARs play a critical role in minimizing insider threats and reducing the attack surface by eliminating unused or excessive permissions. Compliance officers rely on UARs to demonstrate regulatory alignment and provide audit-ready reports. Without automated UAR processes, organizations risk costly breaches, audit failures, and operational inefficiencies.
Beyond compliance, effective UARs improve overall identity hygiene. By continuously validating “who has access to what,” organizations can enforce least-privilege access, tighten security controls, and align with zero trust principles.
Who Uses UAR Tools (and When)?
UAR software is primarily used by IT administrators, security teams, and compliance managers. Line-of-business managers also play a role, as they are often required to certify access for their direct reports during review cycles.
Organizations typically rely on UAR tools during:
- Quarterly or annual audits to satisfy regulatory requirements.
- Employee lifecycle events (joiner, mover, leaver) to ensure timely provisioning and deprovisioning.
- Ad-hoc security reviews following incidents or policy changes.
As organizations scale and the number of applications grows, UAR tools become essential for ensuring consistency, accuracy, and efficiency across the entire access review process.
Benefits of UAR Software
UAR software has become an essential tool for IT, security, and compliance teams tasked with ensuring that employees have only the access they need. By automating reviews and centralizing access data, UAR tools help organizations strengthen security, simplify compliance, and reduce the administrative burden of manual reviews.
Below are some of the core benefits.
- Improve Security by Enforcing Least Privilege
- Streamline Compliance
- Reduce Manual Work and Audit Fatigue
- Increase Visibility into Access and Entitlements
Improve Security by Enforcing Least Privilege
One of the most powerful outcomes of UAR software is the enforcement of least privilege. By continuously monitoring and reviewing entitlements, organizations can ensure users retain only the permissions they need to perform their jobs. Automated review cycles reduce the risk of privilege creep, where employees accumulate unnecessary access over time.
This proactive tightening of access rights lowers the likelihood of insider threats, accidental data exposure, or exploitation by external attackers.
Streamline Compliance
Regulatory frameworks such as SOC 2, SOX, ISO 27001, HIPAA, and GDPR all require organizations to regularly validate and document user access. UAR software automates the process of collecting entitlement data, distributing review campaigns, and generating audit-ready reports. Instead of scrambling before an audit, compliance teams can rely on consistent, automated evidence that meets regulators’ expectations.
This not only reduces compliance risk but also builds trust with customers, partners, and stakeholders.
Reduce Manual Work and Audit Fatigue
Traditional user access reviews often involve tedious, error-prone spreadsheets and email chains. UAR software eliminates these manual workflows by orchestrating campaigns, notifying reviewers, and applying remediation actions automatically. This reduces the time and effort required for each review cycle, lightens the load on IT teams, and minimizes “audit fatigue” for managers who are tasked with certifying access.
With streamlined reviews, teams can focus on higher-value security and governance initiatives instead of repetitive administrative work.
Increase Visibility into Access and Entitlements
Modern enterprises often rely on dozens, or even hundreds, of applications across cloud and on-prem environments. Without a centralized view, it’s difficult to know who has access to what. UAR software consolidates identity and entitlement data into a single pane of glass, making it easier to spot excessive permissions, dormant accounts, or anomalous access patterns.
This visibility not only improves security posture but also enables better governance and decision-making across the organization.
Top 15 UAR Software Tools in 2025
Choosing the right User Access Review software can be the difference between a streamlined, compliant identity governance process and one bogged down by manual reviews and audit fatigue. With increasing regulatory demands and growing security risks, IT and security leaders need tools that not only automate access reviews but also deliver actionable insights, enforce least privilege, and provide audit-ready reporting.
In this section, we’ve curated a list of the top 15 UAR tools in 2025 so you can evaluate which solution best fits your organization’s scale, complexity, and compliance requirements. Here are the top 15 UAR tools in 2025:
- Lumos
- SailPoint
- Okta
- Microsoft Entra
- Oracle Identity Governance
- IBM Security Verify
- One Identity
- Omada
- Saviynt
- CyberArk
- BeyondTrust
- Ping
- Elimity
- Sennovate
- LogicManager
1. Lumos
Lumos is redefining how organizations approach User Access Reviews (UARs) with its autonomous identity platform. By embedding AI into every layer of identity governance, Lumos automates certification campaigns, streamlines reviewer workflows, and eliminates manual overhead; all while enhancing visibility and audit readiness. Lumos makes it easy to enforce least privilege, accelerate compliance, and close risky access gaps across SaaS, cloud, and on-prem environments.
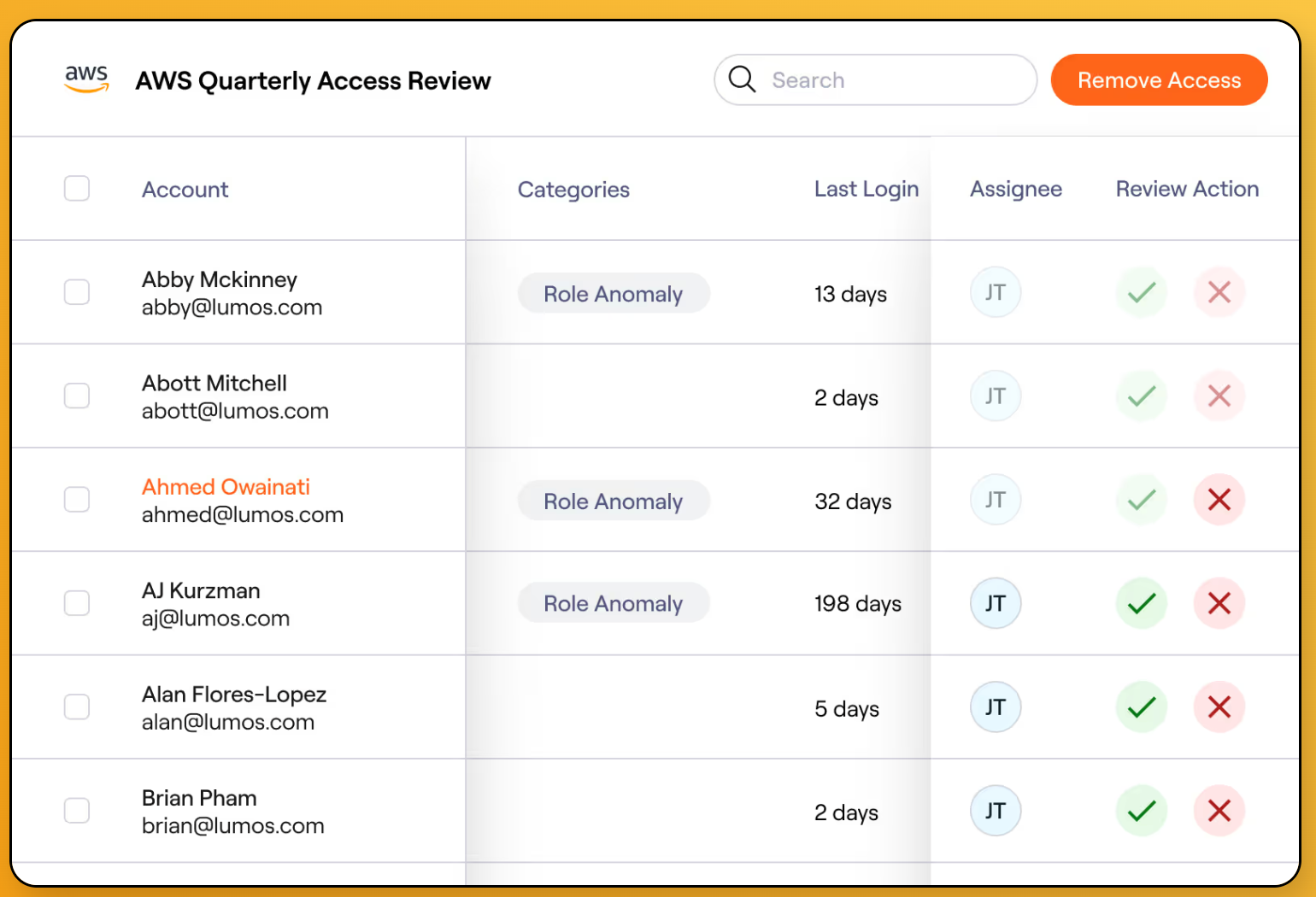
- G2 Rating: 4.8/5
- Price: Starts at $1/month per user (varies by feature set)
- Best for: Security-forward IT and GRC teams at mid-size and enterprise organizations that need scalable UAR automation, full entitlement visibility, and audit-grade evidence; all delivered in a modern, AI-native platform that’s faster and easier to deploy than legacy IGA tools.
Lumos helps organizations transform compliance from a burden into a streamlined, automated process. With campaign templates, real-time access insights, and Albus – Lumos’ AI identity agent – reviewers get smart recommendations, context-aware visibility, and centralized evidence collection that drastically reduces time-to-certification and human error.
Key Features:
- Automated UAR Campaigns: Launch and manage recurring or one-off campaigns across departments, apps, and user groups with ease.
- AI-Powered Reviewer Insights: Albus recommends approvals, flags anomalies, and provides contextual access justifications; reducing reviewer fatigue.
- End-to-End Evidence Collection: Every action, comment, and outcome is logged for full audit readiness.
- Real-Time Access Visibility: Drill into who has access to what, why, and for how long – down to the entitlement level.
- Seamless Integration: Works with Okta, Entra ID, HRIS, and 300+ SaaS and on-prem systems to unify UAR across your tech stack.
To learn how Lumos can automate and simplify your access review process, book a demo today.
2. SailPoint
SailPoint is an identity security platform that includes capabilities for user access reviews. The solution helps organizations manage and certify user entitlements across applications, systems, and cloud services. SailPoint’s automation features reduce manual workloads during audit cycles, while its role-based access controls support least-privilege policies.
- G2 Rating: 4.3/5
- Price: Custom pricing based on organizational needs and deployment scale.
- Best for: Large enterprises with complex compliance requirements that need automated identity governance and access review workflows.
Key Features:
- Automated User Access Reviews: Streamlines periodic access certifications with policy-driven campaigns and customizable review processes.
- Role-Based Access Control (RBAC): Helps define and enforce least-privilege access by aligning entitlements with business roles.
- Integration Ecosystem: Connects with hundreds of enterprise applications, directories, and cloud services to centralize governance.
- Audit and Compliance Reporting: Generates detailed, audit-ready reports to support SOC 2, SOX, ISO 27001, and other frameworks.
- Policy Enforcement: Applies automated controls to detect and remediate excess or outdated entitlements.
- Lifecycle Management: Coordinates provisioning and deprovisioning to ensure access aligns with employee joiner-mover-leaver (JML) status.
3. Okta
Okta is an identity and access management (IAM) platform that provides features for user authentication, authorization, and governance. Its user access review capabilities allow organizations to conduct access certifications, enforce least-privilege policies, and maintain compliance. Okta integrates with a wide range of enterprise applications and offers strong lifecycle management functionality for employees, contractors, and partners.
- G2 Rating: 4.4/5
- Price: Subscription-based pricing, varies by feature set and deployment scale.
- Best for: Organizations of all sizes seeking a cloud-first IAM solution with integrated UAR functionality and broad application support.
Key Features:
- User Access Reviews: Automates periodic certification campaigns with customizable review workflows.
- Lifecycle Management: Manages provisioning, deprovisioning, and access adjustments for joiner-mover-leaver (JML) processes.
- Application Integrations: Offers thousands of pre-built connectors to enterprise and cloud apps for centralized access governance.
- Multi-Factor Authentication (MFA): Adds layered security for access decisions to reduce account compromise risks.
- Compliance Reporting: Provides audit-ready reports to support SOC 2, SOX, HIPAA, and other regulatory frameworks.
- Adaptive Access Policies: Evaluates contextual risk signals (device, location, behavior) to enforce dynamic policies.
4. Microsoft Entra
Microsoft Entra is Microsoft’s identity and access management suite, combining Azure Active Directory (Azure AD) with tools for identity governance, access management, and verification. Its UAR features allow organizations to enforce least-privilege access, support regulatory compliance, and streamline identity lifecycle management across hybrid and multi-cloud environments.
- G2 Rating: 4.4/5
- Price: Tiered subscription pricing, included with Microsoft 365 or Azure licensing depending on features.
- Best for: Enterprises leveraging Microsoft ecosystems looking for deep integration with Azure, Office 365, and cloud-native UAR capabilities.

Key Features:
- User Access Reviews: Automates recurring access reviews for apps, groups, and roles, with customizable campaign settings.
- Lifecycle Workflows: Automates onboarding, offboarding, and role transitions with built-in identity lifecycle governance.
- Conditional Access Policies: Evaluates device posture, risk signals, and context to enforce adaptive access control.
- Privileged Identity Management (PIM): Provides just-in-time access to sensitive roles and resources with approval workflows.
- Compliance Reporting: Delivers audit-ready reporting to support regulatory frameworks such as SOX, HIPAA, and ISO 27001.
- Seamless Microsoft Integration: Natively integrates with Azure, Microsoft 365, and third-party SaaS applications.
5. Oracle Identity Governance
Oracle Identity Governance (OIG) is an enterprise-grade identity governance and administration (IGA) solution that also provides user access review capabilities alongside provisioning, role management, and compliance reporting. Designed for large and complex organizations, OIG helps enforce least-privilege access, automate certification campaigns, and maintain compliance across hybrid IT environments.
- G2 Rating: 4.0/5
- Price: Custom enterprise pricing based on deployment and scale.
- Best for: Large enterprises with complex identity governance needs requiring deep customization, strong compliance features, and Oracle ecosystem integration.

Key Features:
- User Access Certifications: Automates review campaigns for roles, entitlements, and application access to reduce audit fatigue.
- Role and Policy Management: Supports granular role modeling, role mining, and enforcement of least-privilege policies.
- Provisioning and De-provisioning: Streamlines onboarding and offboarding with automated workflows tied to HR and IT systems.
- Segregation of Duties (SoD): Monitors and enforces SoD policies to prevent toxic access combinations.
- Compliance Reporting: Delivers detailed, audit-ready reports aligned with regulations like SOX, GDPR, and HIPAA.
- Integration with Oracle and Third-Party Systems: Connects natively with Oracle applications and integrates with a wide range of enterprise platforms.
6. IBM Security Verify
IBM Security Verify is an identity governance and access management platform that offers built-in user access review (UAR) functionality alongside authentication, single sign-on (SSO), and risk-based access controls. It is designed to help organizations manage user identities, enforce compliance, and automate governance workflows across hybrid IT environments.
- G2 Rating: 4.2/5
- Price: Custom pricing depending on deployment type and organizational scale.
- Best for: Enterprises seeking a flexible identity solution with strong governance features and integration capabilities, particularly in regulated industries.
Key Features:
- User Access Reviews: Automates periodic certification campaigns with customizable workflows and reporting.
- Risk-Based Access: Uses AI-driven analytics to adjust authentication and authorization dynamically based on user context.
- Provisioning and De-provisioning: Automates account creation, modification, and removal to align access with role and lifecycle changes.
- Single Sign-On (SSO): Simplifies access to applications with centralized authentication across cloud and on-premise systems.
- Adaptive Multi-Factor Authentication (MFA): Strengthens identity verification with contextual, risk-aware authentication options.
- Compliance Reporting: Generates detailed audit logs and dashboards to support regulatory mandates such as SOX, HIPAA, and GDPR.
- Integrations: Supports integration with diverse enterprise applications, ITSM systems, and security platforms.
7. One Identity
One Identity is an identity and access management (IAM) platform that provides user access review capabilities along with identity governance, privileged access management (PAM), and Active Directory management. It focuses on helping organizations enforce least-privilege policies, streamline compliance, and automate identity-related processes across hybrid and cloud environments.
- G2 Rating: 4.2/5
- Price: Custom pricing based on deployment size, modules, and licensing model.
- Best for: Organizations looking for an IAM solution that integrates UAR, PAM, and governance features with strong support for Active Directory and hybrid IT environments.

Key Features:
- User Access Reviews: Automates periodic reviews with configurable campaigns, reducing audit fatigue.
- Privileged Access Management (PAM): Provides session monitoring, credential vaulting, and just-in-time privilege elevation.
- Identity Governance: Centralized role management, policy enforcement, and compliance reporting.
- Active Directory and Azure AD Management: Simplifies administration, provisioning, and group management across directory services.
- Automated Provisioning: Aligns user access with HR and business system changes to reduce orphaned accounts.
- Compliance Dashboards: Generates real-time reports to support standards such as SOX, HIPAA, and GDPR.
- Integrations: Connects with ITSM tools, cloud services, and enterprise applications to unify identity workflows.
8. Omada
Omada is an identity governance and administration (IGA) platform that includes strong support for UAR processes. It focuses on enforcing least-privilege principles, ensuring compliance, and streamlining identity lifecycle management through automation and policy-driven controls. Omada is often used by enterprises seeking scalability and structured governance frameworks.
- G2 Rating: 4.3/5
- Price: Custom pricing based on organizational requirements, deployment model, and selected features.
- Best for: Large organizations with complex governance and compliance needs that require a structured, policy-based approach to identity management and UARs.
Key Features:
- User Access Reviews: Automates periodic certifications, providing auditors and managers with clear review workflows.
- Identity Lifecycle Management: Automates provisioning, de-provisioning, and access changes aligned with HR and business processes.
- Policy-Based Access Control: Enforces least-privilege through role- and attribute-based models.
- Compliance and Audit Reporting: Delivers dashboards and audit-ready reports to support frameworks such as SOX, GDPR, and ISO 27001.
- Role Management and Role Mining: Provides tools for designing and refining enterprise roles to reduce excess entitlements.
- Integration Framework: Connects with enterprise applications, directories, and ITSM platforms for consistent governance.
- Cloud and Hybrid Support: Enables governance across on-premises, SaaS, and multi-cloud environments.
9. Saviynt
Saviynt is a cloud-first identity governance and administration (IGA) platform that also provides support for user access reviews. It emphasizes risk-based access management, automation, and granular visibility across hybrid and multi-cloud environments. Saviynt is often chosen by enterprises looking for flexibility in enforcing least-privilege access while meeting compliance obligations.
- G2 Rating: 4.3/5
- Price: Custom pricing based on enterprise size, deployment scope, and features selected.
- Best for: Enterprises with cloud-heavy environments seeking advanced governance, risk-based UARs, and compliance automation.

Key Features:
- Automated User Access Reviews: Simplifies periodic certifications with automated campaigns and built-in workflows.
- Risk-Based Access Certification: Prioritizes reviews based on entitlements, role sensitivity, and contextual risk scoring.
- Cloud Security and Governance: Manages entitlements across AWS, Azure, Google Cloud, and SaaS platforms.
- Role and Entitlement Management: Provides advanced role mining and modeling for least-privilege access enforcement.
- Policy and Compliance Management: Supports regulatory standards such as SOX, HIPAA, GDPR, and ISO 27001.
- Integration Capabilities: Offers prebuilt connectors for enterprise applications, directories, and cloud platforms.
- Analytics and Reporting: Provides dashboards and audit-ready reporting for compliance and governance oversight.
10. CyberArk
CyberArk is a security platform best known for its privileged access management (PAM) capabilities, but it also provides features to support UARs. The platform focuses on controlling, monitoring, and auditing access to privileged accounts, making it particularly relevant for organizations where high-risk entitlements must be reviewed and governed carefully.
- G2 Rating: 4.4/5
- Price: Custom pricing based on deployment scope and modules.
- Best for: Enterprises with significant privileged access requirements seeking strong governance over sensitive accounts and high-risk entitlements.

Key Features:
- Privileged Access Governance: Centralizes and automates reviews of privileged accounts to ensure compliance with least-privilege principles.
- User Access Review Campaigns: Supports periodic access certifications, especially for sensitive systems and administrative accounts.
- Policy Enforcement and Risk Scoring: Applies contextual risk-based policies to privileged sessions and high-value entitlements.
- Session Monitoring and Recording: Provides visibility into privileged user activity, helping support audits and investigations.
- Automated Remediation: Removes or adjusts privileged access based on review outcomes or detected anomalies.
- Integration Ecosystem: Connects with IAM, SIEM, and ITSM platforms to extend review and governance capabilities.
- Audit and Compliance Reporting: Generates audit-ready reports for regulatory standards such as SOX, HIPAA, and PCI DSS.
11. BeyondTrust
BeyondTrust is a security and identity platform with a strong focus on privileged access management (PAM) and secure remote access. In addition to controlling high-risk accounts, BeyondTrust supports user access review processes by enabling governance over privileged and non-privileged entitlements. Its solutions are widely used in industries with strict compliance requirements and distributed IT environments.
- G2 Rating: 4.6/5
- Price: Custom pricing based on organizational needs and deployment scale.
- Best for: Enterprises with complex infrastructures that need secure oversight of privileged accounts, remote sessions, and periodic access reviews.
Key Features:
- Privileged Access Management: Centralizes and monitors privileged account use with least-privilege enforcement.
- Access Certification Campaigns: Automates periodic reviews for privileged and high-risk entitlements.
- Remote Access Management: Secures third-party and vendor access without requiring VPNs.
- Policy-Based Controls: Enforces granular permissions across accounts and applications.
- Session Recording and Monitoring: Tracks privileged activity for visibility and compliance reporting.
- Automated Remediation: Removes unused or excessive privileges based on review findings.
- Compliance Reporting: Generates audit-ready reports for frameworks like PCI DSS, HIPAA, and SOX.
12. Ping
Ping is an enterprise identity and access management (IAM) platform that provides capabilities across workforce, customer, and device identities. As part of its IAM suite, ForgeRock supports user access review (UAR) processes by integrating governance workflows, policy enforcement, and detailed reporting. Its cloud-first architecture makes it a common choice for organizations looking to modernize identity operations while meeting compliance requirements.
- G2 Rating: 4.3/5
- Price: Custom pricing depending on deployment model and modules selected.
- Best for: Enterprises seeking a comprehensive IAM solution with integrated UAR features, especially in hybrid or cloud-native environments.

Key Features:
- Access Certification Campaigns: Automates periodic user access reviews with customizable workflows.
- Identity Governance: Provides policy-based oversight for entitlements across applications and infrastructure.
- Lifecycle Management: Automates joiner-mover-leaver (JML) processes to ensure timely provisioning and deprovisioning.
- AI-Driven Recommendations: Suggests least-privilege adjustments based on usage data and access patterns.
- Integration Ecosystem: Connects with HR systems, directories, cloud apps, and on-premises resources.
- Audit and Compliance Reporting: Generates audit-ready evidence for frameworks such as SOX, GDPR, and HIPAA.
- Access Request and Approval: Offers self-service access requests with manager or policy-driven approvals.
13. Elimity
Elimity is a governance-focused identity analytics and UAR platform that emphasizes visibility, risk detection, and streamlined compliance. It helps organizations analyze access rights across systems, identify outliers, and automate certification campaigns. Designed with lightweight deployment in mind, Elimity is often used by security and compliance teams that want faster oversight without the complexity of traditional identity governance suites.
- G2 Rating: 4.4/5
- Price: Custom pricing depending on organizational size and integrations required.
- Best for: Organizations seeking a dedicated UAR and identity analytics platform with strong reporting capabilities and an emphasis on audit readiness.
Key Features:
- Automated Access Reviews: Simplifies certification campaigns with configurable workflows.
- Identity Analytics: Highlights unusual or risky entitlements with dashboards and reports.
- Outlier Detection: Identifies excessive privileges or deviations from policy baselines.
- Integrations: Connects with common directories, HR systems, and business apps for centralized oversight.
- Compliance Support: Provides audit-ready evidence for frameworks like GDPR, SOX, and ISO 27001.
- Role Mining: Suggests least-privilege configurations by analyzing existing access patterns.
- Customizable Reporting: Delivers exportable audit reports and compliance dashboards for stakeholders.
14. Sennovate
Sennovate is a managed security services and identity solutions provider that includes support for UAR processes as part of its broader governance and compliance offerings. The platform emphasizes tailored deployments, making it a fit for organizations that need managed support in addition to software. Sennovate integrates access review automation with identity lifecycle management, compliance reporting, and risk analysis.
- G2 Rating: 4.3/5
- Price: Custom pricing based on service scope and organizational requirements.
- Best for: Organizations seeking managed identity and security services alongside UAR automation to reduce internal workload.

Key Features:
- Automated UAR Campaigns: Streamlines access certification with workflows for reviewers and managers.
- Identity Lifecycle Management: Supports provisioning, de-provisioning, and access changes across systems.
- Compliance Reporting: Provides audit-ready evidence for regulations such as SOX, SOC 2, HIPAA, and ISO 27001.
- Risk-Based Reviews: Prioritizes certifications based on entitlement sensitivity and user activity.
- Integration Options: Connects with major directories, HR systems, and SaaS applications.
- Managed Security Services: Offers 24/7 monitoring and expert support for identity governance and access control.
- Customizable Workflows: Enables organizations to adapt reviews and reporting to unique business or regulatory needs.
15. LogicManager
LogicManager is a governance, risk, and compliance (GRC) platform that incorporates user access review functionality as part of its identity governance and compliance workflows. The platform emphasizes risk-based access certification, audit readiness, and streamlined reporting for organizations that need to align UAR with broader compliance frameworks. Its strength lies in helping IT and security teams embed access reviews into an organization’s enterprise risk management (ERM) program.
- G2 Rating: 4.4/5
- Price: Custom pricing based on features, modules, and organizational size.
- Best for: Organizations that want to integrate UAR processes with risk management, compliance, and governance initiatives.
Key Features:
- Access Review Campaigns: Automates user certification cycles across systems and applications.
- Risk-Based Access Control: Prioritizes review tasks based on entitlement sensitivity and business risk.
- Compliance Support: Offers built-in workflows for frameworks such as SOC 2, SOX, ISO 27001, and HIPAA.
- Centralized Reporting: Provides audit-ready evidence with dashboards and customizable reports.
- Workflow Automation: Reduces manual workload by automating task assignment and follow-ups.
- Integration Capabilities: Connects with HR systems, directories, and ITSM tools for streamlined data ingestion.
- ERM Alignment: Embeds access review processes within a broader risk and compliance management program.
Key Features to Look for in User Access Review Tools
User Access Review tools are a cornerstone of modern identity governance, helping organizations enforce least privilege, stay audit-ready, and improve overall security posture. But not all UAR platforms are created equal. When evaluating tools, IT and security leaders should look for features that go beyond simple access certification and provide automation, intelligence, and flexibility to fit complex enterprise needs. Below are the essential features to consider. The key features to look for in a UAR tool are:
- Automated Review Campaigns
- Reviewer Assignment and Delegation
- Integration with Identity Providers (IdPs) and Apps
- Entitlement-Level Visibility
- Real-Time Access Insights and Recommendations
- Audit Trails and Evidence Collection
- Support for Human and Non-Human Identities
- User-Friendly Dashboards and Reporting
Automated Review Campaigns
Strong UAR software should allow administrators to launch scheduled or ad-hoc review campaigns with minimal manual setup. Automation ensures reviews happen consistently across applications and departments, reducing human error and compliance gaps. Features like reminders, escalation workflows, and recurring campaign templates streamline the entire cycle from launch to closure.
Reviewer Assignment and Delegation
The right platform must support granular assignment of reviews to the appropriate data owners, managers, or application admins. Delegation capabilities are equally important, enabling temporary reassignment if a reviewer is unavailable. This avoids bottlenecks and keeps review cycles on track, ensuring accountability without introducing unnecessary delays.
Integration with Identity Providers (IdPs) and Apps
Seamless integration with identity providers such as Okta, Azure AD, or Ping, as well as business-critical apps like Salesforce, AWS, and Workday, is non-negotiable. Direct integrations simplify entitlement ingestion, synchronize data, and allow for real-time validation of user access. Without these connectors, reviews risk being outdated or incomplete.
Entitlement-Level Visibility
Effective reviews require more than account-level checks. UAR software should offer fine-grained visibility into entitlements, such as admin rights, role assignments, or privileged access. Entitlement-level context empowers reviewers to make informed decisions instead of rubber-stamping access requests.
Real-Time Access Insights and Recommendations
Modern UAR tools should include analytics that highlight anomalies and risky access patterns. AI-driven recommendations, such as flagging unused permissions or suggesting least-privilege adjustments, help reviewers make faster, more accurate decisions. Real-time insights also reduce the likelihood of over-provisioning and long-standing privileges.
Audit Trails and Evidence Collection
Audit readiness is one of the main reasons organizations implement UAR. Platforms should automatically log review actions, generate tamper-proof evidence, and export compliance reports tailored to frameworks like SOC 2, SOX, and ISO 27001. Centralized audit trails reduce administrative burden and ensure every access decision can be defended during an audit.
Support for Human and Non-Human Identities
With the rise of automation and service accounts, UAR tools must extend beyond human users. Non-human identities – such as bots, APIs, and machine accounts – can introduce significant risk if not regularly reviewed. Solutions should support policy-driven reviews for these entities, ensuring they follow the same least-privilege principles as employee accounts.
User-Friendly Dashboards and Reporting
Finally, usability matters. Dashboards that visualize campaign progress, highlight high-risk accounts, and simplify review tasks can drastically improve reviewer engagement and reduce fatigue. Configurable reporting helps executives, auditors, and IT teams quickly extract insights without navigating complex interfaces.
How to Choose the Right UAR Tool for Your Organization
Selecting the right UAR software can be the difference between a streamlined, audit-ready identity program and a manual, error-prone process that slows down IT and compliance teams. With so many options on the market in 2025, IT and security leaders should evaluate tools against their organizational requirements, compliance landscape, and reviewer experience. Below are the key considerations. Here is how to choose the right UAR tool for your organization:
- Consider Your Integration Requirements
- Balance Automation vs. Control Needs
- Look for Tools with AI/ML-Driven Insights
- Prioritize Usability for Reviewers
- Evaluate Compliance and Audit Readiness Features
Consider Your Integration Requirements
A UAR tool’s value depends heavily on how well it connects with your existing ecosystem. For most organizations, that means seamless integration with identity providers (IdPs) like Okta, Microsoft Entra, or Ping Identity, as well as critical applications such as Salesforce, AWS, or Workday. The best tools provide pre-built connectors and APIs, reducing the time and effort needed to onboard applications.
When evaluating tools, ask: Does it support entitlement-level data ingestion across both cloud and on-premises systems?
Balance Automation vs. Control Needs
Automation is essential for reducing manual workload, but too much automation without human oversight can create risk. The right tool should offer configurable levels of automation: from fully automated review campaigns to hybrid approaches where reviewers make final decisions. Features like automated de-provisioning with rollback options, risk-based triggers, and configurable approval chains strike the right balance between efficiency and control.
Look for Tools with AI/ML-Driven Insights
As user entitlements become more complex, AI and machine learning help simplify reviews. Modern UAR tools can highlight anomalies, flag unused permissions, and suggest least-privilege adjustments. These capabilities not only reduce reviewer fatigue but also improve decision quality. Look for platforms that provide real-time recommendations, predictive risk scoring, and usage-based insights to support informed access decisions.
Prioritize Usability for Reviewers
Even the most advanced tool will fail if reviewers find it too difficult to use. A strong UAR platform should offer clean, intuitive dashboards that simplify the review process for managers and data owners. Features like bulk approval (with safeguards), context-rich entitlement descriptions, and integration into everyday platforms such as Slack or Microsoft Teams can increase adoption and reduce delays.
Evaluate Compliance and Audit Readiness Features
Compliance is often the main driver for UAR implementation, whether for SOC 2, SOX, ISO 27001, HIPAA, or GDPR. Tools should provide tamper-proof audit logs, exportable evidence reports, and campaign tracking that aligns with regulatory requirements. The ability to generate audit-ready summaries on demand significantly reduces audit fatigue and ensures consistency across review cycles.
Choosing Lumos for User Access Reviews
UAR software has become a non-negotiable part of any modern identity and security strategy. With growing regulatory pressure, expanding cloud environments, and increasingly complex permission structures, manual access reviews just don’t scale. The right UAR solution can help organizations enforce least privilege, simplify audits, reduce risk, and free up valuable IT and security resources.
Lumos leads the way in this new era of automated, intelligent access governance. As the first autonomous identity platform, Lumos embeds AI into every layer of the user access review process; helping organizations eliminate manual overhead, reduce audit fatigue, and ensure secure access at scale. From campaign automation and entitlement-level insights to policy enforcement and anomaly detection, Lumos transforms UAR from a checkbox exercise into a strategic security advantage.
While every tool in this list has its strengths, Lumos stands out for its speed, simplicity, and depth – offering 10x faster deployments, 80% less manual work, and a unified platform that combines access reviews, provisioning, and app governance all in one.
Ready to modernize your UAR process and streamline identity governance? Book a demo with Lumos today and see why leading IT and security teams trust Lumos to secure every identity.
Try Lumos Today
Book a 1:1 demo with us and enable your IT and Security teams to achieve more.
_%20Benefits%20and%20How%20To%20Implement%20It.avif)



