How We Use AI to Build Integrations at Lumos
Discover how Lumos is redefining identity security with the first Autonomous Identity Platform – built for limitless integrations, seamless deployment, and automatic maintenance across all your apps, from legacy to SaaS.

In this article
At Lumos, we're on a mission to redefine how organizations secure access in a world drowning with apps. As companies adopt more tools than ever, the challenge isn't just keeping up – it's staying ahead. That’s why we're building a unified autonomous identity platform designed for seamless deployment, automatic maintenance, and limitless integration support.
Enterprises today are managing hundreds of apps across on-prem, cloud, and hybrid environments; and that number isn’t slowing down. Each new tool introduces more risk, more access points, and more operational overhead. At Lumos, we believe the only way forward is through Autonomous Identity – a platform smart enough to integrate with any application, no matter where or how it runs.
Securing access shouldn't mean slowing your business down. Lumos is building the first truly Autonomous Identity Platform, where integrations are limitless and maintenance is automatic. Supporting all apps your teams rely on, whether legacy systems or cutting-edge SaaS, is what Lumos is here for.
Autonomous Identity Platform Development
Building an Autonomous Identity Platform that supports any application isn't just about raw engineering horsepower; it’s about having the right systems and data in place. That’s why we created two internal powerhouses that make it possible to keep up with the growing sprawl of apps our customers rely on.
Simply put, we don’t just build integrations. We build tools that build integrations. At Lumos, we've developed two powerful internal frameworks that let us rapidly support new applications, test them with precision, and deploy them without hassle. It's how we keep up with the never-ending stream of new tech our customers adopt, so they never have to worry about access and security falling behind. We call these two frameworks the integration factory and integration engine.
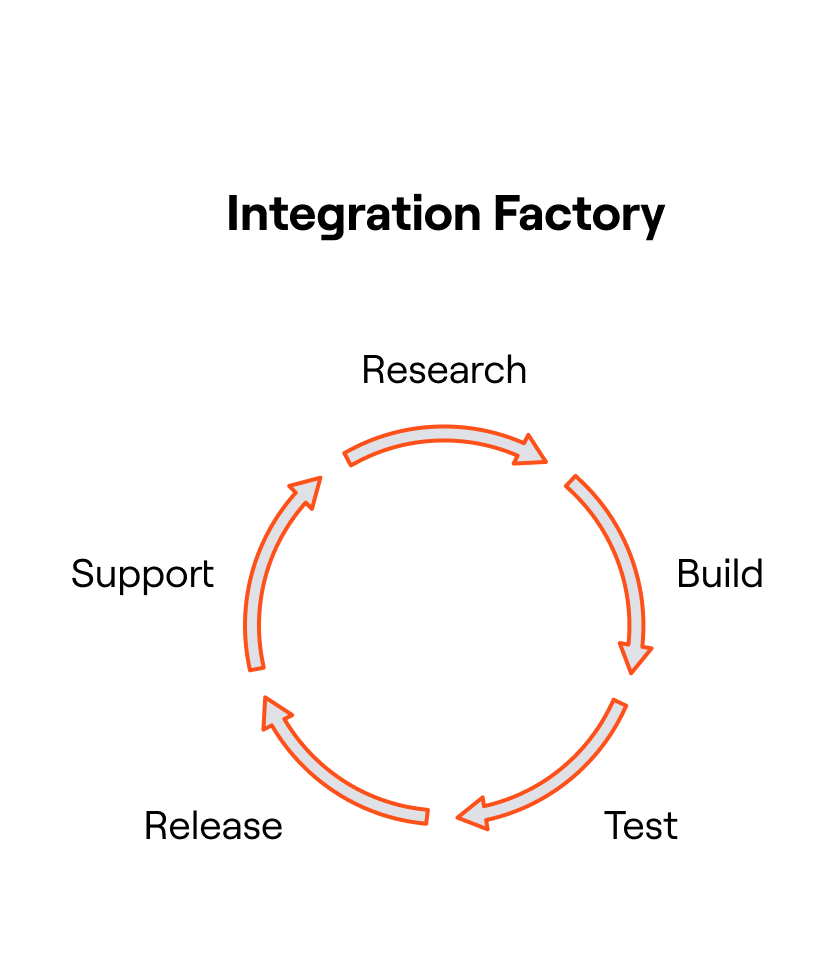
1. Integration Factory
Supporting hundreds of applications – across on-prem, cloud, and hybrid environments – requires turning a chaotic, ad-hoc process into something predictable, repeatable, and scalable. Enter the “Integration Factory". We’ve transformed app integration into a factory-like process, streamlining every phase from idea to deployment:
- Research: We gather the technical details, quirks, and edge cases of each application.
- Build: Using prebuilt authentication modules and standardized components, we create integrations that manage user access and permissions through both read and write connectors.
- Test: Every new integration runs through automated and manual validation cycles.
- Release: With customer-driven roadmaps, we prioritize and deploy what matters most.
- Post-Release Support: We monitor, maintain, and iterate to keep integrations resilient and secure.
Thanks to a library of tested and perfected components, what once took months now takes weeks; or even days. The result? A constantly growing catalog of high-quality integrations built directly around our customers’ needs.
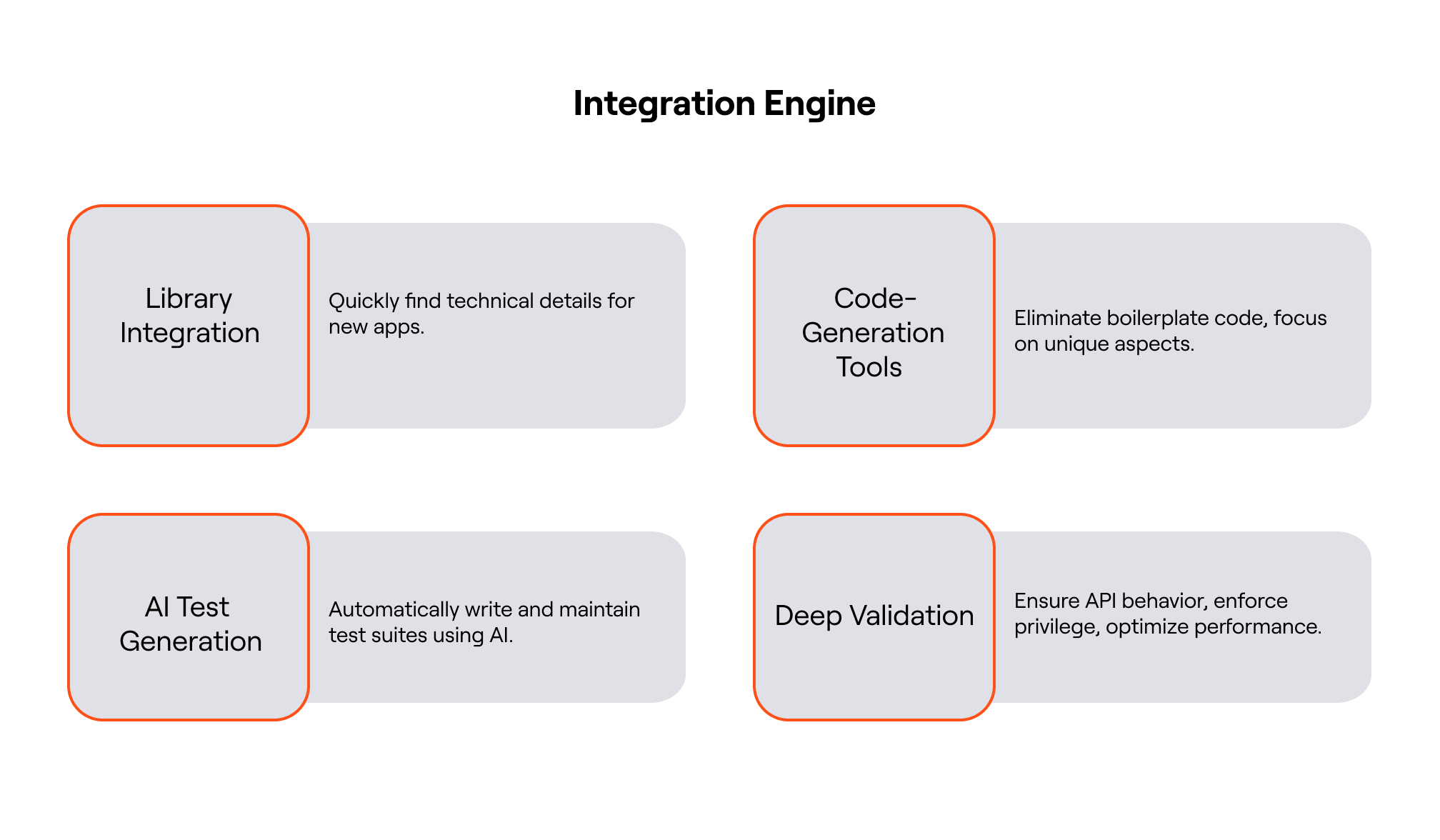
2. Integration Engine
The next framework we use is the “Integration Engine”. The Integration engine is a purpose-built framework that accelerates development, enforces security, and ensures reliability at scale. It combines the following key capabilities:
- Library Integration Research: Our internal systems surface key technical details in record time, cutting down ramp-up for new apps.
- Code-Generation Tools: We eliminate boilerplate and repetitive code, allowing engineers to focus on the unique aspects of each integration.
- AI-Powered Test Generation: We leverage AI to automatically assist and maintain comprehensive test suites, ensuring every integration is validated to the highest standards.
- Deep Validation: We ensure API’s behave as expected, least privilege is enforced and performance is optimized
With the Integration Engine, Lumos ensures every connection is not just fast to build – but deeply secure, rigorously tested, and tailored to scale with your business needs.
What's Different About Our Approach to Integrations?
Speed and flexibility are key defining factors to our integration approach. We ship integrations in days, not weeks, and are able to work with data models from all kinds of systems.
Legacy IGA tools can take weeks and months to build integrations for. Lumos’s out-of-the-box approach with 230+ integrations provides instant time-to-value. Instead of needing to configure and build, we provide integrations that are readily available to use.
For integrations we do not have support for, Lumos is able to quickly spin up connectors. Using scaffolding, automated tools, and context-aware AI, we are able to build deep integrations with provisioning in days not weeks!
Example App : AWS Identity Center
A great example of how Lumos is changing the narrative around integrations is our rich connector for AWS IAM Identity Center.
.png)
This connector makes syncing users, groups, permission sets and accounts easy. But we also take it a step further; and allow provisioning directly into these end systems!
Many of our customers use this integration to directly provision accounts, without going through Okta or any other IDP integration. Gone are the days where an Okta group needs to be configured to grant access to certain permission sets. Use the direct connector and get flexibility into how access is provisioned.
Possibilities with Lumos Integrations
Lumos also supports the ability to develop your own connectors. Many of our customers have used our SDK to build their own connector. With our easy-to-use API’s, customers can build support for any system that does not come out-of-the-box with Lumos. This allows flexibility to model custom business logic.
Custom Connector Capabilities
Users can create integrations that can:
- List Accounts
- List Entitlements / Permissions
- List Access for Accounts
- Provision Access
- Custom Actions
- Downgrade Licenses
- Transfer Resources
Applications can be complex with their authorization and authentication controls. The way those applications are used can add more technical overhead. By allowing developers to build integrations easily, Lumos users get quick time-to-value for custom configurations.
Creating a True Single Control Plane for Identity
Why does all this matter? Historically, connectivity and integrations have been the most critical failure point for IGA projects. Companies manage more identities and permissions across more apps than ever. Yet the cost of integrating apps into legacy IGA tools is so high that most companies never get close to implementing them across all their apps.
More commonly, companies will implement critical apps, like those necessary for SOX compliance, into an IGA tool and leave the rest to ad hoc or manual processes. This might be enough to get you through your audit, but it won’t curb the risk and expense caused by access sprawl, or help you comprehensively enable employees with the right tools. For that, you need a tool that can manage all access.
Lumos’ unique approach to integration allows it to be that tool. Lumos customers manage upwards of 150 apps within months of launching, not years. Only this level of connectivity can form the foundation of Autonomous Identity: the right access, for the right identity, for the right amount of time. Book a demo today to learn more!
















